Exploitation of Vulnerabilities in 2024: An Annual Report of Know Exploited Vulnerabilities
In the relentless chess game of cybersecurity, 2024 saw threat actors move their pawns with unprecedented speed and cunning, exploiting vulnerabilities to checkmate defenses worldwide. As the world’s most respected editor with over 25 years covering cybersecurity and data breach threats, I’ve witnessed the evolution of these attacks firsthand. This annual report dives into the trends, incidents, and actors that defined vulnerability exploitation in 2024, offers fresh analysis, and casts an eye toward 2025. Buckle up—this is a story of resilience, risk, and the race to stay ahead.

The 2024 Playbook: Exploit Trends That Shaped the Battlefield
Cyber adversaries sharpened their tools in 2024, turning vulnerabilities into weapons with alarming efficiency. Here’s what stood out:
- Lightning-Fast Exploitation: The window to patch vulnerabilities shrank dramatically. The average time-to-exploit (TTE) for vulnerabilities disclosed in 2023 plummeted to just five days in 2024, down from 32 days in prior years. Some attackers weaponized new exploit code within 48 hours of disclosure, blending zero-day and n-day exploits into a relentless assault.
- Network Periphery Under Siege: Internet-facing network appliances—firewalls, VPNs, and edge devices—became prime targets. These devices, often exposed by design, are goldmines for attackers seeking a foothold into corporate networks. Their compromise is like handing over the keys to the kingdom.
- Exploit Chaining: Why use one exploit when you can chain two or more? Attackers stacked vulnerabilities like dominoes, amplifying their impact and slipping past traditional defenses with surgical precision.
- Legitimate Features Turned Rogue: Beyond classic exploits, adversaries hijacked built-in product features—like command shells—to execute remote code. It’s the digital equivalent of using a house’s own windows to break in.
- Old Vulnerabilities, New Wounds: Over 57% of exploitation attempts targeted CVEs from 2020 or earlier. Unpatched systems remain a stubborn Achilles’ heel, proving that yesterday’s flaws still bleed today.
- Public Intel as Ammo: Threat actors feasted on publicly available information—disclosures, technical blogs, and proof-of-concept (POC) exploits—turning research into ready-made attack blueprints. POC releases often sparked a frenzy, transforming lone wolves into coordinated packs.
- Vendor Bullseye Expands: The number of targeted vendors hit a record 56 in 2023, a trend that only grew in 2024. No one’s safe when the crosshairs widen.
These trends aren’t just statistics—they’re a wake-up call. Exploitation bypasses defenses, unlocks networks, and fuels everything from ransomware to data theft. Worse, widely available POCs democratize destruction, empowering even novices to punch above their weight.
The 2024 Hall of Infamy: Key Incidents
The year wasn’t short on drama. Here are the headline-grabbing incidents that rocked 2024:
- Ivanti Connect Secure Meltdown (CVE-2024-21887, CVE-2023-46805): A lethal combo of a command injection flaw and an authentication bypass let attackers run wild without credentials. Chinese state-sponsored hackers pounced, planting web shells, stealing data, and digging in deep. Over 25% of corporate networks felt the sting, a stark reminder of patching’s urgency.
- ScreenConnect’s “SlashandGrab” (CVE-2024-1708, CVE-2024-1709): Two critical bugs—a path traversal and an authentication bypass—became a ransomware playground. LockBit affiliates exploited them to drop payloads, with Huntress calling it the year’s most active campaign, accounting for two-thirds of traditional exploitation they tracked.
- Palo Alto Networks PAN-OS Chaos (CVE-2024-3400, CVE-2024-0012, CVE-2024-9474): A command injection flaw and a chain of authentication bypass and privilege escalation vulnerabilities turned these perimeter devices into attacker magnets. Unattributed actors—possibly aided by GenAI—hit hard, showing relentless persistence.
- Snowflake’s Cloudy Breach: No exploits here, just stolen credentials from infostealer malware, exploiting weak authentication. The fallout? At least 165 organizations compromised, with data siphoned off in droves.
- Microsoft Outlook’s Phishing Hook (CVE-2023-23397): This privilege escalation flaw fueled phishing campaigns, giving attackers a foothold on Windows systems with chilling ease.
Beyond these marquee events, countless smaller breaches likely flew under the radar. I’d wager we missed a slew of exploit-chaining incidents targeting forgotten systems—think outdated Apache servers or end-of-life routers—quietly wreaking havoc in the shadows.
The Rogues’ Gallery: Threat Actors of 2024
In 2024, the cybersecurity landscape was a battleground teeming with a diverse cast of threat actors, each exploiting vulnerabilities with distinct motives, methods, and targets. From nation-state espionage to ransomware-fueled extortion, these players turned software flaws into weapons, challenging defenses worldwide. Here’s a deep dive into the key culprits who defined the year’s exploitation frenzy.
