- Ultimate Endpoint Protection for Your Business & Home
Secure your Business & Digital Life with Warden's Zero-Trust Defense against all Known and Unknown Threats.
Cybercrime will cost the world nearly $9.5T in 2024. That is coming from over 73% of businesses facing downtime and revenue lost due to malware in 2022, which has been increasing year over year. This along with all the other advanced criminal threats drives these costs. The problem is that legacy Cybersecurity approaches are not slowing down cybercrime.
Cyber Strategy Institute offers the most complete – and most cost-effective – cyber security for your business available today. You don’t have to break the bank to have peace of mind!

- Ultimate Endpoint Protection for Your Business & Home
Now is the time to take the next step with your business - and protect what you've worked so hard to build.
Cybercrime will cost the world nearly $9.5T in 2024. That is coming from over 73% of businesses facing downtime and revenue lost due to malware in 2022, which has been increasing year over year. This along with all the other advanced criminal threats drives these costs. The problem is that legacy Cybersecurity approaches are not slowing down cybercrime.
Cyber Strategy Institute offers the most complete – and most cost-effective – cyber security for your business available today. You don’t have to break the bank to have peace of mind!

- Stop Criminals from Taking Over
3 Phase Approach to Your Security
It is important to simplify your security and then make it more robust after a new baseline has been established not one based on an old baseline.
Trusted by Top Organizations












- Cybercrime is increasing
Cybercrime's GDP is 2X bigger than the next economy
The criminal under world’s Cybercrime if measured against Nations would be ranked 3rd in the world based on GDP estimated at $8 Trillion.
- Cybersecurity Risks
Your Exposure is greater every day, through Social Media and the DarkWeb!
You are more vulnerable than ever if we include Social Media, Leaked Government information, or compromised corporate data found on the DarkWeb. With AI, it makes it easier than ever to directly target you!
- 3rd Party Data Exposure
- Social Media and Marketing alone Expose Your Business

- Need to move away from our Past
Detection based Cybersecurity is Not Protection.
Detection systems are quickly becoming obsolete, just like keyboards on phones were replaced with touch screens. The new standard in Cybersecurity will be Protection First!
Protection Means
Zero Impact Risk to Threats
- Our Future is at Risk
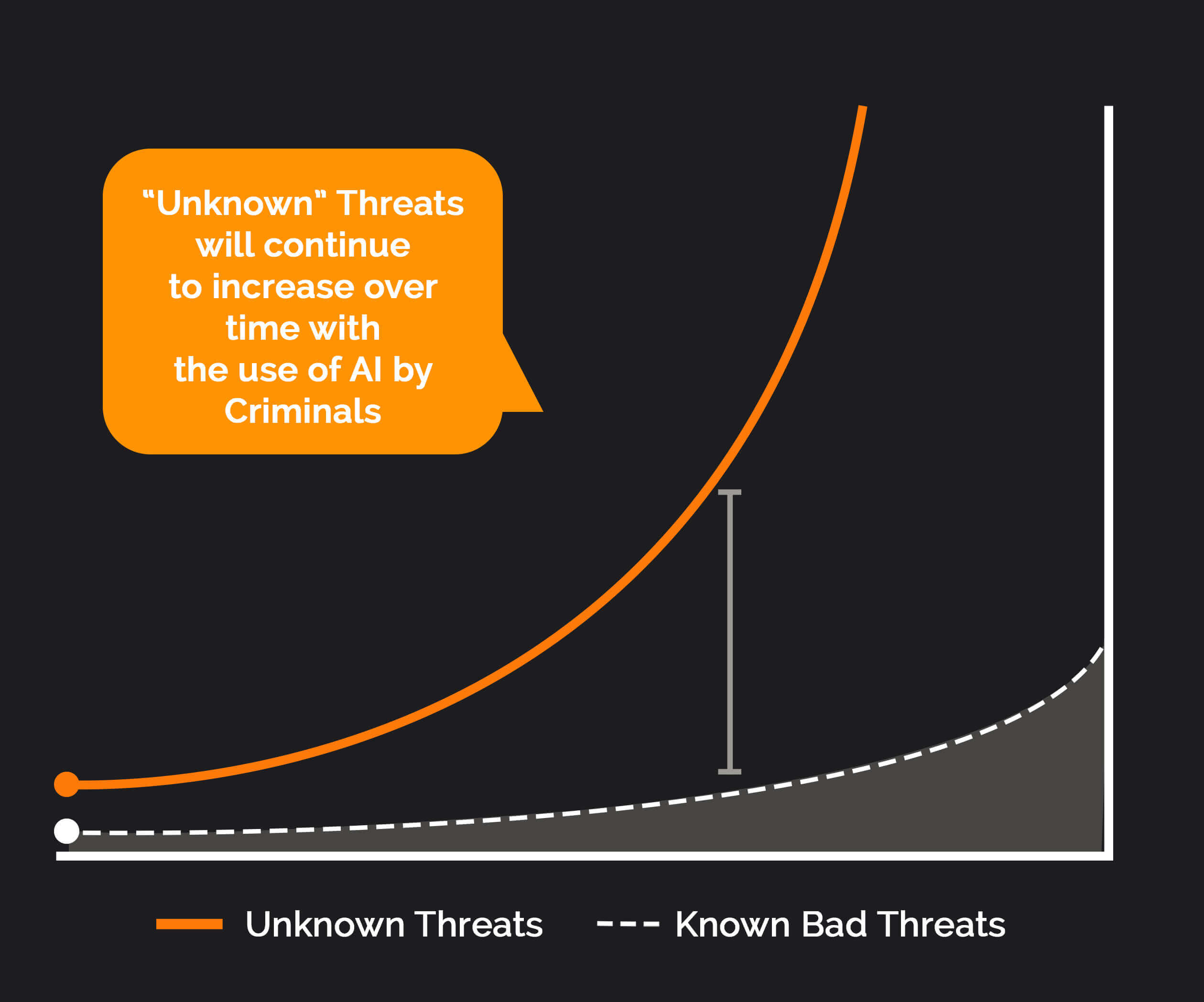
Why is stopping unknown risks so important?
As we go through our lives we make countless decisions. Criminals know this and pray on our brains short cuts to exploit our biases. This is not going to change, their tactics are only going to get harder to spot.
Especially, as they leverage AI to craft better and better tactics they will also create more and more zero-day or unknown malware to target you!
Unique Threats
Unknown Threats

