The True Cost of Downtime and Data Breaches in 2024: What Small Businesses Need to Know
In today’s fast-paced digital world, nothing halts progress faster than unplanned downtime. Every second of an outage means lost revenue, frustrated customers, and a blow to your reputation. The costs are staggering—millions per hour for many industries—yet it’s not just about the money. Downtime can disrupt supply chains, undermine trust, and even cripple businesses.
Downtime in any organization can lead to significant financial losses, especially when driven by cybersecurity issues. As businesses increasingly rely on digital systems, a breach, server failure, or data loss incident can cause more than just operational disruption—it can cost millions, affecting productivity, reputation, and revenue.
But here’s the good news: you don’t have to let downtime hold you back. This article will guide you through the hidden costs of downtime, how to calculate its true financial impact, and, most importantly, what you can do to minimize it. If you’re ready to turn costly setbacks into opportunities for growth, you’re in the right place.
The Growing Cost of Downtime
According to a report from ITIC, 44% of enterprises face downtime costs exceeding $1 million per hour, with this figure rising due to more frequent and damaging security hacks and breaches. A single minute of server downtime for high-critical systems can range from $4,998 to $16,700. The increasing frequency of these events—attributable to factors like cyberattacks and supply chain disruptions—means downtime costs have grown by 32% over the past seven years.
The Ponemon Institute also revealed that in 2021, the average cost of a data breach was $4.24 million, a 10% increase from 2019. Lost business and customer churn accounted for the largest share of these costs. These figures underscore the severity of downtime in today’s interconnected and fast-moving business environments.
Calculating the Average Cost of Downtime – True Cost in 2024
What is Downtime?
Downtime refers to the period when a system, network, or service is unavailable due to an incident—whether it’s caused by a cyberattack, hardware failure, or human error. Downtime affects an organization’s productivity, customer satisfaction, and revenue.
Why Downtime Costs Matter
Even brief downtime events can have substantial financial consequences. Factors such as the industry you’re in, the criticality of the affected systems, and the duration of the outage all contribute to the total cost.
- Industry Impact: Highly regulated industries like healthcare and finance suffer the most from downtime. For example, an hour of downtime in financial services can result in $500,000 or more in lost transactions.
- Business Size: Large enterprises may incur greater downtime costs due to complex infrastructure and high transaction volumes. Small businesses may experience proportionally significant impacts, though on a smaller financial scale.
Factors Driving Downtime Costs
Downtime costs stem from a variety of sources. Here’s a breakdown of the key factors that contribute to the overall financial impact of a disruption:
Lost Revenue: When systems go down, sales and transactions halt. For e-commerce and service businesses, this can mean a direct hit to the bottom line.
Productivity Loss: Employees are left idle when access to systems and data is unavailable. This can quickly add up, especially in companies with large workforces dependent on network systems to carry out their jobs.
Recovery Efforts: The time and resources spent on recovering lost data, repairing systems, and ensuring full restoration often requires overtime, IT specialists, and external consultants—all of which incur costs.
Compliance Fines: In industries like healthcare and finance, downtime can lead to non-compliance with regulations such as HIPAA or SOX, resulting in hefty fines and legal consequences.
Customer Dissatisfaction: If downtime affects customer-facing systems, customer trust is quickly eroded. For instance, repeated incidents can lead to churn, reputation damage, and negative press.
By understanding these cost drivers, companies can identify where investments in cybersecurity and system reliability will have the greatest return.
Calculating Downtime Costs
To calculate the cost of downtime for your organization, follow these steps:
Identify Key Variables:
- Revenue Per Hour: Calculate how much revenue your organization generates per hour.
- Number of Employees Affected: Determine the number of employees impacted by the downtime.
- Employee Hourly Rate: Calculate the average hourly wage of these employees.
- Downtime Duration: Estimate the total time the system is expected to be down.
Downtime Cost Formula:
- Downtime Cost = (Revenue Per Hour × Downtime Duration) + (Number of Employees × Employee Hourly Rate × Downtime Duration)
How to Calculate Your Business’s Downtime Costs
To make the impact of downtime tangible for your business, here’s a simple formula you can use:
Downtime Cost = (Lost Revenue per Hour + Lost Productivity per Hour + Recovery Costs per Hour) × Hours of Downtime
Lost Revenue per Hour: This can be calculated by taking your company’s average annual revenue and dividing it by the total number of business hours in a year.
