
Why Small Businesses Must Prioritize Cybersecurity Plans – and How Warden Can Help
Protect Your Small Business: How Warden Defends Against Cyber Threats and Drives ROI Small businesses are increasingly becoming prime targets for cybercriminals […]

2024’s Cybersecurity Battle: Mitigating BianLian Ransomware Group Threats
Understanding BianLian Ransomware New Tactics and Indicators of Compromise Based on the vulnerabilities and risks described, basic attack paths towards compromise and ransomware […]

The Hidden Dangers: The Rise of Bespoke Malware and Ephemeral Infections
In-depth Analysis: Bespoke Malware and Ephemeral Infections What Are Bespoke Malware and Ephemeral Infections? Bespoke malware refers to custom-developed malicious software tailored […]
Penetration Testing as a Service (PTaaS): Choosing the Right Penetration Testing Service for Your Needs in 2024
Penetration Testing as a Service (PTaaS): A Proactive Approach to Modern Cybersecurity As the digital landscape evolves and cyber threats become more […]

Why are Telemetry Pipelines Are Essential for Modern Data Management and Security?
Optimizing Telemetry Pipelines for Advanced Observability and Security: A Strategic Look into Warden’s Role and Competitive Landscape Telemetry pipelines are essential for […]
Global Ransomware Attacks Strike in 52 Seconds: Why Prevention Beats Detection Every Time in this Crisis
Gone in 52 Seconds… The Global Ransomware Crisis and the Case for Warden In 2021 alone, 623.3 million ransomware attempts targeted organizations […]

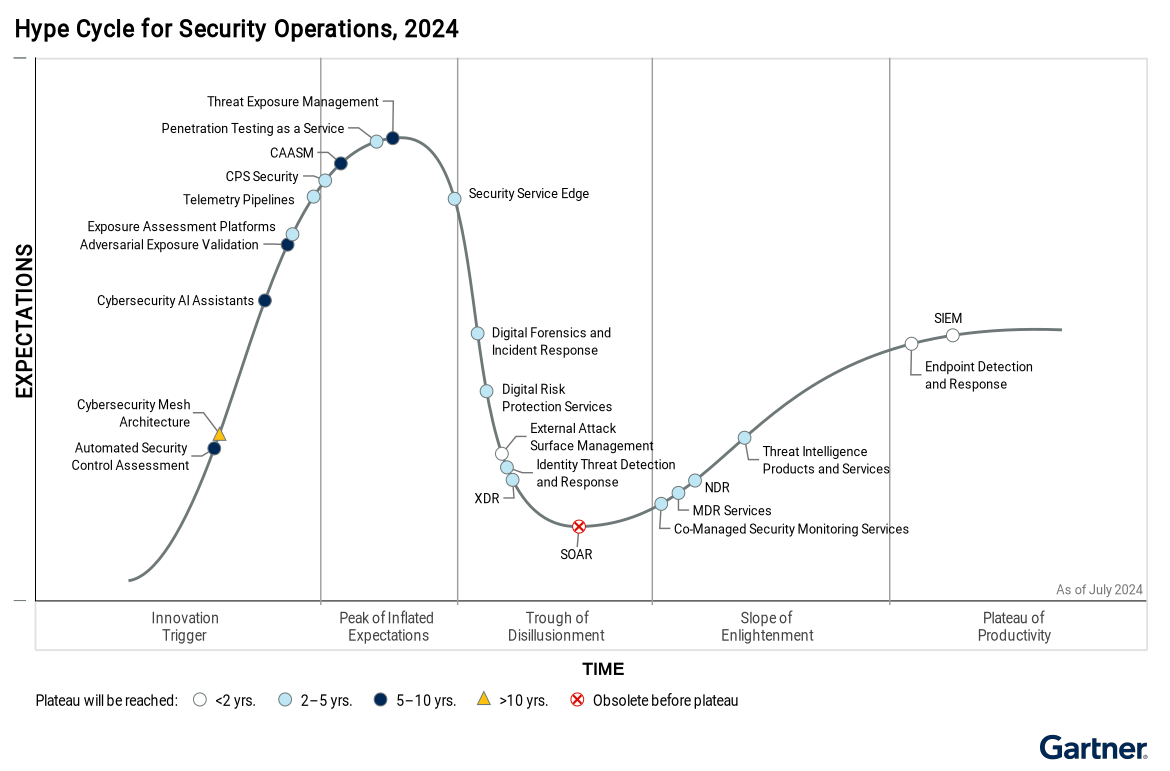
Gartner Analysis of AI-Powered Cybersecurity Assistants: Will Generative AI Assistants Revolutionize Cybersecurity?
The Role of Cybersecurity AI Assistants: An In-Depth Analysis of Gartner’s 2024 Hype Cycle Cybersecurity AI assistants are on the brink of […]

Why Automated Security Control Assessment (ASCA) Is the Key to Unlocking Your Cyber Resilience in 2024
The Future of Automated Security Control Assessment (ASCA): Filling the Gaps in Gartner’s Hype Cycle In 2024, Gartner highlighted Automated Security Control […]
Cybersecurity in Healthcare Merger and Acquisition (M&A): Managing Risks to Ensure Successful M&A Integration and ROI
The Critical Importance of Due Diligence in Healthcare M&A: Safeguarding IT Assets and Mitigating Cybersecurity Risks As healthcare systems increasingly pursue mergers […]

Microsoft States Zero Trust is the Future – Microsoft’s Endorsement is a Game Changer
Microsoft Endorsement for a Zero Trust Strategy As the digital landscape evolves, traditional security models are proving increasingly ineffective at preventing today’s […]

How to Calculate the Cost of Downtime from IT to Cybersecurity Breach: A Complete Guide for 2024 on the True Cost of Downtime
The True Cost of Downtime and Data Breaches in 2024: What Small Businesses Need to Know In today’s fast-paced digital world, nothing […]

Ethical Dilemmas in Pentagon Cyberdefense a Case Study: Why Did HP Enterprise Let Russia Scrutinize ArcSight?
HP Enterprise Allowed a Russian Defense Agency to Review ArcSight Cybersecurity Software Used by the Pentagon – Why? Why did Hewlett Packard […]