- What True Cybersecurity Looks Like
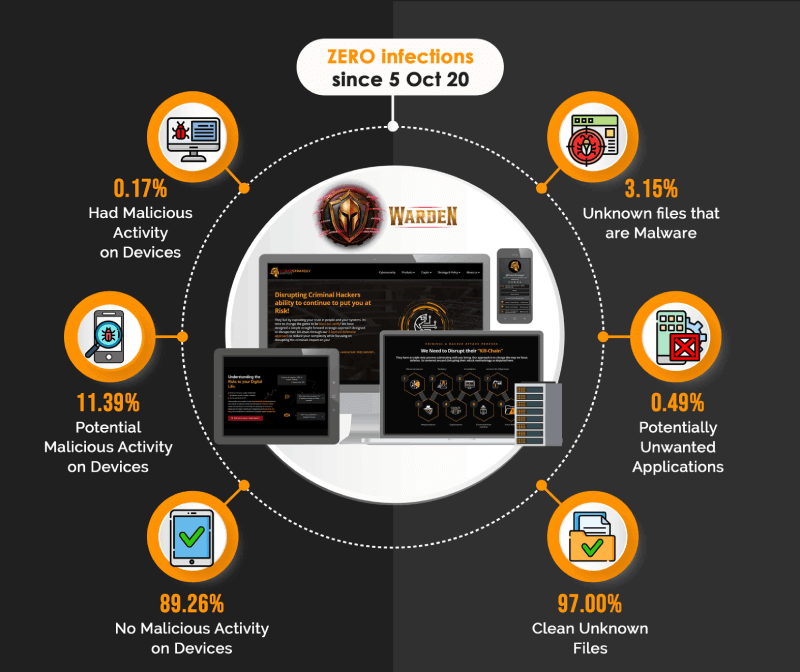
Zero Impact from Known or Unknown Malware Since Oct 2020!
That is correct, an auto-containment system protects your Business and Digital Life from downtime. Warden’s core system, thanks to our Partnership with Xcitium, gives you access to this remarkable system that has ensured Zero businesses have faced downtime due to malware since inception.
- Protected against Downtime from Ransomware, Phishing, Malware, etc
- Professional Team 24x7x365 Ready to Respond & Remediate if Needed
- Save Time and Money while Simplifying Your Complexity