EDRs Aren’t Stopping RATs: A Data-Driven Reality Based on 50,000 Pentests and a Look at Warden’s Next-Generation Defense
Modern security teams invest heavily in Endpoint Detection and Response (EDR) solutions, largely because these tools promise to thwart some of the most dangerous post-exploitation activities—namely, the deployment of Remote Access Tools (RATs). A RAT in the hands of an attacker is a powerful asset that can facilitate:
Persistence – Remaining active even after reboots.
Privilege Escalation – Exploiting vulnerabilities and misconfigurations local to the compromised host.
Credential Harvesting – Dumping credentials (LSA, LSASS, SAM, DPAPI, etc.) and authentication tokens.
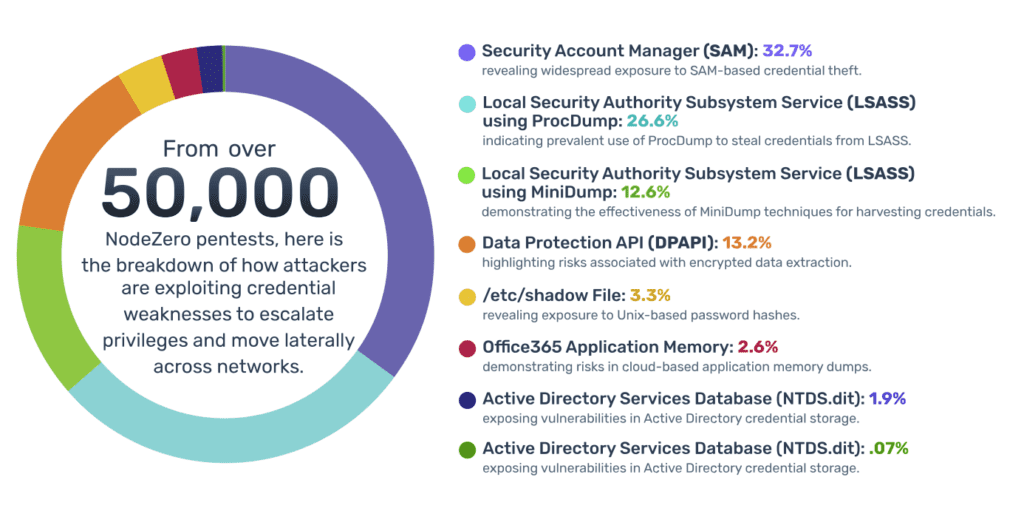
Given the critical role EDRs play in preventing and containing RATs, one would expect these solutions to detect such a blatant threat reliably. However, data from over 60,000 pentests conducted by NodeZero over the past year reveals a surprising gap between expectation and reality.
In these tests, the NodeZero RAT—deployed on both Windows and Linux machines—operates in an extremely “loud” manner with no special EDR evasion techniques. Despite this conspicuousness, multiple leading EDR products frequently failed to detect, contain, or eradicate the RAT. Below, we examine the numbers and discuss why these findings should prompt security teams to reevaluate their assumptions about EDR efficacy.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.

The Data: EDR Vendors and Their Success Rates
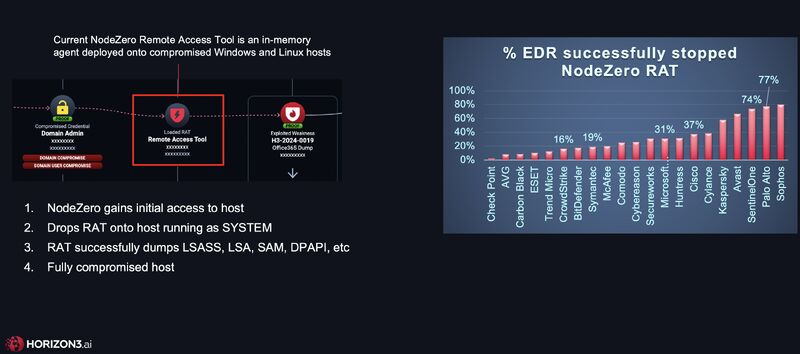
The chart below highlights the approximate success rates at fully detecting, containing, and eradicating the NodeZero RAT during Windows pentests. Success rate here refers to the percentage of time the EDR effectively stopped the RAT before it could carry out credential dumping or other malicious actions.
|
Note: These success rates are derived from real-world pentest data. Each organization’s mileage may vary depending on policy configurations, environment, and product version.
