Summary of Role of Adversarial Exposure Validation in CTEM from the 2024 Gartner Hype Cycle:
Adversarial exposure validation (AEV) refers to technologies that simulate real-world attack scenarios to validate potential exposures in an organization’s infrastructure. These tools combine automated penetration testing (APT) with breach and attack simulation (BAS) to test the effectiveness of security controls, exposing exploitable vulnerabilities. AEV products are typically delivered as SaaS solutions, often involving agents or virtual machines to simulate attacks and validate existing defense mechanisms.
Key Benefits:
- Automation & Flexibility: AEV technologies offer high automation, reducing the need for in-house expertise while expanding the scope of testing with customized attack simulations.
- Security Posture Validation: These tools confirm the feasibility of attacks, helping organizations prioritize remediation efforts and assess how well their security controls protect critical assets.
- Continuous Threat Exposure Management (CTEM): AEV supports ongoing security assessments, allowing organizations to continually evaluate their defenses and optimize their security posture over time.
- Red Team Augmentation: These tools help augment human-led red team exercises, providing a baseline for red teams to focus on more advanced scenarios.
- Compliance & Control Validation: AEV exceeds compliance requirements by offering continuous validation, helping to identify gaps in security controls.
Business Impact: Adversarial exposure validation empowers security teams to demonstrate the true impact of security gaps, helping them make more informed decisions about remediation priorities, technology investments, and ongoing strategic security initiatives.
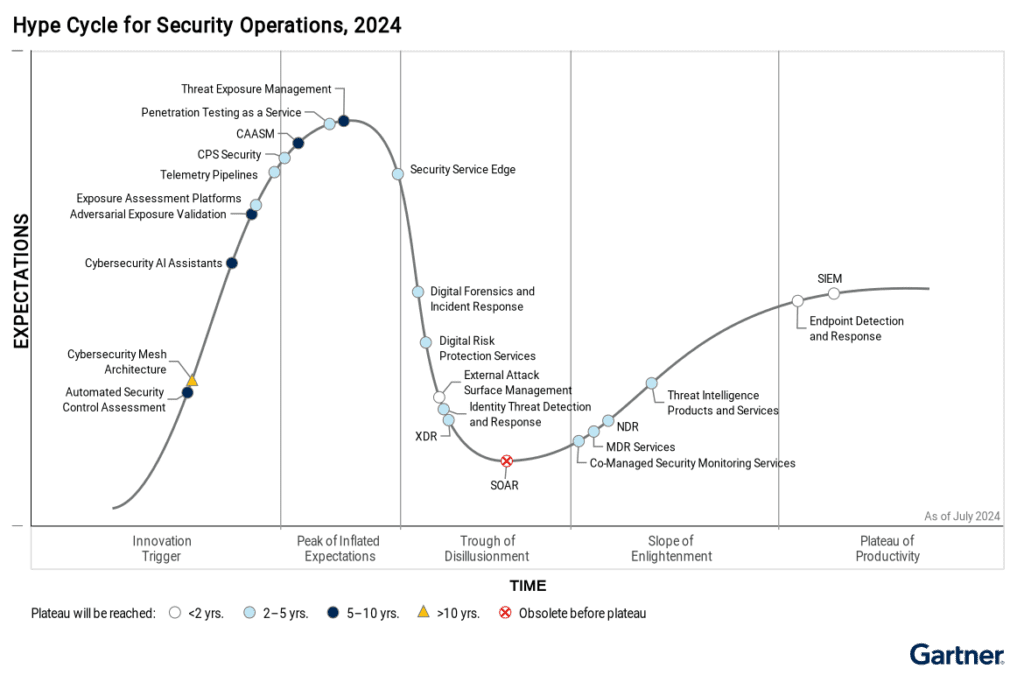
1. Market Adoption and Industry Usage of Adversarial Exposure Validation (AEV)
AEV is gaining traction across industries that prioritize continuous security validation. Sectors such as finance, healthcare, government, and critical infrastructure have been early adopters due to their high sensitivity to breaches and regulatory demands.