Lost Productivity per Hour: Multiply the number of affected employees by their average hourly wage and add the productivity loss (which could be partial, say 50% of their effectiveness).
Recovery Costs per Hour: This includes IT costs, overtime pay, consultants, and the cost of restoring data and systems.
Example Scenario
Example 1: For a mid-sized company with $50 million in annual revenue, 100 employees affected, and an IT recovery rate of $10,000 per hour, a four-hour downtime could cost:
- Lost Revenue = $50,000
- Lost Productivity = $10,000 (100 employees × $50 average hourly wage × 50% effectiveness)
- Recovery Costs = $40,000
Total Cost for 4 hours of downtime = $100,000
Example 2: Let’s say your company is an e-commerce platform. Here’s how you can estimate the downtime cost:
- Revenue Per Hour: $100,000
- Number of Employees Affected: 50
- Employee Hourly Rate: $30
- Downtime Duration: 4 hours
Step 1: Calculate revenue loss:
- $100,000 (Revenue Per Hour) × 4 hours = $400,000
Step 2: Calculate employee productivity loss:
- 50 employees × $30 per hour × 4 hours = $6,000
Step 3: Add both losses to get the total downtime cost:
- $400,000 + $6,000 = $406,000
In this case, the estimated cost of 4 hours of downtime for this e-commerce business is $406,000.
Long-Term Impacts of Frequent Downtime on Business Operations
Downtime incidents don’t just have short-term financial consequences; frequent downtime can lead to long-term damage, particularly to your company’s brand, reputation, and competitive edge.
Customer Trust: Repeated outages erode customer confidence, and many may opt to switch to competitors who can offer more reliable service. Studies show that 76% of consumers will leave a brand after two or more unsatisfactory experiences.
Reputation: Businesses with consistent downtime may be perceived as unreliable, which can affect future partnerships and customer acquisition. Negative press and social media backlash can cause lasting damage.
Competitive Positioning: When a company struggles with frequent downtime, it risks losing its market position to competitors that offer more stable services. In industries like fintech or e-commerce, reliability is often a key differentiator.
Top 15 Cybersecurity Risks in 2024 and How to Calculate Their Financial Impact
| Risk | Likelihood (2023-2024) | Severity | Severity % | Trends and Key Insights |
|---|---|---|---|---|
| Phishing | Very High | High | 75% | Phishing remains the top cyber threat, with 90% of data breaches stemming from it. Expected to dominate as phishing tactics become more sophisticated. |
| Ransomware | High | Very High | 85% | Involved in 70% of malware-based breaches. Costs of recovery have surged, particularly in critical sectors like healthcare. |
| Malware | High | High | 75% | Nearly 560,000 new malware pieces detected daily, with significant increases in 2023. Email remains a common delivery method. |
| Data Breaches | High | Very High | 85% | 48% of organizations have suffered data breaches, often resulting from phishing and ransomware attacks. |
| Business Email Compromise (BEC) | Medium | High | 70% | BEC attacks cause major financial losses, with over $500 million lost annually due to fraudulent transfers. |
| Insider Threats | Medium | Medium | 60% | Employees’ negligence or malicious actions pose a significant risk, with the frequency of insider threats rising in 2023. |
| Mobile Device Attacks | Medium | Medium | 60% | With the rise of remote work, attacks on mobile devices through social media and messaging apps are becoming more common. |
| Supply Chain Attacks | Medium | Very High | 85% | Increasingly sophisticated attacks on software supply chains, as seen in the SolarWinds breach, pose systemic risks. |