Why These Findings Are Concerning
The RAT data alone is unsettling—no single EDR solution reached a 100% detection and containment rate, despite the RAT being deliberately “noisy.” However, these results are even more alarming when viewed alongside the broader insights from the Horizon3 AI Annual Insights Report 2025, which surveyed nearly 800 CISOs and IT practitioners and analyzed data from over 50,000 penetration tests. Here’s how the RAT findings connect to the report’s top takeaways:
Reactive Cybersecurity is Failing
The report underscores that traditional, reactive approaches simply can’t keep up with modern attackers, who iterate faster than defenders can respond. The RAT success rates illustrate this gap: by the time an EDR reacts, the attacker has already harvested credentials or escalated privileges.
Vulnerability Scanning Isn’t Working
Nearly 98% of organizations use some form of vulnerability scanning, yet only 34% find it highly effective. The sheer volume of alerts and false positives creates analysis paralysis, leaving teams overwhelmed and unable to focus on critical threats like a live RAT. If organizations are drowning in vulnerability scan alerts, they’re even less likely to notice stealthy post-exploitation activity.
Weak Credentials and Excessive Permissions Remain a Problem
Credential dumping was successful in a significant number of NodeZero pentests. Attackers often gain entry by simply logging in with stolen credentials—an issue that an underperforming EDR won’t necessarily catch. The RAT data highlights how easily attackers escalate privileges once they’re in.
Patch Overwhelm Extends the Attackers’ Window
Over 53% of practitioners and 36% of CISOs admit to delaying patches, giving attackers a comfortable timeframe to exploit known vulnerabilities. Coupled with EDRs that fail to detect RATs, this extended window of opportunity is a recipe for disaster.
Poor Security Plaguing Cloud Infrastructure
The report shows that many organizations don’t regularly test their cloud environments or skip pentests altogether. If your on-prem EDR struggles with RAT detection, it’s likely your cloud defenses have similar blind spots—especially with common misconfigurations and weak IAM controls.
Teams Failing to Reduce Mean Time to Remediation (MTTR)
While 61% of organizations acknowledge MTTR’s importance, 31% struggle with remediation due to resource constraints. An EDR that fails to contain a RAT promptly further inflates the MTTR, allowing attackers more time to pivot and expand their foothold.
Low Trust in Manual Pentests
Many organizations find third-party pentest reports unreliable or not actionable, preferring continuous validation solutions like NodeZero. However, the data clearly shows that even if you discover vulnerabilities, reactive measures (like a misconfigured EDR) can leave you exposed.
Security Leaders Settling for Annual Pentests
Testing once a year is no longer sufficient. A RAT that goes undetected for months can wreak havoc—stealing data, creating persistence, and opening backdoors. Continuous or more frequent testing is essential to maintain a real-time understanding of your defenses.
Organizations Stuck in Reactive Security Mode
Many teams only investigate potential risks after an incident has occurred. The RAT data underscores how quickly an attacker can move; by the time you react, they’ve already harvested credentials and possibly escalated privileges.
Failure to Adopt Offensive Exercises
Despite recognizing the value of emulating attacker tactics, many organizations remain hesitant. Yet the RAT data proves attackers are exploiting basic misconfigurations and inadequate EDR setups—showing the clear benefits of proactive, offense-driven strategies.
Taken together, these findings illustrate a widening chasm between perceived and actual security. While EDR tools are a critical piece of the puzzle, they are not a silver bullet. When reactive measures are combined with ineffective vulnerability scanning, delayed patching, and under-tested cloud environments, attackers can operate with minimal resistance.
How Hackers Are Bypassing EDR Solutions
As Endpoint Detection and Response (EDR) solutions evolve, so do the techniques hackers use to evade them. Instead of attempting to bypass detection through constant encryption updates—risking errors that could expose them—attackers are now focusing on disabling security defenses entirely.
A growing trend in EDR bypass strategies is the use of specialized EDR-killing tools, which allow ransomware groups and other cybercriminals to neutralize security software before executing their payloads. This section explores the key methods, tools, and trends in the EDR bypass landscape, including custom malware, driver exploits, and abuse of system-level access.

Key Methods Hackers Use to Bypass EDR
As endpoint detection and response (EDR) solutions become more advanced, hackers are constantly developing new methods to evade detection and disable security defenses. From Bring Your Own Vulnerable Driver (BYOVD) attacks to custom-built EDR killer malware, cybercriminals are leveraging increasingly sophisticated tactics to neutralize security tools before deploying ransomware or other malicious payloads. Ransomware operators tend not to update their encryptors frequently due to the risk of introducing flaws that could damage their reputation. As a result, security vendors often detect these encryptors effectively, prompting affiliates to turn to EDR killers as a last step to eliminate security defenses before execution.
