CISA Warns of Hackers Breaching Ivanti Vulnerable Systems offline due to exploit impacting Chemical Security Tool, Exposing Sensitive Data
The CISA Ivanti Incident
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert about a significant cybersecurity breach targeting the Chemical Security Assessment Tool (CSAT). Highlighting that the Cybersecurity and Infrastructure Security Agency (CISA) recently faced a significant security breach involving its Chemical Security Assessment Tool (CSAT). The breach, occurring between January 23-26, 2024, involved Advanced Persistent Threat (APT) actors deploying a web shell on a vulnerable Ivanti Connect Secure and Policy Secure Gateways. The hackers breached the chemical sector potentially through exposed sensitive data from Top-Screen surveys, Security Vulnerability Assessments, Site Security Plans, and Personnel Surety Program submissions, affecting approximately 100,000 users.

What Happened
APT actors exploited a known vulnerability to install a web shell on CISA’s CSAT, allowing unauthorized access to highly sensitive data. This breach was particularly alarming given the nature of the data involved, which includes detailed information on the storage and security of dangerous chemicals, making it a potential target for state-sponsored actors with geopolitical motives.
Timeline of Cyber Hacker Breaching CISA Chemical Security Assessment Tool (CSAT)
July 28, 2023:
- Congress allows the CFATS program to lapse, terminating CISA’s regulatory authority over chemical facility security measures.
August 2023:
- CISA through action or inaction, leaves infrastructure operational that is connected to the CSAT tool.
December 2023:
- Initial activity around vulnerabilities observed. Indicators of potential exploits by Chinese state-sponsored actors noted. Volexity initially detected threat activity in mid-December but later traced exploits back to Dec. 3 according to Cybersecurity Dive on 11 Jan 2024
Early January 2024
- Ivanti Vulnerability Disclosure: Ivanti announced a critical vulnerability in its Connect Secure and Policy Secure Gateways its Endpoint Management Software (EPM), allowing for remote code execution (RCE) (TechRadar).
January, 11, 2024
- CISA said it applied Ivanti’s recommended mitigation measures on Jan. 11 and used Ivanti’s integrity checker tool daily to hunt for potential compromises.
January 19, 2024
- CISA issued Emergency Directive 24-01 in response to the vulnerabilities, directing federal agencies to implement mitigations and report any signs of compromise (CISA).
January 22, 2024
- Zero-Day Exploit Identified: Ivanti disclosed additional vulnerabilities, including a zero-day exploit tracked as CVE-2024-21888, the day before the breach began (TechRadar).
January 23-26, 2024
- Breach Occurrence: Hackers breached the chemical sector through the Chemical Security Assessment Tool (CSAT) environment by exploiting Ivanti vulnerabilities in an Ivanti Connect Secure device used by CISA. The attackers deployed a web shell, which allowed them to access and potentially expose sensitive data, including Top-Screen surveys, Security Vulnerability Assessments, Site Security Plans, and Personnel Surety Program submissions (BleepingComputer) (BleepingComputer).
January 31, 2024
- CISA released guidance to no later than 11:59PM on Friday February 2, 2024, disconnect all instances of Ivanti Connect Secure and Ivanti Policy Secure solution products from agency networks.
- By June 1, 2024, CISA will provide a report to the Secretary of Homeland Security, the National Cyber Director, the Director of the Office of Management and Budget, and the Federal Chief Information Security Officer identifying cross-agency status and outstanding issues.
February 1, 2024
- Cyberscoop reports that CISA orders Ivanti devices targeted by Chinese to be disconnected
February 12, 2024
- CISA Releases guidance on patching Ivanti CVEs, that were released on 8 Feb 2024.
February 29, 2024
- CISA, in collaboration with FBI and international partners (e.g. NCSC-UK), released a joint advisory highlighting the exploitation of Ivanti vulnerabilities and providing detailed guidance for mitigation (CISA).
March 4, 2024
- Reports surfaced that Chinese state-sponsored hackers were actively exploiting these vulnerabilities. The hacking group APT41 (also known as Barium) was identified as the primary actor behind these attacks (CISA).
March 8, 2024
- Confirmation by CISA: The Record first reported the breach, revealing that CISA took two systems offline—CSAT and the Infrastructure Protection (IP) Gateway—while investigating the incident. These systems contained critical information about chemical security and U.S. infrastructure interdependencies (The Record). CISA confirmed the breach publicly. They acknowledged that vulnerabilities in the Ivanti products were exploited and confirmed the temporary offline status of the affected systems. The agency assured there was no operational impact at that time (TechRadar).
