🚨 The Truth About EDR Bypass: Why Your EDRs / Endpoint Security Tools Are Failing
EDRs Aren’t Stopping RATs: A Data-Driven Reality Based on 50,000 Pentests and a Look at Warden’s Next-Generation Defense Modern security teams invest […]

The New HIPAA Security Rules: Key Cybersecurity Takeaways and Compliance Solutions
The New HIPAA Cybersecurity Rules: Key Takeaways and Compliance Solutions The Department of Health and Human Services (HHS) has released a draft […]

Hackers See One System as the Attacker — So Should Your Cyber Defenses Not be Compromise
Why Warden and NodeZero Are the Duo You Need to Stop Cyber Threats in Their Tracks The cyber battlefield is ruthless, and […]

The Clock is Ticking: Why CEOs and CISOs Can No Longer Afford to Ignore Cybersecurity Risks
The Most Dangerous Hour: Why CEOs and CISOs Can No Longer Afford to Ignore Cybersecurity Risks In today’s high-stakes cybersecurity environment, ignorance […]
1.1 TB Stolen of Slack Data: A Step-by-Step Breakdown of the Disney Data Breach and How to Prevent It
How the 1.1 TB Disney Slack Data Breach Could Have Been Prevented with Warden and NodeZero Earlier this year, attackers stole 1.1 […]
Warden CNAPP Defense: Redefining Runtime and Beyond for Cloud-Native Application Protection Platform
Why Warden Outpaces Wiz and Others in CNAPP Innovation A deep dive into Warden’s capabilities and why it’s ahead of the CNAPP […]

Why Small Businesses Must Prioritize Cybersecurity Plans – and How Warden Can Help
Protect Your Small Business: How Warden Defends Against Cyber Threats and Drives ROI Small businesses are increasingly becoming prime targets for cybercriminals […]
Penetration Testing as a Service (PTaaS): Choosing the Right Penetration Testing Service for Your Needs in 2024
Penetration Testing as a Service (PTaaS): A Proactive Approach to Modern Cybersecurity As the digital landscape evolves and cyber threats become more […]

Understanding CPS: How Cyber-Physical Systems Connect the Digital and Cyber Physical System Worlds
2024 Cyber-Physical Systems (CPS) Security: A Comprehensive Analysis and Future Outlook In our technologically advanced era, Cyber-Physical Systems (CPS)—engineered to bridge digital […]

Why are Telemetry Pipelines Are Essential for Modern Data Management and Security?
Optimizing Telemetry Pipelines for Advanced Observability and Security: A Strategic Look into Warden’s Role and Competitive Landscape Telemetry pipelines are essential for […]

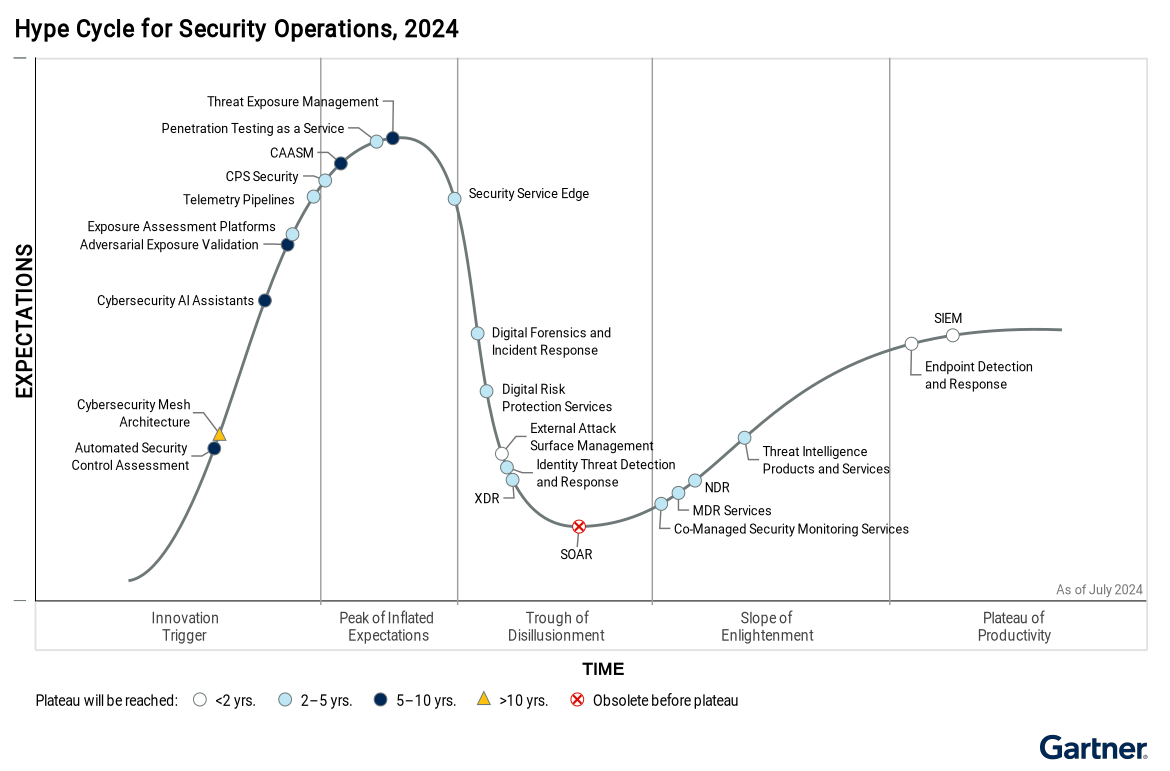
The Role of Adversarial Exposure Validation in 2024: A Key to CTEM Automation
Summary of Role of Adversarial Exposure Validation in CTEM from the 2024 Gartner Hype Cycle: Adversarial exposure validation (AEV) refers to technologies […]

Gartner Analysis of AI-Powered Cybersecurity Assistants: Will Generative AI Assistants Revolutionize Cybersecurity?
The Role of Cybersecurity AI Assistants: An In-Depth Analysis of Gartner’s 2024 Hype Cycle Cybersecurity AI assistants are on the brink of […]
