Top Crypto Scams and How to Avoid Them
The world of cryptocurrency is exhilarating, full of immense potential and groundbreaking innovations. As a crypto native who has been deeply immersed in this space for years, I’ve witnessed the transformative power of digital currencies. However, I’ve also seen the dark side: the relentless tide of crypto scams that prey on the unsuspecting and the unprepared. I’ve personally fallen victim to these scams, losing hard-earned money to fraudsters who exploit the trust and enthusiasm of individuals eager to invest in the crypto market. I say this so you understand that even those that have decades of knowledge, skills and abilities in cybersecurity are at risk in this space. Its why in the end, our objective is to reduce your risks. These experiences, though painful, have driven me to understand these threats thoroughly and to help others avoid similar fates.
Reducing risk is paramount in the crypto world. The excitement of new projects, the promise of high returns, and the rapid evolution of technology can sometimes blind us to the dangers lurking in the shadows. This guide is designed to be a comprehensive resource for you, the reader, to navigate the myriad of risks you might face. It’s not just about protecting your investments—it’s about equipping you with the knowledge to help others before they become victims of cryptocurrency scams. By being precise and thorough, we can collectively reduce the prevalence of these scams and create a safer environment for everyone involved in the crypto ecosystem. Trust is built on shared experiences and transparent information, and through this guide, I aim to foster both.
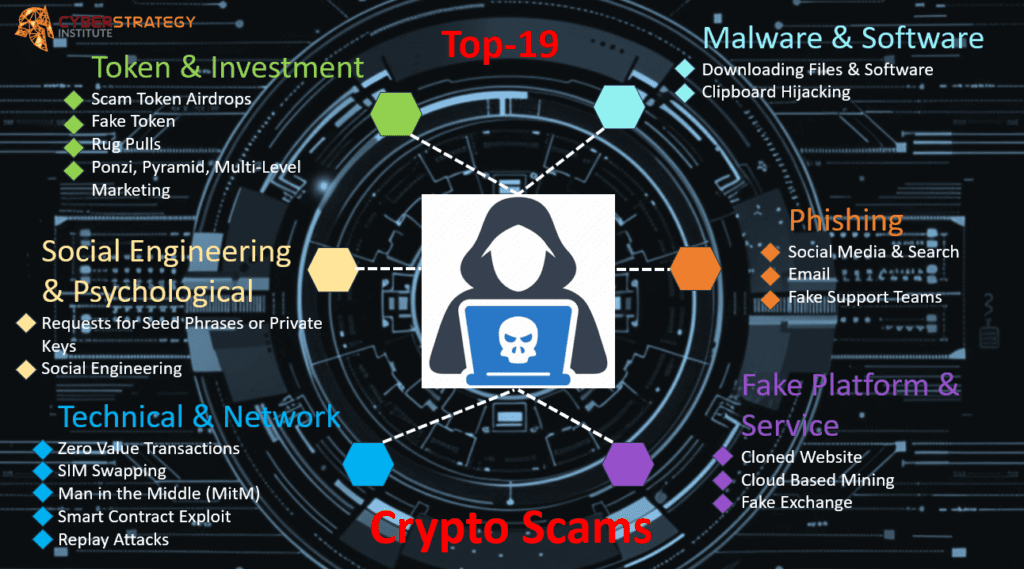
Phishing Scams
Phishing on Social Media and Search Engines
- Twitter: Highly skilled hackers use AI to create fake Twitter pages that mimic real ones, including posts and comments. These accounts often have verified badges and subtly altered names. There are several strategies, the ads approach, commenting under an official post or directly to a follower that asks a specific type of question. So double check their profile names against the real one. Because the last thing we want to do is click on links in these posts that will lead us to sites where connecting your wallet results in losing your crypto assets.
- Telegram: Scammers are watching all the projects channels, looking for folks in need of help. They mimic project mods accounts, even the founders and DM followers in the hopes of learning something sensitive that they can exploit. We recommend creating folders and using them, so you miss random DMs.
- Discord: Scammers disguise malicious links to look normal. Always verify links in the address bar and cross-check with official sources. Even from the team, as Discord servers get compromised all the time, in 2022 over 700 servers were hacked and sent fake links to the community as “team” members. So triple checking in multi channels is important.
- Google Search: Scammers buy ads on Google, making their fake sites appear at the top of search results. These ads can lead to phishing sites that look like legitimate crypto services. We recommend never clicking on ads in Google search results, you want to look for the actual page.
Countermeasures:
- Never click on links from unsolicited messages or ads.
- Double-check URLs and use official channels to verify information.
- Use browser extensions that block malicious sites and provide phishing alerts.
- Avoid clicking on Ads on Twitter/X and Google
- In Telegram use Folders, organize who you follow into different folders
Keys to Identifying Threats:
- Look for subtle changes in URLs or usernames.
- Double check the accounts name, its spelling matters
- erify account authenticity by checking for inconsistencies.
- Use official websites and sources for accessing services.