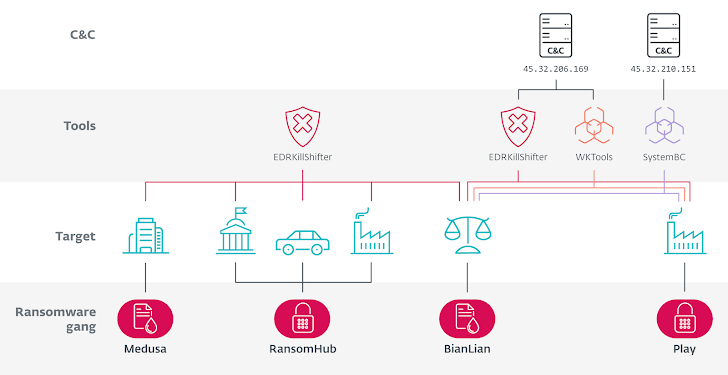
A striking example is RansomHub’s EDRKillShifter, a bespoke tool developed by the ransomware group and provided to its affiliates—a rare occurrence in the ransomware world. This tool, originally tied to RansomHub, has now been observed in attacks by Medusa, BianLian, and Play, underscoring a concerning trend of cross-group collaboration. This is particularly significant given that Play and BianLian operate within a closed Ransomware-as-a-Service (RaaS) model, where partnerships are built on long-term trust rather than open recruitment. The fact that these closed groups are adopting tools from rivals highlights an increasing level of strategic cooperation between ransomware gangs, making EDR bypass tactics more widespread and dangerous than ever.
1. Bring Your Own Vulnerable Driver (BYOVD)
Tactic: Attackers introduce a legitimate but vulnerable driver into a system and exploit its weaknesses to disable security solutions.
Why It Works: Security software often has kernel-level hooks, which can be turned off by exploiting driver vulnerabilities, rendering EDR blind.
Examples:
EDRKillShifter – Used by RansomHub affiliates and later repurposed by Medusa, BianLian, and Play ransomware groups.
ABYSSWORKER – A custom malicious driver used by Medusa ransomware to disable security defenses.
MS4Killer – Used by Embargo ransomware in 2024 to neutralize EDR solutions.
2. Direct System Manipulation & Process Injection
Tactic: Attackers manipulate system processes to evade detection, either by hijacking legitimate Windows processes or by injecting malicious code into trusted applications.
Why It Works: Many EDR solutions rely on behavioral detection—but when malware runs inside a legitimate process, detection becomes harder.
Techniques in Use:
Process Hollowing: Malware overwrites the memory of a legitimate process with malicious code.
DLL Sideloading: Attackers replace or modify DLL files used by trusted applications to execute malicious code.
API Hooking Evasion: Disrupting EDR’s ability to monitor API calls by tampering with Windows API functions.
Examples:
Cobalt Strike and Sliver Framework – Frequently used by ransomware actors for covert process injection and evasion.
SocGholish Malware – A JavaScript malware used to deliver persistent payloads while avoiding detection by masquerading as software updates.
3. Living Off the Land Binaries (LOLBins)
Tactic: Instead of introducing malicious binaries, attackers abuse built-in Windows tools to execute their payloads.
Why It Works: Since these are trusted system utilities, many EDR solutions do not flag them by default.
Common LOLBins Used for EDR Bypass:
PowerShell & WMI: Used for executing scripts and bypassing security policies.
MSBuild.exe: Exploited to execute malicious payloads in memory.
Rundll32.exe: Abused to execute DLLs in an obfuscated manner.
Examples:
QakBot Malware (QBot) – Uses PowerShell for script-based execution and defense evasion.
BlackCat/ALPHV Ransomware – Known for using LOLBins and legitimate admin tools to gain persistence and execute payloads.
4. User Mode Rootkits and Kernel Tampering
Tactic: Malware operates at the kernel level to disable security mechanisms and manipulate system calls.
Why It Works: Some advanced rootkits can hide processes, intercept API calls, and manipulate memory without being detected by user-mode security solutions.
Examples:
Terminator Malware – An advanced EDR killer used by multiple ransomware groups, capable of stopping 100+ security processes.
CosmicBeetle EDR Killer – Used in RansomHub and fake LockBit attacks to neutralize security defenses.
