Sophisticated Web3 Gaming Scammers

Rogue Realms: How Sophisticated Scammers are Exploiting Web3 Gaming
Cybersecurity Techniques Framework:
The comprehensive framework offers strategies for Web3 players to protect against scams and malware. Covering software updates, reputable endpoint defense, verified downloads, and two-factor authentication, it emphasizes education and staying informed about evolving threats. The framework also introduces Warden as a zero-impact, zero-trust cybersecurity solution. The engagement section outlines cautious methods for identifying scams during interactions, urging players to trust their instincts and prioritize safety. Remember to incorporate these practices to ensure a secure and enjoyable Web3 Gaming experience.

Web3Gaming Scammers “How-to” Framework
First off, let’s look at a couple of case-studies of scammers using the Web3Gaming space as a front to steal players assets.
Article 1: Guardians of Throne Scam

Embark on a gripping journey into the underbelly of Web3 gaming, where unsuspecting players face a perilous dance with cybercriminals. In the first installment, “Guardians of Throne Scam,” we unmask a sophisticated plot that ensnares Web3 enthusiasts through an intricately fabricated game. Imagine a virtual world that beckons, yet conceals a malevolent secret — this is the world of “Guardians of Throne.” This exposé unveils a saga of deception, from the deceptive allure of the game to the sinister machinations of the RedLine Stealer malware lurking within. The author’s harrowing account traverses the deceptive landscapes of Twitter, Telegram, and Discord, revealing the scam’s elaborate façade, leaving readers on the edge of their seats. Brace yourself for an exploration of the dark side of Web3 gaming scammers, where every click holds the potential for peril.
Lessons Learned:
1. Scammers are becoming more sophisticated in the Web3 gaming space.
2. Fake games may use various platforms, including Twitter, Discord, and Telegram, to lure victims.
3. Scammers create an elaborate facade, including websites and social media accounts, to make their schemes appear legitimate.
4. Always verify the legitimacy of gaming opportunities, especially those offering ambassador roles.
5. Be cautious of unexpected offers and suspicious behavior, and prioritize cybersecurity measures to avoid falling victim to scams.
Article 2: Blast Royale Impersonation Scam

This article delves into a scam targeting Web3 gamers, mimicking the legitimate game “Blast Royale.” The scammer’s tactics include crafting a fake website and social media presence, enticing players to download the RedLine Stealer malware. The scam unfolds through deceptive outreach on Twitter, Discord, and Telegram, offering early access to the game. The author introduces the cybersecurity service “Warden” as a defense against such threats. Lessons highlight the lucrative nature of Web3 gaming for scammers, the mimicking of legitimate games, and the critical role of advanced cybersecurity tools. Additional insights provide a checklist for identifying scams, covering aspects from website details to requests for turning off security measures.
Lessons Learned:
1. Web3 gaming is a lucrative target for scammers due to increased funding and popularity.
2. Scammers mimic legitimate games, change names, and exploit poor security practices to deceive players.
3. Recognizing red flags, such as suspicious social media accounts and misleading timelines, is crucial in avoiding scams.
4. Scammers use social engineering tactics, including DMs and promises of exclusive access, to manipulate victims.
5. Advanced cybersecurity tools like Warden, which blocks known and unknown malicious files, are essential for robust defense against scams.
Additional Lessons Learned to Identify Scammers:

1. Timeline Discrepancies:
– Scammers may create fake timelines or histories for their projects. In both cases, checking the registration date of the website domain and cross-referencing it with claimed launch dates can reveal inconsistencies.
2. Incomplete or Suspicious Social Media Presence:
– A legitimate project typically has a comprehensive and consistent social media presence. Incomplete profiles, missing links, or limited interaction on platforms like Twitter, Discord, or Telegram could be red flags.
3. Unusual Website Details:
– Genuine projects usually have detailed and well-organized websites. Look out for poorly designed sites, missing information, or discrepancies in content that could indicate a scam.
4. Fake Gitbooks and Documentation:
– Scammers might copy existing documentation, such as Gitbooks, with minimal changes. Always verify the authenticity of documents and cross-reference them with official sources.
5. Overemphasis on Urgency:
– Scammers often create a sense of urgency to pressure potential victims into taking immediate action. Be cautious if a project insists on quick decisions, especially regarding downloads or providing personal information.
6. Use of Multiple Platforms:
– Scammers may operate across various platforms to appear legitimate. If a project contacts you on one platform and asks you to move to another, especially for crucial steps, exercise caution.
7. Requests to Turn off Security Measures:
– Legitimate software or games should not require users to disable antivirus or security measures during installation. Any such request is a clear sign of potential malicious intent.
8. Unrealistic Offers:
– Scammers often entice victims with too-good-to-be-true offers, such as high-paying gigs or exclusive opportunities. Be skeptical of offers that seem overly generous, especially if they require personal information or downloads.
9. Third-Party Verification:
– Engaging with the community and seeking third-party verification can help expose scams. If others have encountered similar issues or doubts, it’s a signal to exercise caution.
10. Cross-Check with Official Channels:
– Verify the legitimacy of a project by cross-checking information with official channels such as Discord servers, Twitter profiles, or the project’s website. Legitimate projects are likely to have a consistent and established online presence.
11. Avoiding Unnecessary Downloads:
– Be cautious about downloading files or executables from unverified sources. Always ensure that the download is from the official and reputable channels associated with the game or project.
12. Educate Yourself on Scams:
– Regularly update your knowledge on common scam tactics. Understanding the evolving strategies scammers use can better prepare you to identify and avoid potential threats in the gaming space.
By incorporating these additional lessons into their awareness, players can enhance their ability to identify and protect themselves from scams in the dynamic and evolving Web3 gaming landscape.
Cybersecurity Techniques to Protect Against Scammers and Malware:

Framework Checklist for Reducing Risks
1. Keep Software Updated:
– Regularly update your operating system, antivirus software, and gaming applications. Software updates often include security patches that protect against known vulnerabilities.
2. Use Reputable Endpoint Defense aka Antivirus Software:
– Install and use reputable antivirus and antimalware software. Ensure that it is regularly updated and configured to perform real-time scans on your system.
BONUS: Checkout the only capability to have had Zero Impacts since 5 Oct 2020 to present and is Zero-Trust enabled out-of-the-box! Warden, stops all known bad and unknown files from directly impacting your system. Prevent Breaches, Theft, Ransomware, Exploits, Malware, Email Phishing, Spyware, etc…before they can impact your Digital Life!
3. Verify Downloads:
– Only download games, applications, or files from official and reputable sources. Avoid third-party websites or links shared through social media, especially if they are unsolicited.
4. Enable Two-Factor Authentication (2FA):
– Implement 2FA wherever possible, especially on gaming platforms and associated accounts. This adds an extra layer of security and makes it more difficult for scammers to gain unauthorized access.
5. Educate Yourself:
– Stay informed about common cybersecurity threats and scams. Understanding how scammers operate can help you recognize and avoid potential risks.
6. Use Strong and Unique Passwords:
– Create strong, unique passwords for your gaming accounts. Avoid using the same password across multiple platforms, and consider using a password manager to help generate and store complex passwords.
7. Beware of Phishing Attempts:
– Be cautious of unsolicited messages, especially those containing links or attachments. Avoid clicking on suspicious links, and verify the legitimacy of messages before taking any action.
8. Check Website Security:
– Before providing any personal information or downloading files, check the security of the website. Look for “https://” in the URL and a padlock symbol, indicating a secure connection.
9. Monitor Account Activity:
– Regularly review your gaming account activity for any unauthorized access or suspicious transactions. Report any anomalies to the platform’s support team.
10. Secure Your Home Network:
– Ensure your home Wi-Fi network is secure by using strong encryption and a unique password. Regularly update your router firmware to address potential security vulnerabilities.
11. Be Skeptical of Unsolicited Offers:
– If you receive unsolicited offers, especially those promising high returns or exclusive opportunities, approach them with skepticism. Verify the legitimacy of the offer through official channels.
12. Limit Personal Information Sharing:
– Avoid sharing unnecessary personal information on gaming platforms and social media. Scammers often use this information for targeted attacks.
13. Stay Informed about Scams:
– Keep yourself updated on the latest scams and cybersecurity threats related to the gaming community. Online forums and official announcements from gaming platforms can be valuable sources of information.
14. Network Security:
– Use a firewall to monitor and control incoming and outgoing network traffic. Configure the firewall to block unauthorized access and communication.
15. Regular Backups:
– Regularly backup your important gaming data and files. In the event of a malware attack, having backups ensures that you can recover your data without paying ransom fees.
By incorporating this comprehensive cybersecurity techniques framework into their practices, Web3 players can navigate the Web3 Gaming world with increased awareness and resilience against potential scams and significantly reduce the risk of falling victim to scammers and malware in the Web3 gaming environment. Staying vigilant and proactive in cybersecurity practices is crucial for a safe and enjoyable gaming experience.
Engaging with a potential scammer in chats can be risky, but if you choose to do so for investigative purposes, here are some methods to help identify red flags and potential signs of a scam:
Identifying Red Flags during Engagement