| Software Supply Chain Attacks | Medium | Very High | 85% | Vulnerabilities in third-party code have led to critical breaches, with attacks on open-source software increasing. |
| Cloud Vulnerabilities | Medium | High | 75% | Misconfigurations in cloud services have led to major breaches, with cloud environments becoming primary targets. |
| Zero-Day Exploits | Low | Very High | 90% | Though rare, zero-day exploits can be catastrophic, allowing attackers to exploit unknown vulnerabilities. |
| Infrastructure Attacks | Medium | Very High | 80% | Critical infrastructure is increasingly targeted by nation-state actors, with attacks on energy grids and healthcare systems rising. |
| DDoS Attacks | Medium | Medium | 60% | Distributed Denial of Service attacks have surged, especially against financial institutions and government websites. |
| Credential Theft | High | High | 75% | Credential theft, particularly through password spraying and brute force attacks, continues to increase, with significant consequences for data breaches. |
| IoT Device Attacks | Medium | High | 70% | As IoT devices proliferate, they are increasingly targeted, often due to poor security configurations and lack of updates. |
| Exploits of Vulnerabilities | High | High | 75% | Exploits targeting known vulnerabilities are a common attack vector, emphasizing the need for timely patching and updates. |
Severity Percentage Explanation:
- Low severity: 50%-60%
- Medium severity: 60%-70%
- High severity: 70%-80%
- Very High severity: 80%-90%
This table outlines the most pressing cyber risks organizations are expected to face in 2024 based on trends from 2022 and 2023. Each risk’s severity percentage is intended for use in calculating cybersecurity impact, including metrics like the Single Loss Expectancy (SLE).
Likelihood Percentage Explanation:
Very High: 75% – 90%
- This indicates a high probability of the event occurring within a given year. In cybersecurity, risks like phishing or malware attacks fall into this category due to their prevalence.
High: 60% – 75%
- High likelihood suggests that an attack or incident is likely to happen, but with slightly less frequency compared to very high risks. Common attacks like ransomware and credential theft fit here.
Medium: 40% – 60%
- Medium likelihood implies that the event may happen occasionally, but not as frequently as the more common risks. Examples include insider threats or mobile device attacks.
Low: 10% – 40%
- A low likelihood represents events that are less likely to occur but are still possible. Zero-day exploits or some nation-state infrastructure attacks might be placed here.
These percentages reflect the frequency of occurrence in a given period (typically a year), based on historical data and trend analysis.
Calculating Average Cost of Cybersecurity Risk (e.g. Cost of a Data Breach)
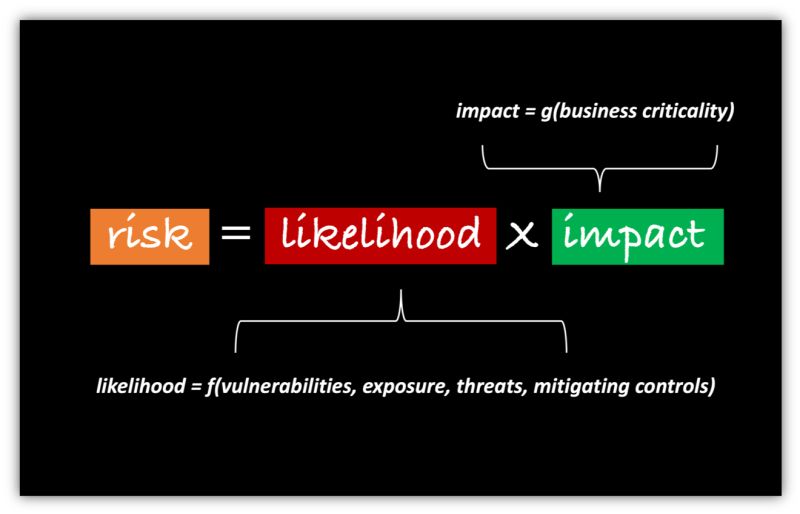
True Cost of Downtime – Single Loss Expectancy (SLE): Calculating % Exposure in a Cyberattack
In risk management, Single Loss Expectancy (SLE) helps determine the financial impact of a cybersecurity event. The formula for SLE is:
SLE = Asset Value × Exposure Factor (EF)
The Exposure Factor (EF) represents the percentage of loss a particular asset would suffer in a cyberattack. This percentage is based on how vulnerable an asset is and the anticipated damage from a specific threat.
Determining % Exposure (EF):
Asset Criticality: Evaluate how critical the asset is to your business operations. High-value assets like customer data or financial systems usually have a higher exposure factor, as their compromise can cause major disruption.