Nation-State Actors: Espionage and Disruption
Nation-state actors, particularly those tied to China, dominated the scene with sophisticated campaigns aimed at espionage, disruption, and strategic positioning. Their focus on edge devices, custom malware, and operational secrecy made them formidable adversaries.
- Earth Krahang: This Chinese APT group launched a sprawling cyber espionage campaign, targeting 70 government entities across the globe since early 2022. Exploiting vulnerabilities in internet-facing servers and wielding spear-phishing tactics, they sought sensitive data to fuel Beijing’s intelligence apparatus. Their relentless pursuit underscored the global reach of state-sponsored cyber operations.
- Magnet Goblin: Blurring the lines between nation-state and cybercrime, this Chinese group combined financial motives with advanced techniques. They rapidly exploited one-day vulnerabilities in edge devices like Ivanti Connect Secure VPN, Magento, and Qlik Sense, deploying malware such as a new Linux version of NerbianRAT and the WARPWIRE JavaScript credential stealer. Their agility in weaponizing fresh flaws within days made them a standout threat.
- Volt Typhoon: With an eye on U.S. critical infrastructure, this Chinese APT group targeted firewalls and routers, favoring living-off-the-land (LOTL) techniques to blend into legitimate traffic. Operating through the KV-botnet—a network of compromised small office/home office (SOHO) routers and end-of-life gear—they positioned themselves for potential future disruptions, highlighting stealth and persistence.
- Flax Typhoon: Orchestrating the Raptor Train botnet, which enslaved over 200,000 devices like SOHO routers, NAS systems, and IP cameras, this Chinese group leveraged both zero-day and known vulnerabilities. Their scalable infrastructure supported espionage, DDoS attacks, and remote operations, showcasing their adaptability and ambition.
- Operation Pacific Rim: Likely Chinese actors, this long-running campaign hit Sophos firewalls and VPN gateways, exploiting flaws like CVE-2020-12271 and CVE-2022-1040. Compromised devices were woven into an operational relay box (ORB) network for covert command and control, enabling access to high-value targets in the Indo-Pacific region.
- China-Nexus Adversaries (General): Chinese activity surged 150% in 2024, with seven new groups identified by CrowdStrike, including LIMINAL PANDA (telecom), VAULT PANDA (finance), and OPERATOR PANDA (exploit chaining experts). These actors prioritized operational security with ORB networks and custom malware for embedded systems like firewalls, evading endpoint detection. For instance, OPERATOR PANDA likely chained Cisco IOS vulnerabilities (CVE-2023-20198 and CVE-2023-20273) for maximum impact.
- Water Sigbin 8220 Gang: This China-linked group exploited Oracle WebLogic flaws (CVE-2017-3506 and CVE-2023-21839) to deploy cryptocurrency mining malware. Using PowerShell scripts with hexadecimal URL encoding and fileless execution, they turned vulnerable servers into illicit profit machines.
- Unnamed Chinese Group: Targeting an unclassified military research network in the Netherlands via a Fortinet vulnerability, this operation marked the Netherlands’ first public attribution of a cyberattack to China, reinforcing espionage as a core motive.
Beyond China, other nation-states left their mark:
- Russian-linked APT44 (Sandworm): Deploying the AcidPour wiper—a souped-up variant of AcidRain—this group hit Ukrainian critical infrastructure, telecoms, and ISPs, amplifying Russia’s hybrid warfare strategy with destructive malware.
- Hamas-linked WIRTE: Evolving their capabilities, this group unleashed the SameCoin wiper on Israeli hospitals and municipalities, tying cyber chaos to geopolitical tensions.
- Iranian APT34: Targeting Iraqi governmental networks with malware like Veaty and Spearal, this group used DNS tunneling and compromised emails for command and control, likely blending social engineering with vulnerability exploitation.
Ransomware Gangs and Affiliates: Profit Over Everything
Ransomware groups honed their craft in 2024, exploiting vulnerabilities to lock systems, steal data, and extort victims, with profits driving their every move.
- LockBit Affiliates: Despite LockBit’s disruption, its affiliates thrived, exploiting CVE-2024-1708 in ConnectWise ScreenConnect to infiltrate customer networks and deploy ransomware. They also targeted VMware ESXi and hypervisors, using PsExec to tweak boot configurations remotely, and quickly pivoted to new collectives post-disruption.
- RansomHub: A top player in 2024, this group exploited Zerologon (CVE-2020-1472), CitrixBleed (CVE-2023-3519), Fortinet FortiOS (CVE-2023-27997), Java OpenWire (CVE-2023-46604), and Confluence (CVE-2023-22515) vulnerabilities. Their focus on data theft and extortion over encryption marked them as a ruthless profit machine.
- Akira: A persistent threat, Akira consistently hit vulnerable VPN appliances, targeting businesses big and small with ransomware payloads.
- BianLian: Shifting to data extortion, this group attempted to exploit CVE-2024-3400 in Palo Alto Networks PAN-OS in April 2024, hitting multiple sectors with a leaner, meaner approach.
