
Embracing the Future: AI Pentesting and Automated Agents in a New Era of Vulnerability Management
Embracing the Future Beyond CVE: AI Pentesting, Automated Agents & the Future of Vulnerability Management As the longstanding CVE framework creaks under the weight […]
Exploiting the Known: The 2024 Surge in Vulnerability Exploitation and Its Impact on Cybersecurity
Exploitation of Vulnerabilities in 2024: An Annual Report of Know Exploited Vulnerabilities In the relentless chess game of cybersecurity, 2024 saw threat […]

The New HIPAA Security Rules: Key Cybersecurity Takeaways and Compliance Solutions
The New HIPAA Cybersecurity Rules: Key Takeaways and Compliance Solutions The Department of Health and Human Services (HHS) has released a draft […]

Hackers See One System as the Attacker — So Should Your Cyber Defenses Not be Compromise
Why Warden and NodeZero Are the Duo You Need to Stop Cyber Threats in Their Tracks The cyber battlefield is ruthless, and […]
Penetration Testing as a Service (PTaaS): Choosing the Right Penetration Testing Service for Your Needs in 2024
Penetration Testing as a Service (PTaaS): A Proactive Approach to Modern Cybersecurity As the digital landscape evolves and cyber threats become more […]

The Role of Adversarial Exposure Validation in 2024: A Key to CTEM Automation
Summary of Role of Adversarial Exposure Validation in CTEM from the 2024 Gartner Hype Cycle: Adversarial exposure validation (AEV) refers to technologies […]
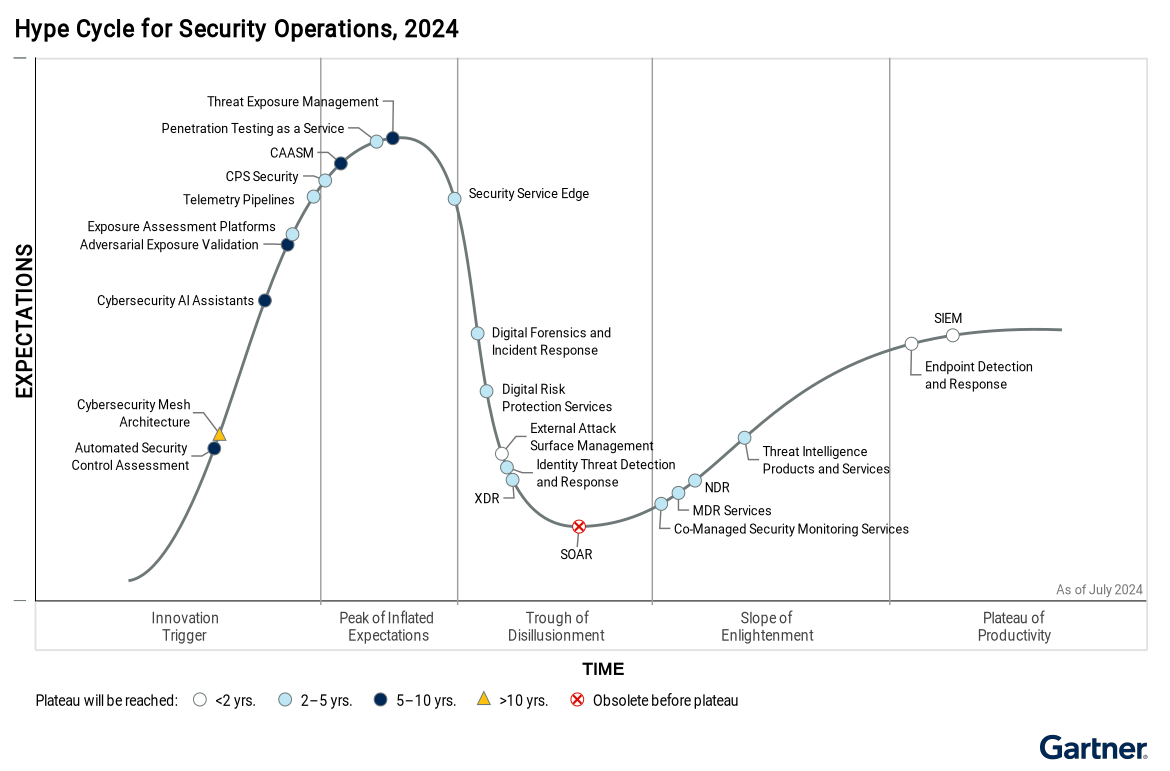
Gartner Analysis of Security Operations Centers (SOCs) in 2024 – Understanding the Hype Cycle™ for Security Operations
The Evolution of Cybersecurity Gartner Analysis of Security Operations Centers (SOCs) in 2024: New Trends, Challenges, and Innovations Gartner Analysis of Security Operations Centers […]

Advanced Pentesting with Horizon3.ai: How NodeZero Tripwires™ Neutralize Attack Vectors
The Cyber Battle You Can’t Afford to Lose: How Pentesting and NodeZero Tripwires™ Can Save Your Network In today’s digital landscape, your […]

The Critical Infrastructure Need for Continuous Pentesting in the Chemical Industry – Cybersecurity in Cross-hairs with CISA Release of Vulnerability Information
Critical Infrastructure Cybersecurity Concern Introduction – Safeguard Industrial Systems The recent CISA incident that exposed the vulnerabilities of 3,200 companies and compromised […]

AI Security — Top 5 Things You Need to Know
In the dynamic landscape of Artificial Intelligence (AI), ensuring robust security measures is paramount as AI becomes our new crown-jewel. The evolving […]

Unraveling Cybersecurity: A Critical Reassessment of Traditional Solutions to Protect Your Company
Unraveling Cybersecurity: Rethinking Traditional Solutions to Protect Your Business Cybersecurity strategies for business continuity are crucial for businesses in today’s landscape, with […]