April 1, 2024
- More than 100,000 individuals were noted by the Cybersecurity and Infrastructure Security Agency to possibly have been affected by a cyberattack against its Chemical Security Assessment Tool involving the exploitation of security vulnerabilities in Ivanti appliances, reports CyberScoop on March 29, 2024.
April 2, 2024
- Cybersecurity Dive stated “CISA asserts no data stolen during Ivanti-linked attack on the agency Threat actors gained access to and potentially compromised two CISA systems weeks after the agency applied Ivanti’s initial mitigation measures.”
- CISA asserts no data stolen during Ivanti-linked attack on the agency, “despite no evidence of data exfiltration, the number of potential individuals and the nature of the data that could have been exposed in the CSAT system met the threshold of a major incident under the Federal Information Security Management Act,” the spokesperson said. (Security Dive)
- However, hackers bypassed Ivanti’s fixes. CISA said it applied Ivanti’s recommended mitigation measures on Jan. 11 and used Ivanti’s integrity checker tool daily to hunt for potential compromises. The threat actor circumvented the mitigations and Ivanti’s integrity checker tool, the CISA spokesperson confirmed.
June 20, 2024
- CISA released letters to stakeholders (companies) information may have been compromised along with user PII information.
- Company Letter: https://www.cisa.gov/sites/default/files/2024-06/csat-incident-notification-letter-stakeholders_508.pdf
- Individuals Letter: https://www.cisa.gov/sites/default/files/2024-06/csat-incident-notification-letter-individual_508.pdf
- Our Assessment: Why all along, not acknowledge this hack, deny exploits then release 100,000 letters to potentially affected companies and individuals 5-months later? We get into our concern below.
June 21, 2024
- The US Cybersecurity and Infrastructure Security Agency (CISA) has reported a breach of its Chemical Security Assessment Tool (CSAT) by a malicious actor, warning chemical facilities that sensitive data might have been compromised. Although there is currently no evidence of data exfiltration, CISA has notified individuals whose personally identifiable information (PII) was submitted for vetting or who had a Chemical-terrorism Vulnerability Information (CVI) Authorized User account that their data might have been accessed. CISA recommends all CSAT account holders reset their passwords to safeguard against brute force attacks. (Infosec-Magazine)
June 24, 2024
- Public Warning: CISA issued a public warning and began notifying impacted entities. Although CISA stated there was no direct evidence of data theft, the potential risks prompted them to notify companies and individuals involved in the CFATS program. They recommended resetting passwords and emphasized the importance of timely security updates (TechRadar).
Hacker Attack Methodology:
The attackers, identified as part of a Chinese APT group known as APT41, leveraged known Ivanti vulnerabilities in the Ivanti Connect Secure appliance. They deployed a web shell to gain unauthorized access. Over two days, they accessed the web shell multiple times before CISA detected the breach and took the affected systems offline (TechRadar) .
The hackers breached the chemical sector by leveraging known vulnerabilities in the Ivanti Connect Secure appliance, deploying a web shell to gain unauthorized access. Over two days, they accessed the web shell multiple times before CISA detected the breach and took the affected systems offline. As, “Wales said their examination of the incident revealed that the attackers deployed a webshell against the CSAT tool and that there was “a loss of control in the system,” further pushing the agency to make disclosures to Congress.” The vulnerabilities exploited included remote code execution flaws that allowed the attackers to install the web shell and conduct their activities undetected for several days (Cyberscoop).
Attribution and Context
APT41, also known as Barium or Winnti, is a Chinese state-sponsored cyber espionage group known for conducting a range of cyber activities, including espionage, financial theft, and supply chain attacks. More information about APT41 can be found here (TechRadar). While the exact identity of the attackers remains unknown, the incident has characteristics typical of advanced persistent threats (APTs). Given the nature of the data and systems involved, the breach has raised concerns about state-sponsored actors being behind the attack, potentially driven by geopolitical motives (Infosecurity Magazine).
Attackers’ Step-by-Step Approach
- Reconnaissance: Attackers identified vulnerable systems within CISA’s network.
- Exploitation: They exploited a known vulnerability to deploy a web shell.
- Establishing Persistence: The web shell allowed attackers to maintain persistent access.
- Data Access: Unauthorized access to sensitive data, potentially leading to data exfiltration.
- Covering Tracks: Efforts to minimize detection by avoiding significant disruptions that might alert CISA.
Key Failures and Impact
- Vulnerability Management: The breach exploited known vulnerabilities, highlighting lapses in timely patch management.
- Incident Detection and Response: The delay in detecting the breach allowed the attackers multiple accesses over several days.
- Communication and Transparency: Initial reports and public confirmations were delayed by 4-months from public awareness of event, but 5-months from breach date, thus impacting public trust and preparedness among affected entities.