AEV is particularly useful in environments where organizations need to comply with regulations like HIPAA, PCI-DSS, or NIST, as it provides verifiable evidence that their security controls work against real-world attacks. Gartner has identified an increasing number of companies investing in Breach and Attack Simulation (BAS) tools, which provide the foundational capabilities for AEV.
Statistics on Adoption:
- According to Gartner, the global market for BAS tools (including AEV) is expected to grow from $217 million in 2021 to $600 million by 2026.
- A study by Ponemon Institute found that 56% of organizations that faced major cyber incidents could have prevented them through more robust validation of security controls, highlighting AEV’s growing importance.
This growth indicates that businesses are recognizing the need to go beyond traditional vulnerability management and shift to dynamic, attack-based validation.
What Gartner Got Right:
- Automation and Flexibility: The report accurately highlights the increasing importance of automation in security validation, particularly for organizations without the resources to maintain large red teams.
- Supporting Red Team Initiatives: It correctly identifies AEV as a tool that can enhance red team effectiveness by providing automated, repeatable attack scenarios that reduce the workload on manual teams.
- Emphasis on Security Posture Evaluation: The focus on how AEV tools can validate security controls and highlight exploitable paths within an organization is spot on.
- Increased Relevance to CTEM: By aligning AEV with broader exposure management, Gartner emphasizes the value of continuous validation in maintaining an evolving security posture.
What Gartner Missed:
Dark Web and Real-World Threat Intelligence: While the Gartner report covers AEV’s potential, it lacks a deeper integration of real-world threat intelligence, such as insights from the dark web, which are essential for understanding emerging adversary techniques and tools. Using open-source intelligence (OSINT) and dark web monitoring, combined with continuous pentesting solutions like NodeZero by Horizon3.ai, could provide richer context for AEV tools.
Broader Deployment Options: Gartner only briefly touches on deployment models (e.g., agent-based, agentless) but misses the potential of a hybrid architecture that would combine both models for more robust, flexible exposure validation. A hybrid approach is crucial, as it offers the versatility to simulate a wider range of attack scenarios across both cloud and on-prem infrastructure.
Focus on Warden’s Capabilities: Gartner does not fully explore the value of integrating adversarial exposure validation into Endpoint Defense Platforms like Warden, which combines Default Deny with Kernel API Virtualization. These tools not only validate security controls but actively prevent attacks during the later stages of the Kill Chain, making them more effective in real-world defensive strategies.
Lack of Discussion on AI and Machine Learning: Gartner did not delve into the potential for AI-driven insights in exposure validation. Tools powered by AI, like those integrated into Warden and Horizon3.ai, can offer predictive insights, automating the discovery of new attack vectors and optimizing defenses within an organizations environment against novel threats.
Market Landscape Overlook: Gartner’s analysis overlooks certain key players and innovations in this space. Beyond traditional vendors like AttackIQ and Cymulate, emerging competitors leveraging AI, deep OSINT, and continuous pentesting (e.g., NodeZero) deserve more recognition in the report for the disruption they’re bringing to the market.
Evolution of Adversarial Exposure Validation (AEV) in Continuous Threat Exposure Management (CTEM)
When reviewing the available sources on Adversarial Exposure Validation (AEV), it’s clear that AEV plays a critical role in Continuous Threat Exposure Management (CTEM) by simulating real-world adversary tactics to continuously test and validate security defenses.
AEV has evolved by integrating technologies like Breach and Attack Simulation (BAS), automated penetration testing, and Red Teaming. These components help organizations proactively assess their security posture, not only during specific moments in time but continuously, as threats evolve. AEV helps prioritize security gaps based on real-world exploits, ensuring that security teams address the most critical vulnerabilities first. This prioritization is key, especially when resources are limited.
Advantages of AEV over Today
One key advantage of AEV is its automation and scalability, which minimizes the need for extensive manual testing, making it more accessible for organizations that may not have large in-house security teams. Furthermore, it provides compliance support by offering continuous validation to meet penetration testing requirements that many industries face.
