
Zero Click Warfare: No User Needed Exploits & Zero‑Click Attacks Demystified
Zero Click Warfare: Understanding No‑Click, No‑User‑Needed Exploits Cybercriminals have entered Zero Click Warfare—launching no user needed exploits that require no click and […]
Ransomware in 2024 – What Will Ransomware Attacks in 2025 Look Like?
Ransomware in 2024: A Year of Escalation and Evolution In 2024, ransomware didn’t just knock on the digital doors of businesses—it kicked […]
Securing the Seas Data Breach Delayed Coast Guard Pay: How Warden Could be the Future that Protects the US Coast Guard’s Digital Frontlines from Hacks and Data Breaches
Data Breach Delayed US Coast Guard Pay! Key Points In February 2025, a cyberattack delayed US Coast Guard paychecks for 1,135 members, […]

Top-7 Malware Threats in 2025: What You Need to Know
Top-7 Malware Threats in 2025: What You Need to Know Introduction: Cybersecurity Threats – Malware Predictions for 2025 As we navigate through […]

Hackers See One System as the Attacker — So Should Your Cyber Defenses Not be Compromise
Why Warden and NodeZero Are the Duo You Need to Stop Cyber Threats in Their Tracks The cyber battlefield is ruthless, and […]

Why Small Businesses Must Prioritize Cybersecurity Plans – and How Warden Can Help
Protect Your Small Business: How Warden Defends Against Cyber Threats and Drives ROI Small businesses are increasingly becoming prime targets for cybercriminals […]

2024’s Cybersecurity Battle: Mitigating BianLian Ransomware Group Threats
Understanding BianLian Ransomware New Tactics and Indicators of Compromise Based on the vulnerabilities and risks described, basic attack paths towards compromise and ransomware […]

The Hidden Dangers: The Rise of Bespoke Malware and Ephemeral Infections
In-depth Analysis: Bespoke Malware and Ephemeral Infections What Are Bespoke Malware and Ephemeral Infections? Bespoke malware refers to custom-developed malicious software tailored […]
Global Ransomware Attacks Strike in 52 Seconds: Why Prevention Beats Detection Every Time in this Crisis
Gone in 52 Seconds… The Global Ransomware Crisis and the Case for Warden In 2021 alone, 623.3 million ransomware attempts targeted organizations […]
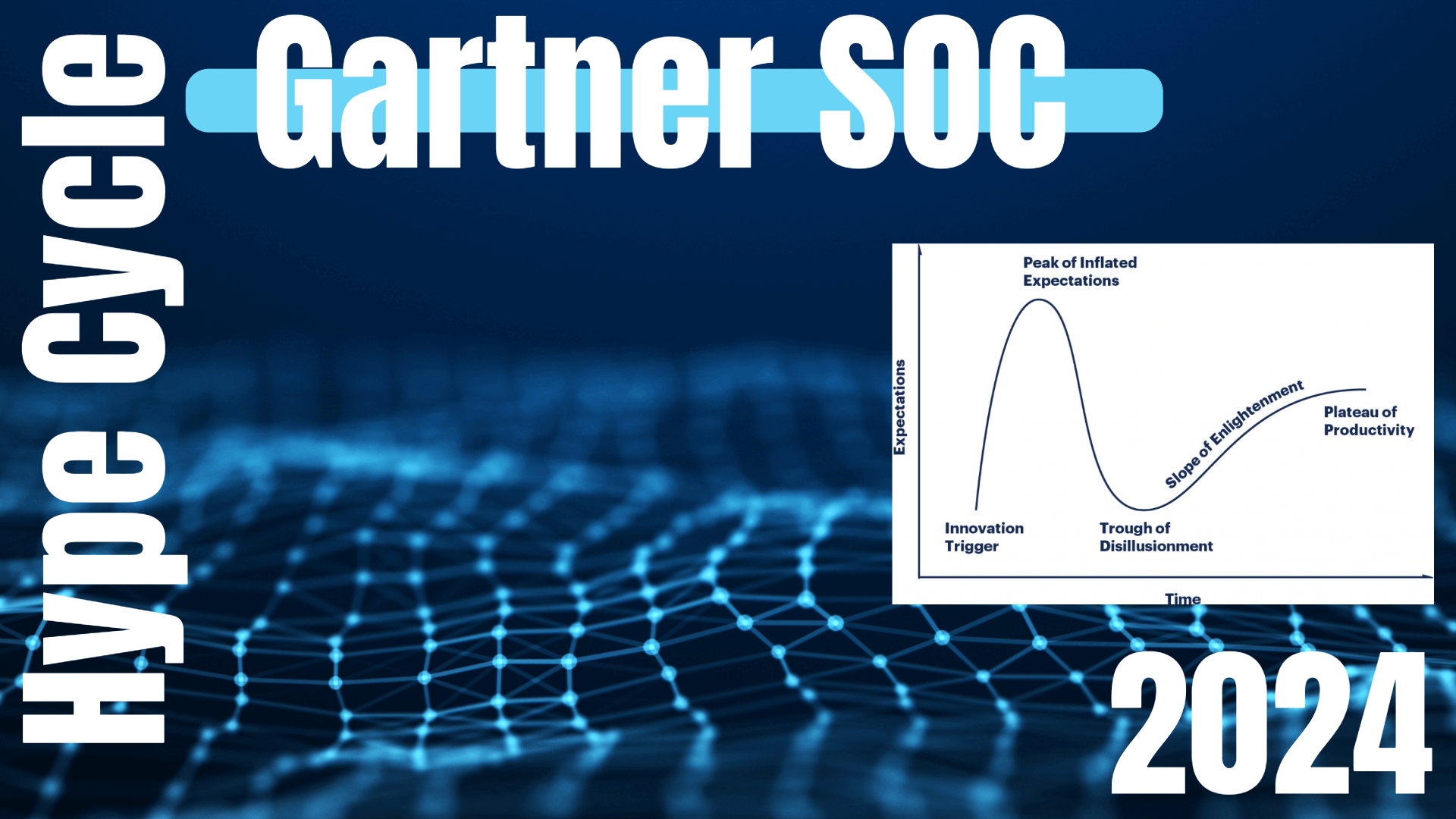
Gartner Analysis of Security Operations Centers (SOCs) in 2024 – Understanding the Hype Cycle™ for Security Operations
The Evolution of Cybersecurity Gartner Analysis of Security Operations Centers (SOCs) in 2024: New Trends, Challenges, and Innovations Gartner Analysis of Security Operations Centers […]

Microsoft States Zero Trust is the Future – Microsoft’s Endorsement is a Game Changer
Microsoft Endorsement for a Zero Trust Strategy As the digital landscape evolves, traditional security models are proving increasingly ineffective at preventing today’s […]

Navigating Zero Trust Security Solutions and Their Boundaries: Tough Questions Every Enterprise Should Ask in order to Implement Zero Trust
Key Considerations for Selecting and Avoiding Common Pitfalls in Implementing Zero Trust Security Solutions In today’s rapidly evolving cybersecurity landscape, Zero Trust […]
