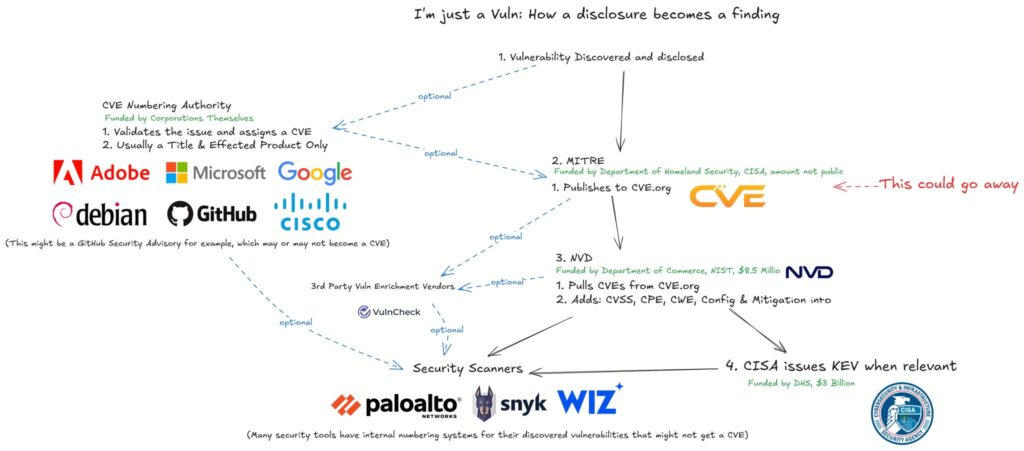
The Collapse of CVE: A Necessary Evolution for Cybersecurity
As the National Institute of Standards and Technology’s National Vulnerability Database (NVD) and MITRE’s work on CVEs continue to falter under the weight of thousands of backlogged entries and deferred vulnerabilities, it is clear that the industry’s reliance on the decades-old CVE framework is a systemic liability. While some view the government’s measured interventions as overreach, a closer examination reveals that recalibrating the current system—and even allowing the collapse of CVE—could be the catalyst for a new era in vulnerability management. However, CISA funded an extension for MITRE to continue on with its current roles. This debate has opened up a wound in the industry, showing how fragile it can be. Thus, with the focus on establishing a non-profit foundation to offer another funding path, might be a good thing, if the system is reevaluated.

A Fragile National Vulnerability Foundation (e.g. CVEs)
For years, the CVE system has been touted as a neutral, comprehensive framework for identifying and cataloging software vulnerabilities. However, recent struggles within the NVD—its backlog of unresolved entries and its inability to keep pace with evolving threats—demonstrate that the infrastructure is crumbling from within. When critical vulnerabilities languish in queues for enrichment, the entire ecosystem—from scanners to advisory systems—suffers, leaving organizations vulnerable in an environment where threats evolve exponentially.
Users of CVE Program & Database: Stuck in a Reactive Vulnerability Cycle
Organizations and end users have come to depend on the CVE system for timely risk assessments and remediation guidance. But this dependency has created a feedback loop of inefficiency and false security. Instead of driving innovation or genuine improvement in vulnerability management, the community of CVE users clings to a model that is inherently reactive. The inability to rapidly correlate emerging threats to actionable intelligence has left many organizations scrambling to manage risk on outdated information. For these users, the collapse of the current CVE system offers an opportunity to break free from a stalemate and adopt a more agile and predictive approach to cybersecurity.

Vulnerability Industry Providers: Complacency and the Cost of CVE Status Quo in Cybersecurity
The entrenched network of vendors and security tool providers has built multi-billion-dollar industries around the existing CVE framework. This dependency has fostered a complacency that stifles innovation. Rather than aggressively pursuing modern techniques for vulnerability detection and management, many providers seem content to merely adapt their offerings to a flawed system. Their reluctance to embrace disruption ultimately hinders progress across the entire cybersecurity landscape. The inevitable collapse of the CVE system, therefore, can be seen not as an unfortunate failure but as a necessary disruption—one that forces industry providers to develop inventive solutions better aligned with today’s dynamic threat environment.
CVEs Industry Experts and Academia: Lost in Theory, Overlooked in Practice
Despite their reputation as thought leaders, many industry experts and academic researchers have long been tethered to the theoretical constructs of the CVE system. Rather than confronting its limitations head-on, these groups have often prioritized incremental improvements and theoretical models that fail to address the practical realities of modern cybersecurity. Academic research, in particular, risks becoming irrelevant if it continues to analyze vulnerabilities within an outdated framework rather than embracing innovative paradigms that could radically enhance risk management practices. The current stagnation is a wake-up call: clinging to the CVE’s legacy framework means neglecting the necessity for transformative methodologies that reflect the rapid evolution of cyber threats.
Government Intervention: A Proactive, Justified Mandate
Critics of government intervention often decry the potential for bureaucratic overreach. Yet when faced with systemic risk, measured regulatory involvement is not only warranted but essential. The government’s recent steps to intervene are aimed squarely at remedying the failures of a dated system. Unlike the slow and unwieldy processes that underpin the current CVE ecosystem, a centralized, government-led initiative could set new standards for cybersecurity that are responsive, comprehensive, and future-proof. By pushing for the collapse of the existing CVE regime, policy makers are not simply disrupting an industry norm; they are catalyzing the development of an integrated framework that could ultimately serve the public interest far more effectively than the status quo ever did.
Government intervention, often mischaracterized as heavy-handed, is in fact a corrective measure—a prompt for the entire sector to innovate or be left behind. As the backlog of vulnerabilities continues to grow unabated, the cost of inaction becomes increasingly clear. The government’s strategy, aimed at streamlining vulnerability management and fostering a forward-thinking cybersecurity ecosystem, is both justified and urgently needed.
Conclusion: Embracing a New Cybersecurity Paradigm
The ongoing debate of the CVE system is not merely a technical hiccup—it is a systemic failure with wide-reaching implications for cybersecurity as a whole. Users stuck in a cycle of reactive risk management, complacent industry providers, and experts ensnared by outdated paradigms are all part of a broken model. The collapse of the current CVE framework, though painful in the short term, represents an opportunity for profound change. With government intervention paving the way, the future of vulnerability management could pivot toward a dynamic, agile, and holistic system that addresses the challenges of modern threat landscapes.
In this context, the fact that the government’s actions continued to kick the can down the road is of concern, are they justified? For the sake of national security, industry resilience, and the integrity of digital infrastructure, it is time to let the old CVE framework collapse and to build something robust and responsive in its place. So lets look at what that system might look like, Embracing the Future.