Notable Trends in EDR Bypass Tactics
Hackers are evolving their strategies to bypass endpoint detection and response (EDR) solutions, leveraging a mix of novel techniques, recycled exploits, and collaborative tool-sharing across ransomware groups. One of the most notable trends is the increasing use of Bring Your Own Vulnerable Driver (BYOVD) attacks, where attackers exploit legitimate but flawed drivers to disable security tools. Additionally, the rise of custom EDR-killing malware, such as RansomHub’s EDRKillShifter, shows that ransomware operators are investing in specialized tools to ensure their payloads execute undetected. Even more concerning is the growing cooperation among ransomware gangs, including those operating under closed RaaS models, who are repurposing each other’s tools to enhance their evasion capabilities. This convergence of tactics suggests that EDR bypass techniques are becoming more standardized and accessible, making it easier for both sophisticated and lesser-known actors to circumvent traditional endpoint defenses.
1. Cross-Gang Collaboration & Tool Sharing
Trusted affiliates from Play and BianLian are using RansomHub’s EDRKillShifter, highlighting a shift in inter-group collaboration.
Some ransomware operators are recycling or modifying existing tools, rather than developing new ones from scratch.
2. Increasing Use of Custom EDR Killers
More ransomware groups are deploying bespoke EDR-killing malware rather than relying on open-source options.
Medusa, Play, and BianLian have all adopted custom malicious drivers for defense evasion.
3. Rise of Fileless & Memory-Only Attacks
Malware is increasingly executed directly in memory, avoiding disk-based detection methods.
Red Team frameworks like Sliver and Brute Ratel are gaining traction as alternatives to Cobalt Strike for stealthier EDR evasion.
4. Focus on Privilege Escalation for EDRs Disruption
Attackers need admin privileges to disable EDR, so they prioritize:
Credential theft (e.g., Mimikatz, LSASS dumps)
Exploiting Windows vulnerabilities to gain SYSTEM access
Social engineering for user-assisted privilege escalation

How Organizations Can Defend Against EDR Bypass
-
Block Known Vulnerable Drivers
-
Maintain an updated blocklist of vulnerable drivers (e.g., Microsoft’s driver blocklist).
-
-
Restrict Administrative Privileges
-
Implement least privilege access to limit attackers’ ability to disable security tools.
-
-
Use Kernel API Virtualization (e.g., Warden)
-
Protect critical system functions from tampering by isolating them from attackers.
-
-
Enable Continuous Memory and Process Monitoring
-
Detect process injection, DLL abuse, and rootkit activity in real time.
-
-
Increase Red Team & Penetration Testing Efforts
-
Regularly simulate EDR bypass techniques to identify weaknesses before attackers do.
-
Hackers are no longer just evading detection—they are actively dismantling security defenses before launching ransomware attacks. The use of EDR-killing tools, process injection, fileless attacks, and LOLBins demonstrates that cybercriminals are adapting faster than many security teams.
The key to stopping these tactics lies in proactive defense: restricting privileges, detecting kernel-level attacks, and ensuring security tools cannot be easily disabled. By understanding and countering these evolving EDR bypass methods, organizations can stay ahead of the attackers and prevent devastating ransomware incidents.
Introducing Warden: A Layered Approach Beyond Traditional EDR
Despite the sobering data, there is a path forward. Warden takes endpoint security to a new level by combining auto-containment, 24×7 SOC support, and robust EDR monitoring to ensure threats like RATs are not just detected but actively thwarted before they can spread.
-
Auto-Containment
-
When suspicious behavior is detected, Warden automatically quarantines the host or process, preventing lateral movement and data exfiltration.
-
This proactive containment drastically reduces the mean time to respond (MTTR).
-
-
24×7 SOC
-
Warden’s SOC analysts are on standby around the clock, ensuring no alert goes unanswered.
-
Real humans monitor and validate potential threats, providing the context machines often miss.
-
-
EDR Monitoring & Beyond
-
Warden doesn’t rely on a single EDR engine. Instead, it integrates signals from multiple sources, applying correlation logic to detect even subtle anomalies.
-
By continuously assessing configurations and threat intelligence, Warden ensures EDRs are properly tuned and optimized.
-
These features address the core issues that surfaced in both the NodeZero RAT data and the Annual Insights Report. Rather than relying on a single product’s detection logic, Warden layers in active defense measures, automated containment, and human oversight to mitigate the gaps plaguing traditional security stacks.
The Emotional Reality: Is Your EDR Truly Protecting You?
It’s easy to trust a familiar brand name and assume your environment is safe. However, the data plainly shows that no single EDR—even the top performers—achieved 100% success in detecting and stopping a “noisy” RAT. And the Horizon3 AI Annual Insights Report 2025 drives home a broader point: reactive security approaches, outdated vulnerability scanning practices, and under-tested cloud environments create a perfect storm for attackers.