Threat Likelihood: Consider the type of threat and its potential impact on the asset. For example, ransomware that encrypts sensitive data may lead to an EF of 80%, while a DDoS attack that only causes a temporary service outage might have an EF of 20%.
Existing Safeguards: Analyze how well the asset is currently protected. If the company has robust encryption and intrusion detection systems in place, the exposure factor will be lower because these measures reduce the potential damage.
Incident History and Scenarios: Review past incidents or simulated attack scenarios to estimate the degree of loss. If prior breaches led to 30% data loss or revenue impact, this can help set the EF for future risk calculations.
Annual Loss Expectancy (ALE) and Value of Safeguard (VoS)
Annual Loss Expectancy (ALE): The Annual Loss Expectancy is a risk assessment formula used to determine the potential annual financial impact of a threat to an organization. It is calculated by multiplying the Single Loss Expectancy (SLE)—the monetary loss expected from a single incident—by the Annual Rate of Occurrence (ARO), which is the estimated number of incidents expected to occur in a year.
Formula:
- ALE = SLE × ARO
Value of Safeguard (VoS): The Value of Safeguard is a way to measure the effectiveness and financial benefit of a security control or safeguard by evaluating how much it reduces your ALE. It is calculated by comparing the ALE before and after implementing a safeguard, then subtracting the annual cost of maintaining the safeguard.
Formula:
- VoS = ALE(before) − ALE(after) − Annual Cost of Safeguard
By calculating both ALE and VoS, organizations can determine whether the cost of implementing security measures is justified by the reduction in risk and potential losses.
To effectively assess the financial risks, companies should calculate their Single Loss Expectancy (SLE), Annual Loss Expectancy (ALE), and Value of Safeguard (VoS). These are foundational metrics in risk management that help quantify the potential impact of security incidents:
Single Loss Expectancy (SLE): This represents the potential loss from a single event. It is calculated using the formula:
SLE = Asset Value x Exposure Factor (EF)
Example: If a critical server valued at $500,000 has a 20% exposure during a cyberattack, the SLE is $100,000.Annualized Loss Expectancy (ALE): This extends the SLE to estimate potential yearly losses, accounting for the frequency of incidents.
ALE = SLE x Annual Rate of Occurrence (ARO)
Example: With an ARO of 0.5, the ALE would be $50,000 annually.Value of Safeguard (VoS): VoS measures the cost savings from implementing security measures.
VoS = ALE (before safeguard) − ALE (after safeguard) − Annual Cost of Safeguard
Example: If an Intrusion Detection System (IDS) reduces ALE from $100,000 to $50,000, and the IDS costs $20,000 annually, the VoS is $30,000—a clear return on investment (ROI) from cybersecurity measures.
Summary of the Cybersecurity Scenario
Consider a company with an annual loss expectancy (ALE) of $100,000 due to network breaches. They install an IDS that reduces the ALE to $50,000, with an annual cost of $20,000. Using the formula:
- VoS = ($100,000 – $50,000) – $20,000
- VoS = $30,000
In this case, the safeguard delivers $30,000 in savings annually by reducing potential loss.
Preventing Cybersecurity-Related Downtime
Cyberattacks are one of the leading causes of costly downtime. From ransomware attacks that encrypt vital data to DDoS attacks that crash critical systems, businesses need to implement targeted defenses to minimize the risk.
Key strategies include:
Zero Trust Architecture: Adopt a Zero Trust approach where access is continuously verified at every stage. This limits exposure to internal threats and unauthorized access.
Endpoint Protection: Ensure all devices, including employee laptops and mobile devices, have up-to-date security software to prevent breaches from spreading through the network.
Regular Patching: Many cyberattacks exploit known vulnerabilities. Keeping systems patched and updated is essential to close these gaps.
Case Study: In 2023, a large financial services company experienced a ransomware attack that resulted in a 3-day downtime. By having a Zero Trust network and a robust recovery plan, they were able to recover systems within 24 hours without paying the ransom—saving them millions in potential downtime costs.
