Master the Art of Cyber Defense with MITRE ATT&CK: Your Blueprint for Unmatched Security
Explore the comprehensive framework that empowers your organization to stay ahead of advanced cyber threats.
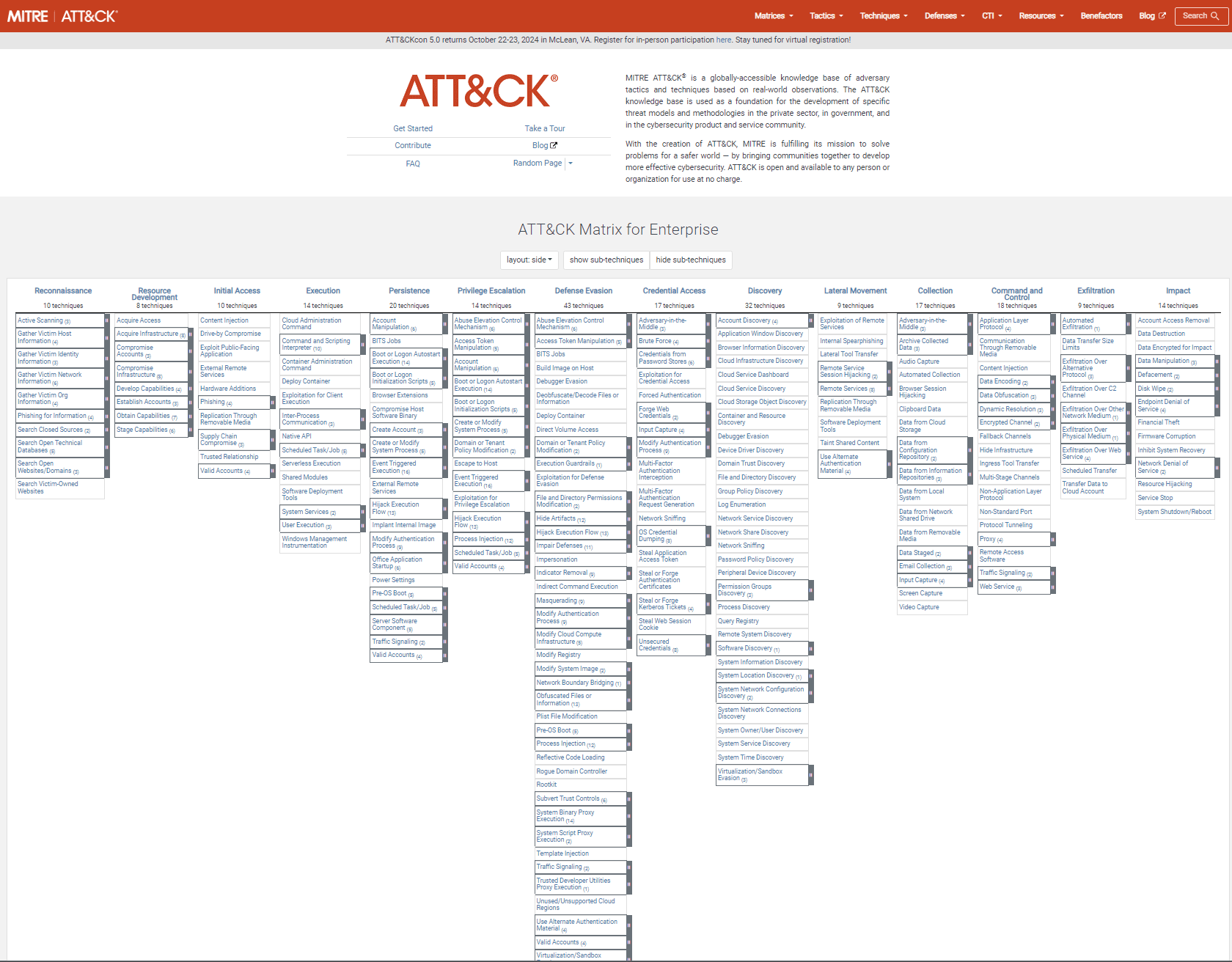
Understanding the MITRE ATT&CK Framework
What is MITRE ATT&CK?
The MITRE ATT&CK framework is a globally recognized knowledge base of adversary tactics and techniques based on real-world observations. It’s designed to help organizations understand how adversaries operate, providing a foundation for enhancing your cybersecurity strategy.
Why Your Organization Needs MITRE ATT&CK?
In today’s complex threat landscape, understanding adversary behavior is crucial. The MITRE ATT&CK framework offers a structured approach to identifying, analyzing, and mitigating cyber threats, enabling your organization to strengthen its defense mechanisms and proactively address vulnerabilities.