Compared to what you currently have, there are a few additional points to consider:
Proactive Attack Surface Management: This is crucial in continuously managing vulnerabilities across both on-premises and cloud environments, ensuring organizations can adapt as their infrastructures evolve.
Purple Team Integration: AEV supports the blending of offensive and defensive strategies, allowing teams to assess how security controls hold up under real-world adversarial testing.
Continuous Feedback Loop: Unlike traditional validation methods, AEV provides real-time insights, allowing organizations to continuously improve their security defenses by making timely adjustments.
To improve your current documentation, you could focus on highlighting AEV’s real-time monitoring, automation in reducing manual efforts, and support for compliance requirements, all of which are growing trends in this space. You could also elaborate more on how AEV is increasingly supporting cloud security validation and facilitating integration with security operations centers (SOCs).
Integration of AEV with SIEM, SOAR, and Other Security Tools
AEV does not function in isolation; it integrates with tools like Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) platforms. By feeding AEV data into SIEM systems, organizations gain insights into potential breaches and weak points, which allows Security Operations Centers (SOCs) to respond more effectively.
When integrated with SOAR, AEV can trigger automated responses to attack simulations, helping teams to automate remediation efforts based on findings from adversarial testing. This ensures that organizations are not just identifying security gaps but also remediating them rapidly, reducing Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR).
Key Benefits of Integration:
- Contextualized Threat Intelligence: AEV findings can be enriched with data from SIEM systems, providing a holistic view of the threat landscape.
- Automated Response: Integration with SOAR enables the automatic deployment of fixes or configuration changes to security controls based on AEV results.
- Improved Incident Response: Linking AEV simulations with incident response workflows ensures faster handling of critical issues.
Automation Limitations in AEV
While automation is central to AEV, it has certain limitations. Not all attack simulations can be automated, especially highly targeted attacks or zero-day exploits that require the nuanced thinking of a human red team. Some AEV platforms focus only on standard attack techniques, and while they do a great job at simulating those, they may not fully capture the sophistication of more advanced persistent threats (APTs).
Challenges in Automation:
- Limited Coverage: Many AEV tools primarily automate known attack vectors based on common tactics and techniques from frameworks like MITRE ATT&CK, but they may struggle with innovative attack techniques that adversaries develop.
- Customization Gaps: Automating highly specialized or targeted attacks requires a deep understanding of the unique configurations of an organization’s systems, which can be difficult to standardize in an automated tool.
- False Sense of Security: Relying solely on automated adversarial testing might lead to missed vulnerabilities that require more creative, human-driven testing.
Continuous Pentesting How Does it Compare?
The concept of Adversarial Exposure Validation (AEV) ties directly into Horizon3.ai’s NodeZero platform, which offers automated continuous penetration testing. NodeZero operates with a similar approach by mimicking real-world attack scenarios to evaluate an organization’s vulnerabilities, helping validate the efficacy of security controls and identify exposures. Through autonomous pentesting NodeZero allows you to Find, Fix and Verify your security risks in a continuous approach to reduce risks that build up overtime as the environment changes. NodeZero is agentless, self-service, and able to complete its tasks in hours verses weeks with accuracy that includes proof of exploit and the path it took with no false positives.
Here’s how NodeZero aligns with the AEV concept:
1. Automation and Scalability
NodeZero’s platform is designed to run continuous penetration testing autonomously. This aligns with the AEV requirement of automating red team efforts and reducing the need for expensive human-led testing. AEV stresses that automation enables organizations to perform regular, scalable security assessments without heavy manual involvement—exactly what NodeZero achieves by enabling on-demand testing.
2. Attack Simulation
NodeZero simulates real adversarial tactics to test how effectively security controls stand up to attacks. Like AEV solutions, NodeZero focuses on simulating real attack techniques to demonstrate not just the presence but also the exploitability of security weaknesses. This form of active validation is crucial to understanding an organization’s true security posture.
3. Actionable Remediation Guidance
Horizon3.ai emphasizes actionable insights from NodeZero’s findings. The platform doesn’t just identify vulnerabilities; it helps prioritize them based on actual risk and provides steps for remediation, which is one of the core benefits of AEV. AEV solutions are designed to deliver practical, prioritized remediation advice, allowing security teams to focus on addressing the most impactful exposures first.