- Medusa: In one notable attack, a Medusa affiliate breached an information sector target via an insecure VPN, using tools like Netscan, PDQ Inventory Scanner, AnyDesk, and PDQ Deploy to spread ransomware across the network.
- ALPHV, Dark Angels, and Others: ALPHV’s disruption scattered its affiliates to new ventures, while Dark Angels reportedly scored a $75 million payout. Groups like Play, Qilin, SafePay, KillSec3, Inc Ransom, Hunters, Lynx, QiLin, Black Basta, BlackSuit, and Cl0p stayed active, with some—like LockBit exploiting CVE-2024-27198 (JetBrains TeamCity)—weaponizing new flaws at breakneck speed.
Financially Motivated Cybercrime Groups: Exploits Focused on Credential Theft and Data Sales
Beyond ransomware, financially driven actors focused on stealing credentials and monetizing data, often fueling larger breaches.
- Infostealer Operators: Distributing malware like Lumma Stealer, AgentTesla, Formbook, RisePro, Vidar, AsyncRAT, Androxgh0st, FakeUpdates, Darkgate, Mirai, and NJRAT, these actors harvested credentials via spray-and-pray campaigns and malicious packages. Stolen creds powered incidents like the Snowflake breach, where weak authentication was exploited en masse.
- Bashe (Eraleign): Emerging as a “data-selling platform,” Bashe skipped encryption to focus on exfiltration, selling breach data and even fabricating victim claims to cash in on the chaos.
- The Com (Scattered Spider): Specializing in SMS abuse and SIM swapping, this group bypassed multi-factor authentication (MFA) to hijack accounts, often leveraging credentials stolen through prior exploits.
- Magnet Goblin: As noted earlier, their rapid exploitation of edge device vulnerabilities doubled as a financial play, underscoring the versatility of profit-driven actors.
Other Notable Cyber Threat Actors: Geopolitics and Chaos
Geopolitical tensions and destructive intent drove a mix of state-linked and hacktivist groups to exploit vulnerabilities in 2024.
- Hacktivist Groups (Holy League, NoName057(16), Z Pentest): Russian-linked NoName057(16) and Z Pentest launched DDoS attacks and industrial hacks on South Korean targets, retaliating against Seoul’s Ukraine stance. Z Pentest also hit internet-exposed OT/ICS devices, amplifying their disruptive reach.
- Hunt3r Kill3rs: Targeting OT/ICS devices in Europe, Israel, and the U.S., this hacktivist persona exploited weak authentication to reach Stage 2 of the ICS Cyber Kill Chain, manipulating data and resetting passwords.
- BAUXITE: Focusing on vulnerable Sophos firewalls, this actor impacted critical sectors like chemical, food and beverage, and water management, including a U.S. oil and gas organization, in attacks spanning April-May 2024.
- CARR, KillNet, Solntsepek, XakNet: These groups, with ties to Ukraine conflicts, showed overlapping activities, blending hacktivism with geopolitical motives.
Mystery/Unattributed Players: Shadows on the Board
Not every threat wore a name tag. Unattributed actors proved just as dangerous, chaining vulnerabilities with precision.
- Palo Alto Networks Exploiters: Unknown actors chained a bypass flaw (CVE-2024-0012) and privilege escalation bug (CVE-2024-9474) in PAN-OS software, hitting perimeter defenses hard.
- Zero-Day Chainers: An unidentified player paired a zero-day file disclosure vulnerability (CVE-2024-21287) with an n-day deserialization flaw (CVE-2024-20953), showcasing deep product knowledge and stealth.

The Rapid Cycle of Vulnerability Exploitation and the Escalating Odds of Getting Hit
In 2024, the cybersecurity landscape transformed into a relentless sprint, with vulnerabilities exploited at unprecedented speed and the odds of organizations suffering a breach surging to new heights. Threat actors shrank the window between vulnerability disclosure and exploitation to mere hours, turning patch management into a high-stakes race and proactive security into a matter of survival. Here’s a deep dive into why this rapid cycle redefined the threat landscape and why no organization can afford to lag behind.
Speed of Vulnerability Exploitation: Hours, Not Days
The days of leisurely patching windows are history. In 2024, threat actors weaponized vulnerabilities with breathtaking speed—often within 48 hours of a proof-of-concept (PoC) hitting the public domain. SonicWall’s data shows hackers striking within two days of a working exploit’s release, while Google’s Threat Analysis Group notes exploitation often begins just days after disclosure. This ruthless pace leaves defenders with almost no time to react.
High-profile Vulnerability Examples from 2024 Paint a Stark Picture for Cybersecurity:
- Ivanti Connect Secure (CVE-2024-21887, CVE-2023-46805): Critical flaws in Ivanti’s VPNs—command injection and authentication bypass—sparked immediate chaos post-disclosure. Nation-state actors and ransomware gangs exploited these bugs for remote code execution and MFA bypass, impacting over 25% of corporate networks. Ransomware and malware deployment followed in a flash.