Email Scams
- Scammers send fake emails to collect private data from users, often impersonating trusted entities to gain access to sensitive information like private keys.
Countermeasures:
- Verify the sender’s email address.
- Avoid clicking on links or downloading attachments from unknown senders.
- Use email security features like spam filters and two-factor authentication.
Keys to Identifying Threats:
- Look for grammatical errors and unusual email addresses.
- Verify suspicious emails through official channels.
- Avoid providing personal information through email links.
Fake Support Teams
- Scammers pretend to be support teams from companies like MetaMask on social media platforms, aiming to access private and sensitive information like crypto wallet keys.
Countermeasures:
- Contact support only through official channels.
- Never share private keys or passwords with anyone.
- Verify the identity of support personnel through multiple channels.
Keys to Identifying Threats:
- Be cautious of unsolicited support messages.
- Verify support requests through the company’s official website.
- Avoid engaging with support personnel on unofficial platforms.
Malware and Software Scams
Downloading Files or Software
- Downloading a file, game, or software from untrusted sources can be disastrous. Modern viruses are sophisticated and can drain your crypto assets once installed.
Countermeasures:
- Use reputable antivirus software.
- Avoid downloading files from unknown or suspicious sources.
- Regularly update your software and security patches.
Keys to Identifying Threats:
- Be wary of too-good-to-be-true offers for free software.
- Check reviews and ratings of the source website.
- Use security tools to scan downloads before opening them.
Clipboard Hijacking
- Malware that monitors your clipboard can replace copied crypto addresses with attackers’ addresses.
Countermeasures:
- Verify addresses before sending transactions.
- Use anti-malware software.
Keys to Identifying Threats:
- Notice any unexpected changes in copied data.
- Use security software to detect and prevent clipboard hijacking.
Social Engineering and Psychological Scams
Requests for Seed Phrases or Private Keys
- Never share your seed phrase or private key. Scammers might request these through fake websites, software, or phishing attacks.
Countermeasures:
- Keep your seed phrase and private keys secure and offline.
- Use hardware wallets for added security.
- Educate yourself about safe crypto practices.
Keys to Identifying Threats:
- Recognize that no legitimate service will ask for your private keys.
- Avoid entering sensitive information on suspicious sites.
- Verify any requests through multiple official channels.
Social Engineering
- Scammers use psychological tactics to trick you into believing in a fake site, program, or person.
Countermeasures:
- Always be skeptical and verify the legitimacy of any offer or request.
- Don’t fall for emotional manipulation or urgency tactics.
- Educate yourself on common social engineering techniques.
Keys to Identifying Threats:
- Recognize and resist pressure tactics.
- Verify requests through multiple channels.
- Be cautious of unsolicited messages and offers.
Token and Investment Scams
Scam Token Airdrops
- Scam tokens can trigger smart contracts that drain your wallet or direct you to scam sites.
Countermeasures:
- Ignore unsolicited tokens and never engage with them.
- Use wallet settings to hide unwanted tokens.
- Verify any airdrop details through trusted sources.
Keys to Identifying Threats:
- Question the legitimacy of unsolicited airdrops.
- Cross-check airdrop announcements with official project communications.
- Avoid interacting with unknown tokens.
Fake Tokens
- Always verify the smart contract address of any token you are dealing with. Fake tokens can appear identical to real ones but are worthless.
Countermeasures:
- Use trusted platforms like Etherscan or CoinGecko to verify token contracts.
- Avoid trading tokens with unknown or suspicious origins.
- Research token projects thoroughly before investing.
Keys to Identifying Threats:
- Look for inconsistencies in token contract addresses.
- Use official project websites and trusted resources for information.
- Avoid newly created tokens without a clear and legitimate history.
Cryptocurrency Scam Rug Pulls
- Fraudulent projects amass investments before disappearing with all funds.
Countermeasures:
- Research projects thoroughly before investing.
- Look for audits and community trust indicators.
- Diversify investments to mitigate risks.
Keys to Identifying Threats:
- Be wary of projects with unrealistic promises.
- Check for transparent development and community engagement.
- Avoid investing in projects without clear use cases or roadmaps.
Ponzi, Pyramid, and MLM Schemes
- These schemes focus on generating revenue by making new investors pay for compromised tokens with older investors, creating liquidity for them to exit.
Countermeasures:
- Research the project’s business model and revenue sources.
- Avoid projects that emphasize recruitment over product or service value.
- Look for regulatory warnings and legal issues associated with the project.
Keys to Identifying Threats:
- Be cautious of projects promising high returns with little risk.
- Verify the legitimacy and transparency of the project’s operations.
- Avoid schemes that require continuous recruitment to sustain.
Technical and Network Scams
Zero-Value Transactions
- Scammers can send tiny transactions to your wallet with addresses that look similar to yours, hoping you’ll copy and send assets to their address by mistake.
Countermeasures:
- Always copy and paste addresses carefully.
- Double-check every character before sending any transaction.
- Use wallet address management tools to avoid errors.