Continuous Threat Exposure Management (CTEM) NodeZero plays a role in helping organizations move toward a CTEM framework by providing continuous validation rather than one-off assessments. It supports regular attack simulations that test defenses over time and across changing infrastructures, including hybrid and cloud environments, which is a growing focus in adversarial validation .
5. Augmentation**
NodeZero is also positioned as a tool for augmenting traditional red team activities. This aligns with the AEV model of blending automated tools with human-led initiatives to create a more robust security validation process. It helps smaller or less mature organizations who cannot afford full-time red teams by automating attack techniques.
alities, it’s clear that NodeZero offers a highly effective AEV solution, supporting both automated validation of security postures and ongoing exposure management.
How NodeZero is Not Aligned with Adversarial Exposure Validation (AEV)
While Horizon3.ai’s NodeZero is highly aligned with Adversarial Exposure Validation (AEV), there are some areas where it may not fully match the scope and depth of AEV as described by Gartner. Here are some potential misalignments:
1. Narrower Focus on Automated Penetration Testing
NodeZero’s core offering is continuous, automated penetration testing. While this covers a large part of adversarial exposure validation, NodeZero might not fully cover the breadth of BAS functionalities that AEV typically encompasses, such as hybrid or agentless deployment options, which allow simulations from both within and outside an organization. AEV also aims to simulate more diverse attack vectors, not just limited to penetration testing but broader attack surface simulations
AEV often includes:
- BAS (Breach and Attack Simulation) capabilities for broader attack scenarios.
- Simulating various paths, both internal and external, that an attacker might take.
While NodeZero is strong in continuous penetration testing, it may not be as comprehensive in hybrid or complex multi-step simulation scenarios as some broader AEV solutions like AttackIQ or Cymulate, which allow for layered attack simulation.
2. Limited Focus on Compliance-Driven Simulations
AEV is used by organizations to not only validate security controls but also to meet compliance requirements. It involves continuous validation against standards such as PCI-DSS or ISO. NodeZero may offer penetration testing automation, but the platform might not emphasize compliance-focused scenarios as strongly as other AEV tools designed to support auditors, third-party risk assessors, and highly regulated industries
While NodeZero provides actionable remediation, the lack of a direct focus on regulatory acceptance of automated test results may be a gap compared to other AEV vendors that offer compliance-specific validation reports.
3. Integration and Deployment Flexibility
According to the AEV model, adversarial exposure validation should allow flexible deployment models, such as agent-based and agentless approaches, to simulate various attack vectors from both internal and external perspectives. NodeZero is primarily focused on agentless automated penetration testing but may not offer the same hybrid flexibility that’s increasingly relevant to AEV.
Some AEV vendors provide both agent and agentless deployments to simulate scenarios from an assumed breach or an external adversary’s perspective. If NodeZero lacks this hybrid approach, it could limit organizations seeking more versatile validation methods.
4. Extensive Integration into Security Operations (SOC)
AEV tools are often expected to provide deep integration into existing security operations tools, such as SIEMs or SOAR platforms. This integration enables continuous feedback between AEV tests and defensive systems like firewalls, endpoint detection, or network monitoring solutions. NodeZero focuses more on delivering findings from penetration tests but might not emphasize integration with security tools as robustly as other AEV solutions that provide comprehensive security control validation.
5. Purple Teaming Support
The AEV concept heavily emphasizes Purple Teaming, where red and blue teams collaborate to fine-tune security controls in real time based on adversarial testing. NodeZero’s strength lies in automated red teaming, but the platform may not have a fully developed collaborative Purple Teaming feature set, which involves real-time defensive adjustments.

Top-11 Questions people are commonly asking about Adversarial Exposure Validation.
1. What is Adversarial Exposure Validation (AEV)?
Adversarial Exposure Validation is the continuous and automated process of simulating real-world attack scenarios to identify exploitable vulnerabilities in an organization’s defenses. It combines techniques like automated pentesting and breach simulation to validate how effective existing security controls are against potential threats. This allows organizations to prioritize risks that have a real-world impact rather than focusing on theoretical vulnerabilities.