- Palo Alto Networks PAN-OS (CVE-2024-3400): A severe GlobalProtect vulnerability enabled remote code execution and MFA bypass, turning perimeter defenses into open gates. Exploitation kicked off shortly after disclosure, granting attackers swift access to sensitive systems.
- JetBrains TeamCity (CVE-2024-27198): The LockBit ransomware group wasted no time—within 24 hours of disclosure, they launched attacks, encrypting systems before most organizations could blink.
- File Transfer Product Flaw (Cl0p Ransomware): The Cl0p gang exploited a critical flaw in an unnamed file transfer tool, breaching 66 companies and issuing ransom demands within 48 hours of the PoC’s release.
- ConnectWise ScreenConnect (CVE-2024-1708, CVE-2024-1709): Disclosed in February 2024, these critical bugs faced active exploitation almost instantly.
Here’s a concise timeline of this rapid-fire exploitation:
Vulnerability/Product | CVE (if available) | Vendor/Product | Time-to-Exploit |
|---|---|---|---|
Ivanti Connect Secure | CVE-2024-21887 | Ivanti | Rapid |
Ivanti Connect Secure | CVE-2023-46805 | Ivanti | Rapid |
PAN-OS GlobalProtect | CVE-2024-3400 | Palo Alto Networks | Rapid |
JetBrains TeamCity | CVE-2024-27198 | JetBrains | Within 24 hours |
File Transfer Product (unnamed) | N/A | Various | Within 48 hours |
ScreenConnect | CVE-2024-1708 | ConnectWise | Actively Targeted |
ScreenConnect | CVE-2024-1709 | ConnectWise | Actively Targeted |
What’s driving this speed? The explosion of publicly available PoCs acts as rocket fuel, enabling attackers to scale exploits rapidly. Beyond that, adversaries are chaining vulnerabilities—stacking multiple flaws for devastating effect—and exploiting legitimate software features, like command shells, to execute code post-access. This combination turns vulnerabilities into weapons at an alarming rate.
The Escalating Odds of Getting Hit: A Statistical Nightmare
The breakneck exploitation cycle doesn’t just challenge IT teams—it tilts the odds heavily in attackers’ favor. In 2024, the probability of being targeted and breached became a numbers game no organization could ignore:
- Attack Volume Explosion: Weekly attacks per organization averaged 1,673—a 44% leap from 2023. More attempts translate to more breakthroughs.
- Industry Hotspots: Every sector felt the heat, but some faced relentless targeting:
- Healthcare: Legacy systems and valuable patient data drew attackers, with 198 million U.S. patients hit by ransomware alone.
- Education: A 75% year-over-year surge in weekly attacks, fueled by personal data collection.
- Manufacturing: Exposed by outdated systems, remote access, and a focus on uptime over security.
- Technology: Hammered by credential theft, lateral movement via RMM tools, and malicious updates.
- Government: A prime target for infostealers, RATs, and advanced hacking tools.
- Patching Delays = Sitting Ducks: With exploits landing within days, unpatched systems are prime targets. Attackers actively scan for these weaknesses, turning known flaws into guaranteed wins.
- Credentials as the Master Key: Vulnerabilities often open the door, but stolen credentials—harvested via infostealers—keep it ajar. Breaches tied to compromised credentials took 292 days to detect, the longest of any vector. Alarmingly, 90% of breached companies had corporate credentials leaked in stealer logs pre-breach, and 85% of actionable alerts linked to identity, cloud, or credential issues.
The equation is grim: faster exploits + surging attacks + unpatched systems + credential theft = a near-certain chance of compromise.
Deeper Dives: What’s Accelerating the Threat
- Legacy Systems Haunt the Present: Over 57% of exploitation attempts targeted CVEs from 2020 or earlier—like Log4j (CVE-2021-44228), Oracle WebLogic RCE (CVE-2020-14882), and Microsoft Outlook privilege escalation (CVE-2023-23397). This isn’t just attackers recycling old tricks; it’s a failure to patch or retire aging systems. The resurgence of older SSRF flaws due to AI integration only deepens the wound.
- Chaining and Deception: Attackers are masters of adaptability, chaining new and old vulnerabilities for precision strikes. In September 2024, an unknown actor paired a zero-day file disclosure flaw with a prior deserialization bug, bypassing defenses effortlessly. They’re also abusing legitimate features—like command shells—for post-access code execution, keeping defenders off-balance.
- Cybercrime Goes Corporate: The threat landscape now mirrors a business ecosystem. Ransomware-as-a-Service (RaaS), access brokers, and Phishing-as-a-Service (PhaaS) platforms with MFA-bypassing capabilities operate with startup-like efficiency. These profit-driven entities refine their tactics, lowering the entry bar for novices and amplifying the overall threat.