- Identify and prioritize risks
- Enhance incident response strategies
- Improve threat detection and prevention
- Align your security operations with industry best practices
Breaking Down the MITRE ATT&CK Framework
-
Tactics:
The “why” of an adversary’s actions. Understand the strategic goals behind cyberattacks, from initial access to impact. -
Techniques:
The “how” of an attack. Learn about the specific methods attackers use to achieve their goals, such as phishing, lateral movement, and data exfiltration. -
Procedures:
Real-world examples of how tactics and techniques are executed, offering insights into how threats evolve and adapt.
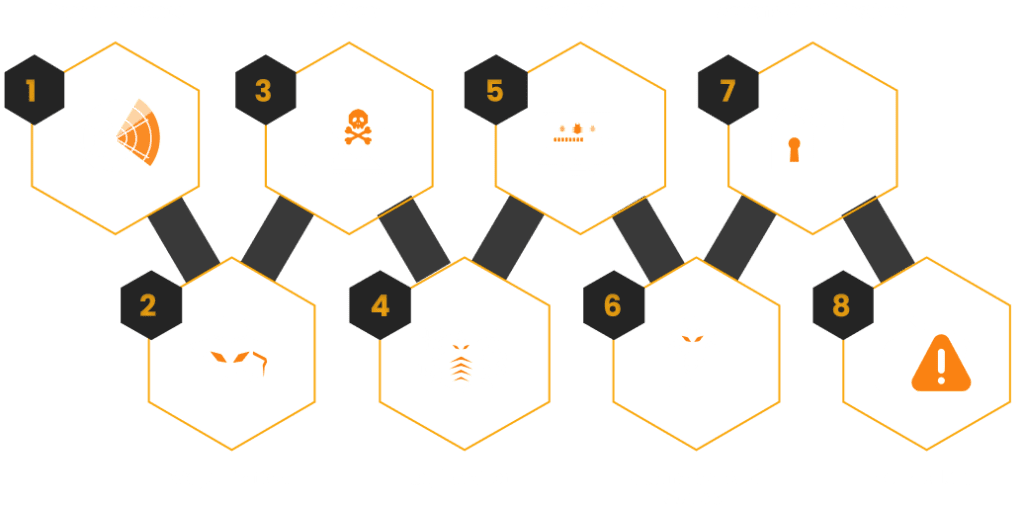
The Cyber Intrusion Kill Chain, also known simply as the Kill Chain, is a concept adapted from military operations and first applied to cybersecurity by engineers at Lockheed Martin. It provides a structured approach to understanding the various stages of a cyberattack, from initial reconnaissance to the final impact on the target. The Kill Chain is invaluable not just for conducting an attack but also for detecting and defending against one. When applied defensively, the goal is to break the chain, thereby thwarting the attacker’s efforts.
The Kill Chain: An Overview
The Kill Chain framework describes a series of steps that an attacker must go through to execute a successful cyberattack. The stages include:
- Reconnaissance: The attacker identifies potential targets and assesses them for vulnerabilities.
- Weaponization: Development or acquisition of malicious payloads, such as malware, to exploit identified vulnerabilities.
- Delivery: Transmission of the payload to the target, often via phishing emails, compromised websites, or physical devices like USB drives.
- Exploitation: Triggering the malicious code, which could occur through user interaction (e.g., opening a file) or automated processes.
- Installation: Establishing a persistent presence in the target environment, often through backdoors or other methods.
- Command & Control (C&C): The attacker creates a communication channel with the compromised system to further their objectives.
- Actions on Objectives: The final stage where the attacker achieves their goal, such as data exfiltration, disruption of services, or further spreading of the attack.
This framework helps organizations understand where their defenses may be weak and where they can focus their efforts to disrupt an attack before it succeeds.
The Evolution to MITRE ATT&CK
While the Kill Chain provides a high-level view of an attack, the MITRE ATT&CK framework dives deeper into the tactics, techniques, and procedures (TTPs) used by attackers. MITRE ATT&CK categorizes these TTPs into specific behaviors, offering a more granular view of how attacks unfold in real-world scenarios.
- Tactics: These represent the overarching goals of an attacker, such as gaining initial access, moving laterally, or exfiltrating data.
- Techniques: These describe how an attacker achieves their tactical goals. For example, “Phishing” is a technique used to gain initial access.
By mapping the stages of the Kill Chain to specific tactics and techniques in MITRE ATT&CK, organizations can better understand how to defend against attacks and where to deploy their resources.