Justifying Downtime Prevention Investments to Leadership
One of the biggest challenges IT teams face is convincing leadership to allocate budget for downtime prevention. Here’s how to frame the discussion:
Use Data: Present downtime cost estimates for your business, including lost revenue, recovery efforts, and potential compliance penalties. Showing the numbers can make the abstract concept of downtime more concrete.
ROI of Prevention: Compare the cost of investing in preventive technologies like cybersecurity tools or redundant infrastructure to the costs of a potential downtime incident. Investments in downtime prevention often pay for themselves many times over by preventing catastrophic losses.
Risk Mitigation: Highlight the non-financial benefits as well, including risk mitigation and regulatory compliance. Downtime in highly regulated industries can result in legal penalties far exceeding direct financial losses.
How to Recover from Cyberattack-Induced Downtime
No matter how robust your defenses, cyberattacks are sometimes unavoidable. Having a solid recovery plan can minimize downtime and reduce costs.
Containment: Immediately isolate affected systems to prevent the attack from spreading. This may include shutting down specific services or network segments.
Restoration: Work with your IT team to restore systems from the most recent clean backups. If your data is encrypted by ransomware, having offline backups is key to a quick recovery.
Communication: Inform your stakeholders—customers, employees, partners—about the incident and provide a clear timeline for resolution. Transparency helps maintain trust during recovery.
Post-Incident Review: After recovering from downtime, conduct a thorough review to identify what went wrong and implement improvements to prevent future incidents.
Downtime Real Costs per Industries
Downtime can have a devastating financial impact across various industries, with costs of downtime often climbing into millions per hour. Nearly 98% of organizations report that just one hour of downtime can cost them over $100,000. Here’s a deeper look at how downtime costs vary across key industries:
IT Industry
- Cost of Downtime: $5,600 per minute
- Hourly Range: From $145,000 to $450,000 per hour, depending on company size.
- The IT industry’s reliance on continuous operations means even minor outages can result in significant financial loss, particularly for service-based businesses where availability is key to customer satisfaction.
Automotive Industry
- Cost of Downtime: $50,000 per minute or $3 million per hour
- 70% of downtime is often due to lack of equipment maintenance awareness or missed update requirements. Downtime in auto manufacturing can delay production, supply chain logistics, and even customer deliveries, amplifying the financial impact.
Manufacturing Industry
- Cost of Downtime: $260,000 per hour
- Manufacturers endure around 800 hours of downtime annually due to maintenance and equipment failures. Given the industry’s dependency on seamless processes, unexpected downtime can cascade across supply chains, leading to substantial revenue losses.
Enterprise Industry
- Cost of Downtime: Between $1 million to $5 million per hour, excluding potential fines or penalties.
- When factoring in server outages, downtime can hit $300,000 per minute. As reliance on digital marketplaces grows, downtime costs have risen 32% over the past seven years, further stressing the importance of robust digital infrastructure.
Other Key Industries
- Media: $90,000 per hour — Media companies rely heavily on constant content delivery; a single outage can disrupt broadcasts, advertising, and audience engagement.
- Health Care: $636,000 per hour — Downtime in healthcare can jeopardize patient care and safety, often resulting in delays in treatment and additional costs.
- Retail: $1.1 million per hour — In a highly competitive space, even a brief disruption in operations can result in significant revenue loss, as consumers seek alternatives.
- Telecommunications: $2 million per hour — Telecom companies are the backbone of digital communication, and downtime not only affects consumers but can also impact national and global business operations.
- Energy Industry: $2.48 million per hour — Downtime in energy supply systems can halt production, delay distribution, and create safety hazards.
- Brokerage Services: $6.48 million per hour — Financial transactions grind to a halt during outages, making this one of the most costly sectors for downtime.
By understanding these figures, businesses can better prepare for downtime, investing in preventive measures and robust IT infrastructure to mitigate the true cost of a data breach or service outage in 2024.
Conclusion: Cost of a Data Breach – Avoid Downtime and Data Loss
In today’s digital landscape, the cost of downtime is no longer just an IT issue—it’s a critical business risk that impacts every facet of an organization, from financial stability to customer trust. As cyber threats grow more sophisticated, the potential for downtime increases, making it imperative for businesses to have robust strategies in place. From understanding Single Loss Expectancy (SLE) and Annual Loss Expectancy (ALE) to evaluating the Value of Safeguards (VoS), calculating the true financial impact of downtime is essential for maintaining operational resilience.