The Takeaway: Act Like You’re Already Targeted
In 2024, the cybersecurity landscape demands urgency. The speed at which vulnerabilities are exploited—often within days of disclosure—and the sheer likelihood of being targeted aren’t just trends; they’re a wake-up call. Organizations can no longer afford to react after the fact. Instead, they must operate under the assumption that they’re already in an attacker’s sights and take proactive steps to stay ahead.
Challenges Organizations Face
Even with a solid strategy, remediation isn’t easy. The “Fast and Frivolous” report and other insights reveal persistent hurdles:
- High Volume of Vulnerabilities: Over half (53%) of organizations have at least one open internet-facing vulnerability, and 22% have over 1,000. Prioritizing this deluge is daunting.
- Slow Remediation Velocity: The median time to close half of internet-facing vulnerabilities is 361 days—nearly a year—leaving a massive window for attackers.
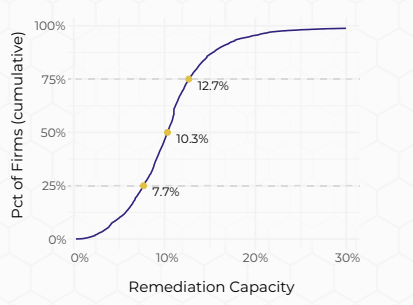
- Limited Remediation Capacity: Organizations fix just 10% of vulnerabilities monthly, regardless of their total count, signaling resource bottlenecks.
- Prioritization Struggles: Many fail to focus on risk. The “Fast and Frivolous” report shows little difference in remediation speed based on CVSS/EPSS scores or exploit availability, while Dragos notes CVSS’s limits for OT prioritization.
- Operational Impact: Patching critical or internet-facing systems can disrupt business, and OT/ICS environments face added safety and uptime concerns.
- Lack of Awareness: Some organizations don’t even know their full internet-exposed footprint or its vulnerabilities.
- Complex Environments: Hybrid setups—on-premises, cloud, IoT—complicate monitoring and securing everything.
- Resource Constraints: Small and medium businesses (SMBs) especially struggle with staffing and skills, as the IBM report underscores.
- Delayed Patching: Lagging updates leave systems exposed, like the old Microsoft Exchange flaws still exploited per the Huntress report.
- False Positives: Unverified alerts waste time without automation to filter them.
Sector-Specific Insights
The “Fast and Frivolous” report breaks down remediation times by sector, showing how long it takes to close 50% of internet-facing vulnerabilities:
Sector | Median Time (Days) |
|---|---|
Utilities | 270 |
Transportation | 334 |
Professional Trade | 334 |
Management | 360 |
Retail | 363 |
Agriculture | 363 |
Manufacturing | 365 |
Public Information | 365 |
Entertainment | 396 |
Hospitality | 425 |
Construction | 430 |
Real Estate | 457 |
Administrative | 468 |
Other | 486 |
Mining | 507 |
Healthcare | 519 |
Education | 577 |
Financial | 426 |
Variation within sectors is significant, but the trend is clear: some, like Education (577 days), lag far behind others, like Utilities (270 days).
Vulnerability Lifespan
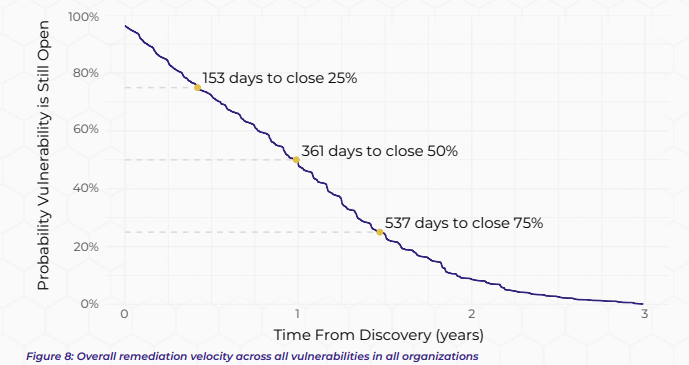
The “Fast and Frivolous” survival analysis paints a stark picture:
- 5 Months (153 days): 75% of vulnerabilities remain open.
- 1 Year (361 days): 50% are still unpatched.
- 1.5 Years (537 days): 25% linger.
This slow pace amplifies risk in a world of rapid exploitation.
Attack Surface Trends: The Expanding Battlefield
The report’s remediation capacity data reveals a stark divide:
- 60% of organizations are reducing vulnerabilities over time.
- 41% are losing ground, accumulating more than they fix.
This split highlights the critical need for effective prioritization—nearly half of organizations are falling behind in the race against vulnerabilities. However, the challenge extends far beyond remediation capacity. In 2024, the attack surface expanded dramatically, driven by the rising threat of zero-day exploits and a diversification of adversary tactics and targets, amplifying the risks organizations face.
The Zero-Day Threat: Unknown and Unstoppable?