What Was Compromised
According to CISA and analysts, the breached data included:
- Top-Screen surveys
- Security Vulnerability Assessments
- Site Security Plans
- Personnel Surety Program submissions
These documents contain highly sensitive information related to chemical facility security and vulnerabilities, making them valuable targets for state-sponsored actors with geopolitical motives (TechRadar) (BleepingComputer) (BleepingComputer).
New Reporting Criteria
In response to this incident, CISA has updated its reporting criteria for cybersecurity incidents in the chemical sector. Organizations are now required to:
- Report any suspected breaches within 24 hours of detection.
- Provide detailed incident reports, including the nature of the breach, affected systems, and potential impact.
- Implement and report on immediate mitigation measures.
Impact on Organizations
The new reporting criteria will have significant implications for organizations at risk:
- Increased Compliance Requirements: Organizations must enhance their incident detection and reporting capabilities.
- Regulatory Scrutiny: Failure to comply with the new reporting criteria may result in increased regulatory scrutiny and potential penalties.
- Operational Adjustments: Companies may need to adjust their operational protocols to ensure compliance with the updated requirements.
Recommended Actions
- Immediate Review: Organizations using the compromised tool should immediately review their security protocols and ensure all sensitive data is secured. Identify and patch vulnerabilities within your network. Look at how to continue to upgrade and modernize to increase resilience to reduce high-risk vulnerabilities, especially from Chinese hackers.
- Incident Response Plans: Update and test incident response plans to ensure rapid and effective response to any potential chemical-related incidents.
- Adopt Multi-Factor Authentication (MFA): Ensure MFA is enabled for all critical systems.
- Enhanced Monitoring: Implement enhanced monitoring and threat detection measures to identify and mitigate any further attempts at unauthorized access.
- Zero Trust Security Model: Consider adopting a Zero Trust security model to limit access to sensitive information and reduce the risk of future breaches.
Failures of CISA
The hackers breached the chemical sector through CISA’s failure to patch known Ivanti vulnerabilities in a timely manner played a critical role in this breach. The lack of robust security measures and proactive monitoring allowed attackers to exploit these weaknesses, leading to unauthorized access and potential data exposure. This incident underscores the importance of stringent cybersecurity practices and regular updates to safeguard against such threats. These are the normal concerns about every other compromise.
This is different however, the more we look the more we have concerns. From CISAs own website about CFATS:
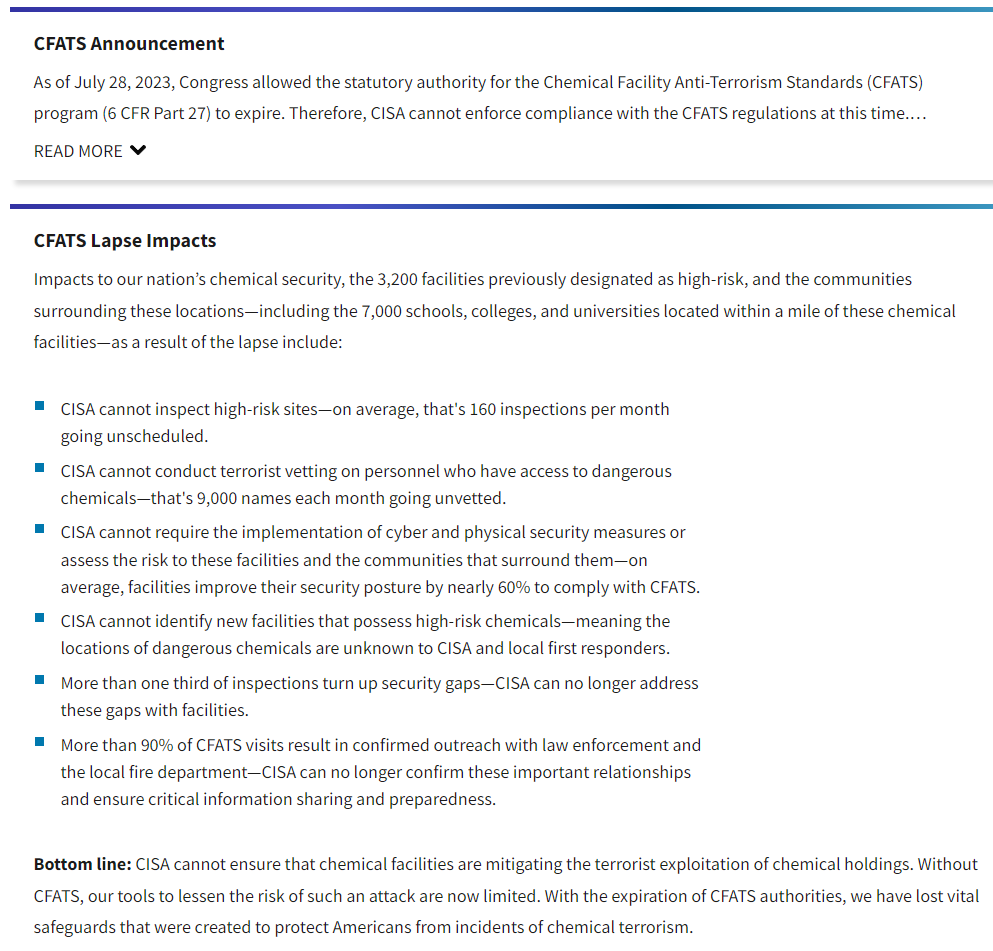
Why It Matters
The breach’s potential to expose critical infrastructure data is highly concerning. This breach underscores the importance of robust cybersecurity measures in the chemical industry. The exposed data could be used by malicious actors to orchestrate attacks on chemical facilities, posing severe risks to public safety and national security. Unauthorized access to chemical security information can lead to catastrophic consequences, including targeted attacks on chemical facilities. This situation highlights the critical need for organizations to adopt a proactive cybersecurity posture, regularly update their systems, and adhere to strict incident response protocols.
Critical Infrastructure Sector: Chemical Industry
This alert primarily concerns the chemical industry, particularly those facilities dealing with hazardous materials and chemicals that pose significant risks to public health and safety.