Ask yourself:
-
Are you comfortable with a 20% (or higher) chance of a successful breach?
-
Would your current EDR vendor’s support team be able to respond quickly enough if you discovered a RAT was already dumping credentials?
-
Do you have complete visibility into how your EDR is configured, and are you certain it’s optimized for your unique environment?
-
Have you moved beyond basic compliance checklists to truly offensive, continuous testing?
These questions are not meant to sow fear for the sake of it—they’re grounded in real-world pentest outcomes and validated by the Horizon3 AI Annual Insights Report 2025. But they do highlight the urgent need for continuous validation and a more holistic approach to endpoint security.
Next Steps: Evaluating Warden for Superior Coverage
If the NodeZero pentest data—and the broader insights from the Annual Report—have you reconsidering your reliance on a single EDR product, you’re not alone. Many security teams are now exploring Warden to fill these critical gaps. By combining auto-containment, 24×7 SOC monitoring, and robust EDR orchestration, Warden ensures you’re not left hoping your configuration is good enough—you’ll know your environment is secure because it’s continuously tested and monitored.
Ready to Learn More about Warden’s Endpoint Protection?
-
Schedule a demo: See how Warden or NodeZero can integrate with your existing security stack.
-
Join our user community: Share experiences, ask questions, and learn best practices from peers who’ve made the switch.
The threat landscape won’t wait for you to catch up. Attackers are already using straightforward techniques to bypass well-known EDRs. The only question is whether your organization will remain exposed—or take proactive steps to close these gaps with a solution designed to auto-contain threats, provide 24×7 SOC oversight, and continuously validate that your endpoints remain secure.
Don’t let a single misconfiguration or suboptimal policy put your entire enterprise at risk. Reach out now to find out how Warden can transform your security posture from uncertain to truly protected.

Top 11 Endpoint Detection and Response (EDRs) Questions and Answers Based on the Article
What is the primary method hackers use to bypass EDR solutions?
Hackers frequently use the Bring Your Own Vulnerable Driver (BYOVD) technique, which involves exploiting legitimate but flawed drivers to disable security tools and avoid detection.What is EDRKillShifter, and why is it significant?
EDRKillShifter is a custom EDR-killing tool developed by RansomHub, designed to disable endpoint security solutions before deploying ransomware. It has since been adopted by other ransomware groups like Medusa, BianLian, and Play, highlighting a trend of tool-sharing among cybercriminals.Why do ransomware operators avoid making major updates to their encryptors?
Updating encryptors risks introducing flaws that could weaken their effectiveness or expose them to detection. Instead of modifying encryptors frequently, ransomware affiliates use EDR-killing tools to remove security solutions just before executing their payloads.How are ransomware groups collaborating despite operating under closed RaaS models?
Groups like Play and BianLian, which typically restrict partnerships to trusted affiliates, have been observed sharing tools with RansomHub and other rivals, suggesting an increasing level of cooperation among cybercriminals.Who is suspected to be behind the recent ransomware attacks using EDRKillShifter?
A threat actor dubbed QuadSwitcher is believed to be responsible for attacks involving Play, Medusa, BianLian, and RansomHub, indicating a possible overlap between different ransomware operations.What other recent EDR-killing tools have been observed in use?
Apart from EDRKillShifter, hackers have deployed tools like MS4Killer (used by the Embargo ransomware gang) and ABYSSWORKER (linked to Medusa ransomware) to neutralize security defenses.What is the impact of these EDR bypass techniques on cybersecurity?
The increasing use of EDR-killers and tool-sharing between groups makes ransomware attacks more effective and harder to detect, forcing security teams to adapt their defenses against these evolving threats.Why do hackers need admin privileges to deploy an EDR killer?
Most EDR-killing tools require high-level privileges to disable security software, meaning attackers must first escalate their privileges—often through credential theft or exploiting system vulnerabilities—before deploying these tools.What role do custom malicious drivers play in EDR bypass strategies?
Some ransomware groups, like Medusa, have been observed using custom drivers (e.g., ABYSSWORKER) to disable security tools, further demonstrating the trend of tailored malware for evasion.How can organizations defend against these EDR bypass techniques?
Companies should enable detection of potentially unsafe applications, monitor for privilege escalation attempts, and ensure they are not using outdated or vulnerable drivers that could be exploited in BYOVD attacks.What does the growing trend of EDR bypass tactics suggest about the future of ransomware?
The increasing sophistication of EDR-killers, BYOVD techniques, and cross-group collaboration indicates that ransomware operations are becoming more organized, efficient, and capable of evading traditional security defenses, making proactive threat detection more critical than ever.