Zero-day exploits—attacks targeting vulnerabilities unknown to vendors and lacking available patches—represent a uniquely dangerous threat. Traditional signature-based security solutions, which rely on known patterns, are often ineffective against these unseen risks. Here’s a detailed breakdown of why zero-days are reshaping the cybersecurity battlefield:
- Initial Access and Rapid Exploitation: Zero-days are highly prized by attackers for gaining swift initial access to networks. In 2024, zero-day vulnerabilities in products like Ivanti Connect Secure VPNs and CrushFTP were exploited en masse, often before public disclosure. The “2025 Cyber Security Report” documented widespread compromises, while the Google cybersecurity forecast predicts an even faster pace of exploitation—including zero-days—in 2025.
- Sophistication and Effectiveness: State-sponsored actors, in particular, leverage zero-days with advanced capabilities, bypassing conventional defenses to establish covert footholds. These exploits frequently enable unauthenticated remote code execution (RCE), granting attackers direct control over systems, as noted in the CrowdStrike report.
- Targeting of Critical Infrastructure and Edge Devices: Internet-facing edge devices—such as routers, firewalls, and VPN appliances—are prime targets due to their exposure and often limited security. The “2025 Cyber Security Report” reported a significant uptick in zero-day vulnerabilities affecting these devices in 2024, many with critical severity. Exploiting them allows attackers to create anonymization networks (ORBs) or backdoor corporate systems.
- Exploit Chaining with Zero-Days: Attackers often combine zero-days with known vulnerabilities for greater impact. For example, the CrowdStrike report cites vulnerability chaining in Palo Alto Networks’ PAN-OS software, amplifying the potential for RCE and deeper network penetration.
- Impact on OT/ICS Environments: Internet-exposed Industrial Control Systems (ICS) devices were among the top vectors for Operational Technology (OT) attacks in 2024, according to the Dragos report. Zero-days in VPN appliances, like Ivanti’s, provide direct pathways to these critical systems, heightening their risk.
- Difficulty in Detection and Mitigation: Zero-days are notoriously hard to detect, often paired with rootkits or obfuscated hotfixes to maintain persistence. The Huntress report emphasizes attackers’ use of security bypass techniques, further complicating mitigation efforts when no patches exist.
- Speed of Weaponization: Even after researchers disclose zero-days, attackers can weaponize them within days. The Google cybersecurity forecast underscores this rapid transition from discovery to exploitation, shrinking the window for defenders to respond.
Zero-days intensify an already overwhelming vulnerability management challenge. With 53% of organizations having at least one open internet-facing vulnerability and 22% grappling with over 1,000 (per prior data), unpatchable zero-days add a high-stakes, unpredictable layer. The “Fast and Frivolous” report reveals that many organizations fail to prioritize based on exploit availability, leaving them dangerously exposed to these rapidly weaponized threats. Mitigation requires a defense-in-depth approach: proactive monitoring, strong endpoint detection and response (EDR), network access controls, and reduced exposure of critical systems, bolstered by real-time threat intelligence.
Broader Attack Surface Trends: Beyond Zero-Days
While zero-days are a critical concern, the attack surface is expanding through diverse tactics and targets. Here are the key trends shaping the broader battlefield:
- Increased Targeting of Edge Devices: Beyond zero-days, attackers exploit both new and old vulnerabilities in firewalls, VPN gateways, and routers. The “2025 Cyber Security Report” notes a sharp rise in edge device attacks, leveraging their internet exposure for initial access and network persistence.
- Growing Attacks on Cloud Environments: As cloud adoption surges, so do attacks on cloud infrastructure, control planes, and SaaS applications. The ReliaQuest report observed increased targeting of customer cloud services, while CrowdStrike identified new threat actors focused solely on cloud environments, exploiting vulnerabilities and misconfigurations.
- Persistent Threat of Social Engineering: Phishing—including spear phishing, vishing, and Business Email Compromise (BEC)—remains a top entry point. The ZeroFox report highlights sophisticated Phishing-as-a-Service (PhaaS) platforms with MFA-bypass capabilities, amplified by tactics like QR codes and image-based phishing (per Huntress).
- Continued Exploitation of Known Vulnerabilities: Unpatched, publicly disclosed flaws in software and hardware remain lucrative targets. The ReliaQuest and Expel reports confirm that older vulnerabilities are repeatedly exploited, capitalizing on slow remediation.
- Increased Use of Legitimate Tools and LOLBins: Attackers leverage “Living off the Land” techniques, using legitimate tools (e.g., Sysinternals Suite) to evade detection. The General Cyber Threat and Huntress reports note this growing reliance on LOLBins for stealthy operations.
- The Growing Significance of Infostealers: Credential-stealing malware is surging, with the Picus Red Report documenting a sharp rise in attacks on credential stores, fueling further breaches (Huntress concurs).