2. Why is Adversarial Exposure Validation important for cybersecurity?
AEV is crucial because it goes beyond identifying vulnerabilities to testing their exploitability in real-world conditions. It helps security teams prioritize critical risks by simulating attacks that could impact an organization’s most valuable assets. This can drive strategic decision-making by demonstrating the weaknesses in an organization’s defenses and focusing remediation efforts where they are needed most.
3. How does Adversarial Exposure Validation relate to Continuous Threat Exposure Management (CTEM)?
AEV is a key component of CTEM programs, which are designed to manage and mitigate threats continuously. CTEM focuses on providing a comprehensive and dynamic view of an organization’s threat landscape by validating security exposure on an ongoing basis. AEV plays the role of simulating attacks within CTEM to keep security teams updated on how their defenses hold up against evolving threats.
4. How is AEV different from traditional vulnerability management?
Traditional vulnerability management identifies and lists theoretical vulnerabilities, but AEV goes a step further by simulating how those vulnerabilities could be exploited in real-world scenarios. This means AEV delivers more actionable insights, helping organizations focus on fixing vulnerabilities that are most likely to be exploited by attackers.
5. What are the key benefits of Adversarial Exposure Validation?
Some key benefits include:
- Continuous validation of security controls.
- Automation of red teaming and attack simulations.
- Improved prioritization of critical vulnerabilities.
- Enhanced compliance readiness through consistent testing.
- Reduced attack surface by validating security posture over time.
6. Which organizations should implement AEV?
AEV is typically implemented by organizations with mature cybersecurity practices, especially those that are focused on CTEM or red team augmentation. It is ideal for security operations teams that need to continuously validate and improve their defenses, particularly in industries where compliance with security regulations is critical, such as healthcare, finance, and government.
7. How does AEV support red teaming and purple teaming?
AEV helps augment red teaming by automating many of the repetitive tasks and attack simulations, allowing human-led red teams to focus on more advanced and complex attack scenarios. It also supports purple teaming, where red and blue teams collaborate by simulating attacks and immediately testing the blue team’s response to highlight defense gaps.
8. What role does automation play in AEV?
Automation is at the core of AEV, allowing security teams to continuously and consistently test their defenses against simulated attacks. This automation helps reduce the manual effort needed for traditional red teaming or pentesting, allowing for more frequent assessments and quicker identification of exploitable vulnerabilities.
9. What are the limitations of Adversarial Exposure Validation?
Some limitations include:
- Complexity of implementation: Setting up and running AEV tools requires a deep understanding of threat actor techniques and the organization’s infrastructure.
- Acceptance issues: Some industries, particularly regulated sectors, may not accept AEV results for formal audits or assessments.
- Narrow focus of some tools: Certain AEV tools focus only on red teaming use cases, while others may not fully integrate with existing CTEM processes, limiting their applicability in broader security programs.
10. What are some examples of AEV tools in the market?
Leading AEV tools include:
- Horizon3.ai NodeZero: Continuous pentesting solution that automates attack simulations and provides deep insights into vulnerabilities.
- AttackIQ: A platform focused on breach and attack simulation.
- Cymulate: A platform offering attack simulation across various threat vectors.
- SCYTHE: Provides highly customizable adversarial attack simulations.
11. How does AEV fit into the 2024 Gartner Hype Cycle for Security Operations?
The 2024 Gartner Hype Cycle for Security Operations identifies AEV as moving from the early stages of adoption into the Plateau of Productivity. Organizations are increasingly adopting AEV to automate red teaming and continuous exposure management. However, Gartner also highlights that AEV tools, while promising, may not fully replace human-driven attack simulations in the short term due to their automation limitations.
As AEV technology matures, it will likely evolve to offer more adaptive learning capabilities, enabling it to simulate increasingly complex attack patterns. For now, hybrid models that combine automated and manual adversarial testing remain the best approach for organizations aiming to validate their security defenses against advanced persistent threats.