1. Ask Detailed Questions:
– Inquire about specific details regarding the game, project, or opportunity. Scammers may struggle to provide coherent and accurate information.
2. Verify Information:
– Cross-check the information provided by the scammer with official channels, such as the game’s website, social media profiles, or reputable forums. Legitimate projects should have consistent and accurate information.
3. Request Proof or Documentation:
– Ask for proof of legitimacy, such as official documentation, contracts, or endorsements. Scammers may avoid providing concrete evidence.
4. Test Their Knowledge:
– Assess the scammer’s knowledge of the gaming industry and related technologies. Genuine representatives would have a deeper understanding, while scammers may struggle to answer technical questions.
5. Check for Unusual Grammar and Language:
– Pay attention to the language used in communications. Scammers may exhibit poor grammar, spelling mistakes, or use generic phrases. Legitimate representatives typically maintain professional communication.
6. Look for Urgency or Pressure Tactics:
– Scammers often use urgency to pressure victims into quick decisions. If the scammer is pushing for immediate actions, it could be a sign of a scam.
7. Request a Video Call or Meeting:
– Propose a video call or meeting to discuss the opportunity further. Scammers may hesitate or find excuses to avoid face-to-face interactions.
8. Check Online Presence:
– Examine the scammer’s online presence on platforms like Twitter, Discord, or Telegram. Look for inconsistencies, low activity, or suspicious follower patterns.
9. Research Similar Scams:
– Investigate similar scams reported by others in online forums or social media. Patterns of behavior or tactics may emerge that align with your interactions.
10. Be Cautious of High Returns or Gains:
– If the opportunity promises exceptionally high returns or gains, exercise caution. Unrealistic promises are often indicative of scams.
11. Request References or Testimonials:
– Ask for references or testimonials from other individuals who have participated in the opportunity. Scammers may struggle to provide credible references.
12. Use a Virtual Machine for Testing:
– If you’re testing potentially malicious files or software, consider using a virtual machine for isolation. This can protect your primary system from potential harm.
13. Monitor Their Reactions:
– Pay attention to how the scammer reacts to your questions and requests. Defensive or evasive responses may indicate deceit.
14. Consult with Trusted Contacts:
– Reach out to friends, colleagues, or trusted contacts to inquire if they have any knowledge or experience with the project or individuals involved.
15. Trust Your Instincts:
- If something feels off or too good to be true, trust your instincts. Scammers rely on exploiting emotions, and if the situation raises doubts, it’s wise to proceed with caution or disengage.
Remember that engaging with scammers carries risks, and it’s essential to prioritize your safety and the security of your information. If you suspect a scam, report it to the relevant authorities or platform administrators.
Warden Zero Impacts
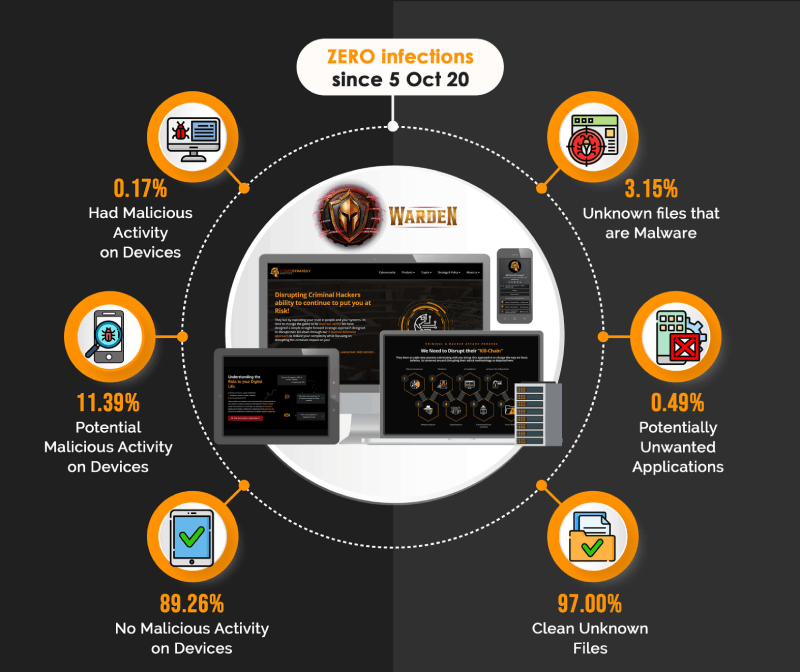
Again, Checkout the only capability to have had Zero Impacts since 5 Oct 2020 to present and is Zero-Trust enabled out-of-the-box! Warden, stops all known bad and unknown files from directly impacting your system. Prevent Breaches, Theft, Ransomware, Exploits, Malware, Email Phishing, Spyware, etc…before they can impact your Digital Life!