Criticality Score: 10/10
This breach by hackers breached the chemical sector has been classified with a criticality score of 10/10 due to the potential for severe impact on public safety and national security. The compromised data includes sensitive information essential for preventing and managing chemical-related incidents.
Why: 3,200 High Risk Chemical Facilities and 100,000 users
Vulnerabilities Released:
- Top-Screen surveys
- Security Vulnerability Assessments
- Site Security Plans
- Personnel Surety Program submissions
Actor: Chinese APT
Threats:
- Phishing
- Spearphishing
- Direct Cyberattacks using vulnerability data disclosed
Potential Impacts:
- Potential to hold at Cyber risk 20% of the US National Chemical Facilities and 100% of all high risk Chemical Facilities.
- Ransom, Extortion, or ability to create insider threats to anywhere these 100,000 users are from
Concerns:
The breach of CISA’s Chemical Security Assessment Tool (CSAT) could have severe consequences for the chemical sector. It places at risk a sector generating $639 billion annually, representing over 20% of the national GDP related to chemicals. Sensitive data, including security vulnerability assessments and site security plans, were potentially exposed. This compromises the integrity of security protocols across 3,200 facilities and endangers 100,000 individuals’ personally identifiable information (PII). If malicious actors leverage this information, it could lead to targeted attacks on chemical facilities, posing substantial risks to public safety, operational integrity, and national security. Moreover, the breach undermines trust in CISA’s ability to protect critical infrastructure, prompting urgent calls for improved cybersecurity measures and incident response protocols. The threat is magnified by the involvement of sophisticated nation-state actors, like those from China, who could leverage this data for strategic and malicious purposes. This incident underscores the need for robust cybersecurity measures and rapid response protocols to protect critical infrastructure. Thus, having all the vulnerability information from site security plans, vulnerability assessments and personal information a threat actor has all the intelligence they need to systematically attack these facilities at a time and choice of their choosing.
How Warden Can Help
Warden offers robust protection by combining advanced threat detection, real-time monitoring, and a comprehensive Zero Trust security framework. This approach ensures that only authorized users have access to sensitive data, significantly reducing the risk of breaches. We do this through a kernel level defense that stops all changes from impacting the binaries (code) of the software and operating systems you leverage for day to day operations. This is fully managed 24x7x365 by a team that is leveraging threat intelligence to actively hunt adversaries activity to ensure redundant security measures are in place to defend you systems.
Learn more about Warden and how it can fortify your cybersecurity defenses at Cyber Strategy Institute.
Summary of CISA Hacker of Ivanti Breach
The CISA alert about the hackers breach of the chemical sector through the chemical security tool highlights the critical importance of cybersecurity in the chemical industry. With sensitive data exposed, the potential for severe public safety risks is high. Organizations must act immediately to review and enhance their security measures, comply with new reporting criteria, and consider adopting a Zero Trust security model to mitigate future risks. Warden provides a robust solution to safeguard against such breaches and protect sensitive data.
Stay vigilant and ensure your security measures are up-to-date to protect against evolving cyber threats.