Keys to Identifying Threats:
- Be vigilant about transaction details.
- Use transaction tracking tools to monitor for suspicious activity.
- Report and block suspicious addresses.
SIM Swapping Fraud
- Attackers hijack phone numbers through SIM swaps, bypassing 2FA and accessing exchange accounts.
Countermeasures:
- Secure your phone number and consider using additional authentication methods.
- Use apps and services that offer alternative 2FA methods like authentication apps or hardware tokens.
Keys to Identifying Threats:
- Monitor your phone account for unusual activity.
- Use strong, unique passwords for online accounts.
- Avoid sharing personal information that could aid in a SIM swap.
Man-in-the-Middle (MitM) Attacks
- Public Wi-Fi networks can be exploited to redirect transactions to attackers’ wallets.
Countermeasures:
- Avoid using public Wi-Fi for sensitive transactions.
- Use VPNs to secure your internet connection.
- Verify transaction details carefully.
Keys to Identifying Threats:
- Be cautious of public Wi-Fi networks.
- Monitor network connections for suspicious activity.
- Use encryption to protect data transmissions.
Smart Contract Exploit Scammers
- Vulnerabilities in smart contracts can lead to significant losses, as seen with the “ChainLock” DeFi platform exploit.
Countermeasures:
- Ensure smart contracts are audited before use.
- Use trusted platforms and contracts with proven security records.
- Stay updated on security practices and exploit reports.
Keys to Identifying Threats:
- Check for audit reports from reputable firms.
- Monitor smart contract interactions for anomalies.
- Stay informed about known vulnerabilities and exploits.
Replay Attacks
- Attackers intercept and resend valid data transmissions, duplicating transactions.
Countermeasures:
- Implement replay protection and stay updated on network security patches.
- Use secure communication channels.
- Regularly update software and security protocols.
Keys to Identifying Threats:
- Be aware of network security alerts and updates.
- Monitor transactions for unusual duplications.
- Use security features provided by platforms and wallets.
Fake Platforms and Services
Cloned Websites
- Scammers create cloned websites that look identical to legitimate ones, aiming to steal assets and private keys.
Countermeasures:
- Always type the URL directly into your browser.
- Use bookmarks for frequently visited sites.
- Look for security certificates and signs of legitimacy.
Keys to Identifying Threats:
- Verify site URLs and security indicators.
- Avoid clicking on links from emails or messages.
- Use browser extensions that detect cloned sites.
Cloud-Based Mining Scams
- These scams ask people to sign contracts and invest in bitcoin or other major altcoin mining data centers, which are hard to verify.
Countermeasures:
- Research the company thoroughly before investing.
- Look for reviews and independent analysis.
- Verify the physical existence and legitimacy of the mining operation.
Keys to Identifying Threats:
- Be skeptical of high returns with minimal risk claims.
- Check for regulatory registration and licenses.
- Avoid companies that lack transparency about their operations.
Fake Exchanges
- These appear out of nowhere and, after being active for a few months, mysteriously vanish with user funds.
Countermeasures:
- Use established and well-known exchanges.
- Check for user reviews and regulatory compliance.
- Verify the exchange’s track record and transparency.
Keys to Identifying Threats:
- Be cautious of new exchanges without a verifiable history.
- Look for exchanges with strong security practices and user protections.
- Avoid platforms that lack clear information about their team and location.

How to Report Crypto Scams
Reporting crypto scams is crucial to protecting the crypto community and helping to combat fraud in the crypto market. If you suspect a cryptocurrency scam, you should immediately report it to the relevant authorities and platforms. Many scammers use phishing scams and fake websites to trick users into revealing their private keys or sending cryptocurrency to fraudulent addresses. To report these common crypto scams, you can contact organizations like the Federal Trade Commission (FTC) and the Internet Crime Complaint Center (IC3), as well as specific cryptocurrency exchanges and wallet providers. It’s also important to share your experience on social media and crypto forums to warn others about common crypto scams and how to avoid them. Reporting these scams such as the romance scam, fake crypto exchange, giveaway scam, pump-and-dump scams, crypto phishing scams, rug pull scams not only helps prevent further victims of a cryptocurrency scam but also aids in tracking and shutting down scam operations. Remember, if you fall victim to a crypto scam, act quickly to report it and protect your remaining crypto assets.
Conclusion
While doing cryptocurrency transactions it is important to keep these types of crypto scams in your head as a way to avoid them. Even legitimate projects can get hacked, leading to official pages displaying scam content. Always stay cautious, verify information, and avoid rushing into anything. Enjoy the opportunities in the crypto world, but remember to prioritize security above all.
Stay safe from Crypto Scammers, and happy trading! 🚀🔐
For additional ways to avoid cryptocurrency scams its important to find resources and verified information, consult reputable crypto security blogs, newsletters, and crypto-centric publications such as CoinDesk, CoinTelegraph, and security-focused blogs like Krebs on Security. Ensure continuous education on emerging threats and proactive measures in the rapidly evolving Web3 space.