Optimizing for the MITRE ATT&CK Framework
To optimize your cybersecurity posture, it’s essential to integrate the Kill Chain with the MITRE ATT&CK framework. This combined approach allows for a more detailed and actionable defense strategy.
Reconnaissance and Weaponization: In the MITRE ATT&CK framework, these stages correspond to pre-attack behaviors, such as gathering information about the target. Organizations should focus on intelligence gathering and threat detection to identify potential threats before they escalate.
Delivery and Exploitation: Here, the MITRE ATT&CK framework identifies tactics like “Initial Access” and “Execution.” Defenses should include advanced email filtering, web security, and user training to prevent attackers from delivering and executing their payloads.
Installation, Command & Control, and Actions on Objectives: MITRE ATT&CK covers persistence, lateral movement, and exfiltration tactics. Defensive measures should include endpoint detection and response (EDR), network segmentation, and data loss prevention (DLP) tools.
Advanced Defensive Strategies with Warden
Warden, offers sophisticated defense mechanisms designed to counteract even the most persistent and advanced threats. By aligning its technology with the MITRE ATT&CK framework, Warden excels in neutralizing threats, especially in the later stages of the Cyber Kill Chain, where traditional defenses often struggle.
Network Communication Control
Warden’s Default Deny technology is a cornerstone in preventing attackers from establishing Command & Control (C2) channels. When an unknown file is contained within Warden’s environment, it is effectively isolated, with no ability to create network sockets or initiate any form of communication. This approach bypasses the complexities of protocol decoding and identification of non-standard port usage, which are often exploited by attackers. Instead, Warden’s method is straightforward: all communication is blocked until a definitive verdict is returned by the Verdict Cloud system. If the file is determined to be safe, only then is network communication permitted. This unique approach ensures that any attempts to establish a C2 channel are entirely thwarted, regardless of the sophistication of the attack or evasion techniques employed.
Kernel API Virtualization
Warden’s Kernel API Virtualization technology introduces an additional layer of security by creating a virtual interface between potentially harmful code and the operating system. This layer effectively prevents unauthorized access to critical system resources, such as the file system, registry, and other kernel-level operations. During the “Actions on Objectives” phase, this technology is particularly crucial. It not only blocks the attack but also ensures that the malicious code cannot persist or affect the underlying system operations.
For example, in the case of Privilege Escalation:
- Boot or Logon AutoStart Execution: Adversaries may attempt to configure system settings to automatically execute malicious programs during system boot or logon. However, Warden’s Kernel API Virtualization prevents any modifications to system-critical areas, such as the Windows Registry, ensuring that these attempts do not persist and do not affect the operational system.
In the realm of Process Injection:
- Attackers often inject code into processes to evade detection or elevate privileges. While traditional defenses may rely on behavior detection, Warden’s virtualization approach stops these actions by blocking any execution of unauthorized code, ensuring that malicious processes cannot compromise system integrity.
Lateral Movement and Exploitation of Remote Services:
- Warden’s containment strategy effectively isolates unknown files, allowing them only to interact with virtualized environments. This isolation extends to network services and remote systems, preventing attackers from exploiting vulnerabilities and moving laterally within the network. By containing the threat within a controlled environment, Warden eliminates the possibility of escalation and unauthorized access.
Attack Collection and Exfiltration:
- Warden’s Kernel API Virtualization also prevents unauthorized access to sensitive resources, such as screen capture and clipboard data, within its containment environment. Furthermore, it blocks any attempt to create network connections for exfiltration, ensuring that sensitive information remains secure.
Impact Mitigation:
- Finally, in the critical phase of Impact, where attackers aim to manipulate or destroy data, Warden’s virtualization of the file system and service access ensures that such attempts are neutralized. By preventing unauthorized interactions with the system, Warden safeguards against data destruction, denial of service, and system shutdowns, maintaining the integrity and availability of critical assets.
Warden’s advanced defensive strategies, particularly its Default Deny technology and Kernel API Virtualization, provide a robust defense against sophisticated threats, ensuring comprehensive protection throughout the Cyber Kill Chain.
Conclusion
By integrating the Kill Chain with the MITRE ATT&CK framework and leveraging advanced tools like Warden, organizations can create a robust defense strategy that not only identifies and disrupts attacks but also prevents them from progressing through the later stages of the Kill Chain. This holistic approach is essential for defending against today’s sophisticated cyber threats and ensuring the security of your digital environment.
DOWNLOAD THE FREE
BUYERS GUIDE FOR KERNEL-LEVEL DEFENSE 2025

Business Complete - Supporting Businesses with Extended Detection and Response Capabilities
Get all the features of Managed Professional along with Network and Cloud Security along with added deployment support.