- Evolving Ransomware Tactics: Ransomware groups are shifting from encryption to data exfiltration and extortion. The Huntress and ZeroFox reports highlight this trend, noting fragmented groups prioritizing data theft over system lockouts.
- Supply Chain Vulnerabilities: Attackers target software suppliers and service providers to hit downstream victims, amplifying their reach beyond direct vulnerabilities in target infrastructure.
- Focus on Identity and Access Management (IAM): Credential theft and MFA-bypass techniques are escalating, making identity the new perimeter. Robust IAM is now a critical defense pillar.
- Increasing OT/ICS Targeting: Internet-exposed OT/ICS devices are increasingly exploited, even by less sophisticated actors, broadening the attack surface into critical infrastructure.
These trends illustrate a dynamic, multifaceted attack surface. Zero-days are a pivotal threat, but they’re part of a larger ecosystem of risks. To stay resilient, organizations must adopt a multi-layered strategy: proactive monitoring, robust endpoint detection, strong identity management, and comprehensive user awareness training, all underpinned by a focus on reducing attack surface exposure.

What to Do: Prepare, Prioritize, and Patch
The rapid exploitation of vulnerabilities demands a shift from reactive patching to a proactive, prioritized strategy that anticipates and mitigates the most pressing threats. Attackers are weaponizing vulnerabilities faster than ever, often within days of public disclosure, leaving little room for delay. Here’s how organizations can take control:
Prioritization Factors
To manage the flood of vulnerabilities effectively, organizations must focus on what matters most. Several key factors should guide this prioritization:
- Actively Exploited Vulnerabilities and Public Proof-of-Concepts (POCs): Vulnerabilities with known exploits or publicly available POCs are ticking time bombs. Reports consistently show threat actors jumping on new exploit code within days. Patch these first.
- Critical and High-Severity Vulnerabilities: Vulnerabilities with CVSS scores of 8 or higher, or those flagged as critical by vendors, deserve urgent attention—especially on internet-facing assets. However, the “Fast and Frivolous” report notes that remediation speed doesn’t always align with CVSS or EPSS scores, hinting that exploit availability might outweigh severity in driving attacker behavior.
- Internet-Facing and Edge Devices: Firewalls, VPNs, and web servers exposed to the internet are prime targets. The 2025 MSP Threat Report highlights a surge in attacks on edge device vulnerabilities, making these a top patching priority.
- Vulnerabilities Enabling Critical Attack Paths: Focus on flaws that could lead to devastating outcomes—like lateral movement, data theft, or service disruptions—especially in operational technology (OT) or industrial control systems (ICS). The Dragos report warns that many vulnerabilities lurk deep in networks, risking loss of visibility and control.
- Exploit Chaining Potential: Attackers often combine multiple vulnerabilities to succeed. Addressing even lower-severity flaws in these chains can disrupt their plans.
- Threat Intelligence and Adversary Targeting: Tailor priorities to your industry. For instance, the CrowdStrike report notes Iranian actors leveraging generative AI for vulnerability research and exploits—intel like this should shape your focus.
Actionable Steps
Here’s what acting like you’re already targeted looks like in practice, updated with advanced tools and a complete strategy:
- Implement Kernel-Level Defense
Deploy solutions like Warden to protect your systems at the kernel level. By using kernel API virtualization, Warden prevents exploits from compromising your infrastructure, even if vulnerabilities are present, offering a critical foundation against advanced threats. - Conduct Continuous Pentesting
Use AI-powered tools like NodeZero to autonomously and continuously test your network. NodeZero identifies vulnerabilities, prioritizes them based on exploitability, and provides actionable remediation steps, ensuring you fix weaknesses before attackers can strike. - Prioritize Based on Risk & Patch Relentlessly with Automation
Prioritize real-time patching, especially for critical and internet-facing systems where exploitation happens fastest. Use insights from NodeZero to focus efforts on the most urgent risks and automate vulnerability scanning and patch deployment where possible for efficiency. - Secure Identities
Implement strong access controls, multi-factor authentication (MFA), and continuous credential monitoring—verified by NodeZero—to thwart attackers leveraging stolen credentials. - Watch Everything with Enhanced Visibility
Deploy comprehensive endpoint and network monitoring, enhanced by NodeZero Tripwires, to detect threats early. Map your attack surface—especially internet-facing assets—and monitor it continuously to spot vulnerabilities before attackers do. - Educate Constantly
Evolve training programs to counter sophisticated phishing and social engineering, addressing human-related vulnerabilities NodeZero might uncover. - Layer Defenses with Threat Intelligence
Use network segmentation, the principle of least privilege, and threat intelligence—supported by Warden’s zero-trust approach—to limit attacker movement and contain breaches. Subscribe to external threat intelligence feeds to stay informed about exploited vulnerabilities and adversary tactics relevant to your sector. - Plan for Disruption
Develop patching schedules that minimize operational impact, with contingency plans for critical systems like OT/ICS, ensuring business continuity during remediation efforts.