Organizations that fail to account for these risks face escalating costs, whether from lost revenue, diminished productivity, or regulatory penalties. By proactively assessing your vulnerabilities and implementing effective safeguards, you can significantly mitigate downtime and its financial impact, safeguarding not only your bottom line but also your reputation.
If you’re ready to take control of your organization’s cybersecurity and minimize the risks of downtime, we can help. Reach out today to discuss how our solutions can protect your business from costly disruptions and ensure continuous operation. Let’s work together to secure your future.

Top 7 Downtime Questions
What are the average costs of downtime for my industry?
- As a business owner or IT professional, understanding how much downtime costs in your industry is crucial. Whether you’re in healthcare, finance, or retail, each minute of downtime can translate to thousands of dollars lost. For example, in healthcare, downtime can cost nearly $7,900 per minute. How do your operations stack up against industry averages?
What factors contribute to the high cost of downtime?
- You might be wondering why downtime can be so expensive. Lost revenue, productivity drops, recovery expenses, and customer dissatisfaction are all significant contributors. Additionally, if you’re in a highly regulated industry, compliance fines can add another layer of cost. Knowing these factors can help you identify where your business is most vulnerable.
How do I calculate my business’s specific downtime costs?
- Calculating downtime costs might seem overwhelming, but it’s essential to have a clear estimate. The formula combines lost revenue, productivity losses, and recovery expenses. By using this, you can better advocate for necessary investments in cybersecurity and infrastructure. What would a 4-hour downtime incident cost your business?
What can I do to prevent downtime caused by cyberattacks?
- Cybersecurity downtime is a real threat, and as someone responsible for maintaining business operations, you need to understand how to prevent it. Adopting a Zero Trust architecture, ensuring endpoint protection, and regularly patching systems are critical strategies. Have you evaluated your current cybersecurity measures?
What are the long-term impacts of frequent downtime?
- If your business experiences repeated outages, you’re likely concerned about more than just the immediate financial impact. Long-term effects can include damaged customer trust, a weakened reputation, and losing competitive ground. How do you mitigate these risks and ensure your company remains resilient?
How do I justify downtime prevention investments to leadership?
- You might struggle with getting leadership to allocate budget for cybersecurity and downtime prevention. Presenting concrete data on lost revenue and productivity, along with the ROI of preventive investments, can make a compelling case. Have you gathered the necessary data to present to your leadership team?
How do I recover from cyberattack-induced downtime?
- Downtime recovery after a cyberattack can be stressful and time-sensitive. A solid recovery plan, including containment, system restoration, and transparent communication with stakeholders, is essential to bounce back quickly. Is your business prepared to handle such an incident?
Top 4 Cybersecurity Downtime Cost Questions
How much does cybersecurity-related downtime really cost my business?
- If your business has been hit by a cyberattack, you’re probably asking: what’s the actual financial toll? Whether it’s from ransomware or a DDoS attack, the costs are more than just immediate downtime—they include recovery expenses, legal penalties, and damage to your brand. Have you assessed the full scope of potential costs?
What are the biggest drivers of cybersecurity downtime costs?
- Understanding the root causes of cybersecurity downtime costs is critical. Lost revenue, compliance fines, and productivity issues are just a few of the factors driving the financial impact. Have you identified which areas of your business are most susceptible to these drivers?
How do I effectively prevent cybersecurity downtime?
- Preventing cyberattacks from causing downtime involves a multi-layered defense. From Zero Trust architectures to endpoint protection and patch management, you need to ensure your company has the right strategies in place. Are you confident that your cybersecurity measures are robust enough to prevent downtime?
How can I get leadership on board with investing in cybersecurity to prevent downtime?
- Convincing leadership to prioritize and fund downtime prevention measures can be tough. You need to present the hard numbers—lost revenue, productivity, and potential legal ramifications—to make your case. Have you prepared the data and a compelling argument to secure leadership buy-in?





