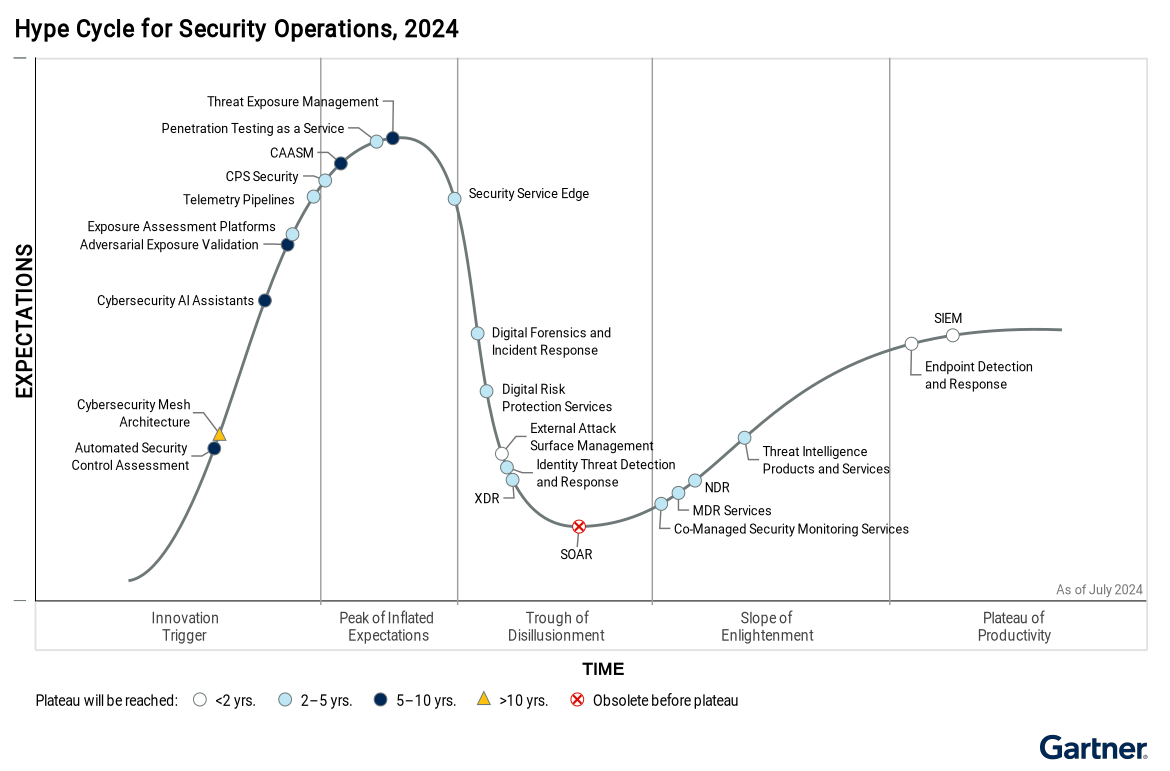
Why Automated Security Control Assessment (ASCA) Is the Key to Unlocking Your Cyber Resilience in 2024
The Future of Automated Security Control Assessment (ASCA): Filling the Gaps in Gartner’s Hype Cycle In 2024, Gartner highlighted Automated Security Control […]
Cybersecurity in Healthcare Merger and Acquisition (M&A): Managing Risks to Ensure Successful M&A Integration and ROI
The Critical Importance of Due Diligence in Healthcare M&A: Safeguarding IT Assets and Mitigating Cybersecurity Risks As healthcare systems increasingly pursue mergers […]

How to Calculate the Cost of Downtime from IT to Cybersecurity Breach: A Complete Guide for 2024 on the True Cost of Downtime
The True Cost of Downtime and Data Breaches in 2024: What Small Businesses Need to Know In today’s fast-paced digital world, nothing […]

Advanced Pentesting with Horizon3.ai: How NodeZero Tripwires™ Neutralize Attack Vectors
The Cyber Battle You Can’t Afford to Lose: How Pentesting and NodeZero Tripwires™ Can Save Your Network In today’s digital landscape, your […]

Navigating Zero Trust Security Solutions and Their Boundaries: Tough Questions Every Enterprise Should Ask in order to Implement Zero Trust
Key Considerations for Selecting and Avoiding Common Pitfalls in Implementing Zero Trust Security Solutions In today’s rapidly evolving cybersecurity landscape, Zero Trust […]
In the Cybersecurity Crosshairs – The Unseen Cyber Battles of Today’s CISOs
A Disturbing Trend: Boards Dismissing CISOs Spells Trouble for Cyber Security Leaders The recent findings published by Merlin Namuth shed light on […]

Can a Zero Trust Architecture Be Implemented “Out of the Box”?
Unlocking Zero Trust Architecture: Beyond Conventional Cybersecurity Thinking to Implement “out of the box” Zero Trust Security Embark on a transformative journey […]
7-Things about the Zero Trust Security Model That Most Don’t Understand
Here are the top 7 things about Zero Trust Security that most people don’t understand in Cybersecurity: Zero Trust is a pivotal […]

The Holy Grail of Cybersecurity: Can We Stop Cyber Hacks Instantly?
Cybersecurity’s Foundational Approach to Risk, Best Practices, and Strategies such as Zero Trust stopping hacks with the Holy Grail of Security! Understanding […]

Unraveling Cybersecurity: A Critical Reassessment of Traditional Solutions to Protect Your Company
Unraveling Cybersecurity: Rethinking Traditional Solutions to Protect Your Business Cybersecurity strategies for business continuity are crucial for businesses in today’s landscape, with […]