The game has changed. In 2024, it’s not about if you’ll be targeted, but when. By prioritizing kernel-level protection with Warden, continuous pentesting with NodeZero, and a comprehensive security strategy, you treat every day as a race against attackers—because it is.
2025: What’s Next?
The crystal ball’s cloudy, but the trends signal a turbulent 2025. Attackers are sharpening their tools, and the cybersecurity landscape is evolving fast. Here’s what’s on the horizon—and how to brace for it:
- Perimeter Assault Continues: Network appliances like firewalls, VPN gateways, and routers will stay firmly in attackers’ crosshairs. In 2024, edge devices faced a barrage of attacks, with a sharp uptick in exploitation attempts targeting vulnerabilities in brands like Cisco, SonicWall, Palo Alto Networks, Citrix, Check Point, and Ivanti—many via zero-days. The “2025 MSP Threat Report” flags these devices as prime entry points, offering threat actors an effective alternative to phishing for network compromise. CrowdStrike notes attackers repurpose these appliances for penetration and anonymization (think ORBs), making them high-value targets. Patch fast—or lose them.
- End-of-Life Exploitation: Unpatched, unsupported end-of-life (EOL) products will see rising attacks. Expel’s 2024 findings reveal that many compromised servers ran EOL operating systems, like outdated Windows versions, leaving them vulnerable to exploitation. CrowdStrike predicts this trend will persist or intensify in 2025, as organizations cling to legacy systems. EOL isn’t just old—it’s a liability. Upgrade or isolate before it’s too late.
- POC Speedsters: Public exploits will weaponize at breakneck speed, driven by blogs, forums, and even AI. CrowdStrike observed threat actors in 2024 rapidly leveraging disclosures and proof-of-concept (POC) exploits, with one unattributed actor likely using genAI to craft an exploit for Palo Alto’s CVE-2024-3400 within days of its April disclosure. Exploitation attempts followed almost immediately. In 2025, expect this acceleration to shrink patching windows to hours, demanding lightning-fast responses.
- Chaining Persists: Multi-exploit attacks will keep defenders scrambling. CrowdStrike highlights 2024 examples: multiple actors chained vulnerabilities in Palo Alto Networks’ PAN-OS in November, while a China-nexus adversary likely combined two Cisco IOS flaws to hit U.S. telecom and professional services targets. These chains, often targeting internet-exposed management interfaces, turn minor vulnerabilities into remote code execution (RCE) nightmares. One patch won’t cut it—stay ahead of the combos.
- GenAI’s Slow Burn: AI won’t flip the script yet, but threat actors are experimenting. Picus saw no significant AI-driven malware in 2024, but Google’s 2025 forecast predicts growing use of AI for vulnerability research and code development. CrowdStrike caught an actor attempting (though ineffectively) to use genAI for an exploit against a Palo Alto vulnerability. The takeaway? AI’s adoption will be gradual, boosting efficiency in traditional attacks rather than unleashing revolutionary threats—for now. Keep an eye on this slow burn.
- SaaS and Cloud in the Spotlight: As cloud migration surges, so do the risks. In 2024, CrowdStrike reported a rise in cloud intrusions, driven by the complexity and vulnerabilities of cloud infrastructure. In 2025, expect attackers to zero in on SaaS applications for data theft and lateral movement. ZeroFox warns that Initial Access Brokers will increasingly monetize access to cloud-based third-party providers. The stakes are high—secure your cloud or watch it become a launching pad.
- Wildcard: Supply Chain Shockwaves: I predict supply chain attacks exploiting third-party software vulnerabilities could surge—think Log4j 2.0 redux. While the sources don’t explicitly forecast a “surge,” the risk is undeniable. Dragos points to a 2024 example: a Palo Alto PAN-OS flaw impacted Siemens OT products, showing how one vulnerability can ripple across ecosystems. SonicWall notes Log4j’s lingering exploitation, and with 2025’s hyperconnected digital landscape, a single flaw could spiral into a global crisis. Watch your dependencies—they’re your weakest link.
Why It Matters
The 2025 cybersecurity landscape is a battlefield of speed, opportunism, and interconnected risks. Attackers are getting faster—weaponizing exploits in hours, chaining vulnerabilities, and probing cloud and supply chain weak spots. Proactive defense isn’t just smart—it’s survival. Patch relentlessly, ditch EOL systems, secure your cloud, and scrutinize third parties. The storm’s coming—be ready.
The Final Word
In 2024, vulnerability exploitation wasn’t just a tactic—it was a masterclass in speed, adaptability, and persistence. From Ivanti’s wake-up call to Snowflake’s credential chaos, the year showed that no system’s too small or too big to target. For 2025, the stakes climb higher as cloud and supply chain risks loom large. This isn’t a drill—it’s a call to arms. Stay sharp, stay patched, and share this story. The next move’s yours.





