The Evolution of Cybersecurity Gartner Analysis of Security Operations Centers (SOCs) in 2024: New Trends, Challenges, and Innovations
Gartner Analysis of Security Operations Centers (SOCs) in 2024, continue to evolve, adapting to rapid technological advancements and shifting work environments, particularly with the rise of hybrid and remote work. According to Gartner’s Hype Cycle for Security Operations 2024, SOCs face an increasingly complex threat landscape, amplified by the growing use of generative AI (GenAI) and the need for continuous threat exposure management (CTEM). Security and risk management (SRM) leaders must develop more agile and risk-centered security strategies to protect their digital assets effectively.
Gartner Key Changes in SOCs
Generative AI in Cybersecurity
GenAI is revolutionizing SOCs by enhancing threat detection and automating responses. However, it also opens new vulnerabilities, requiring SOCs to both leverage and defend against AI-driven threats. AI assistants are becoming integral to extended detection and response (XDR) platforms, reducing data management costs and increasing operational efficiency.Shift to Continuous Threat Exposure Management (CTEM)
The CTEM framework has emerged as a leading strategy, focusing on scoping, discovery, prioritization, validation, and mobilization of security exposures. SOCs are moving from periodic vulnerability assessments to continuous threat exposure management, ensuring vulnerabilities are addressed in real time.Identity Threat Detection and Response (ITDR) Identity protection has taken center stage in SOC operations, with ITDR being integrated into detection frameworks to fortify digital identities. This trend is further driving the adoption of co-managed monitoring services, allowing organizations to better customize and manage their threat detection efforts.
Major Challenges Facing SOCs
Data Overload and Operational Efficiency
As organizations gather more data across various technology and business domains, SOCs are struggling to scale their operations due to staffing and budget constraints. SOCs must find ways to manage increasing data volumes, often by using AI to enhance visibility without overwhelming analysts.Vendor and Technology Confusion
With the growing market of security tools and services, many organizations face difficulties evaluating and integrating new technologies, such as cybersecurity mesh architecture (CSMA) or exposure assessment platforms. SRM leaders must navigate marketing hype and align solutions with their organization’s unique attack surface and risk profile.Complexity in Security Control Optimization
Security controls continue to grow more complex as organizations adopt diverse infrastructures. Tools like automated security control assessments (ASCA) are emerging to optimize configurations, but without proper governance and triage, SOCs risk facing a backlog of unresolved issues.
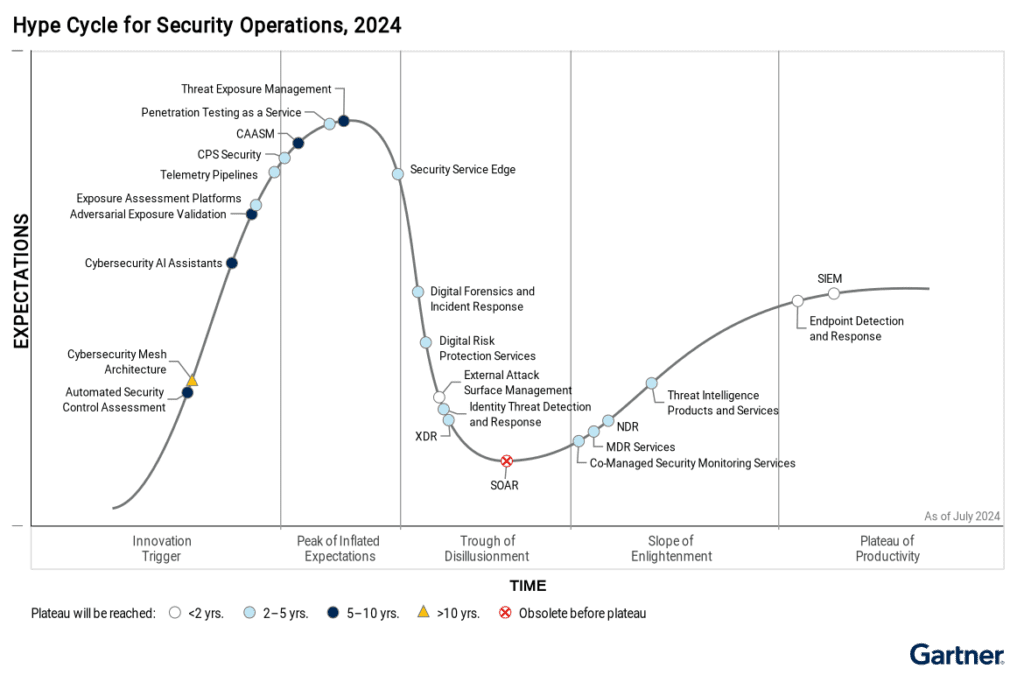
What’s New and Exciting in the Gartner Analysis of Security Operations Centers in 2024?
Extended Detection and Response (XDR)
XDR solutions have grown to incorporate prebuilt automation and analytics, making it easier for organizations to gain threat intelligence with minimal manual input. With AI assistants integrated into XDR tools, even smaller organizations can adopt advanced threat detection without the need for large in-house teams.Co-Managed Monitoring Services
As organizations demand more customizable solutions, co-managed SOC services allow clients to participate more actively in managing their security operations. This flexibility lets businesses tailor monitoring services to meet specific security and operational needs.Adversarial Exposure Validation
SOCs are increasingly turning to offensive security techniques like breach attack simulations and autonomous penetration testing to test their defenses. These tools simulate real-world attacks, giving organizations insight into exploitable vulnerabilities and the efficacy of their controls.- Cybersecurity AI Assistants Cybersecurity AI assistants leverage large language models to help discover existing knowledge from cybersecurity tools and generate content for security teams. They promise improved productivity and efficiency, particularly for tasks like incident response, risk management, and code review. While adoption is still low, these assistants are expected to evolve into more autonomous agents capable of working with high-level guidance.
- Adversarial Exposure Validation This process uses automated tools to simulate real-world attacks, demonstrating the feasibility and exploitability of various security exposures. It combines multiple simulation techniques to provide consistent, continuous, and automated evidence of potential vulnerabilities. This approach helps security teams prioritize strategic initiatives, evaluate technology investments, and expand red team capabilities to support broader exposure management efforts.
- Exposure Assessment Platforms (EAPs) EAPs continuously identify and prioritize exposures across a range of asset classes, supporting continuous threat exposure management (CTEM) programs. They consolidate results from various assessment tools, providing a centralized view of high-risk exposures. EAPs help organizations prioritize remediation efforts based on factors like exposure severity, asset criticality, and business impact, improving operational efficiency in managing security risks.
- Telemetry Pipelines Telemetry pipelines provide a uniform mechanism to manage the collection, ingestion, enrichment, transformation, and routing of machine data from source to destination. They help organizations handle the increasing volume of telemetry generated by modern workloads, optimize costs associated with data movement and storage, and consolidate operational and security-related telemetry collection. These solutions improve efficiency in managing and analyzing health, performance, and security data across distributed environments.
- Cyber-Physical Systems (CPS) Security CPS security focuses on ensuring the safety, reliability, and resilience of systems that interact with the physical world, such as industrial control systems, IoT devices, and critical infrastructure. As these systems become increasingly targeted by attackers, CPS security efforts must consider not only traditional cybersecurity practices but also physical safety and operational resilience. The field is evolving to include specialized security solutions and is subject to growing regulatory attention due to its importance in critical infrastructure protection.
- CAASM (Cyber Asset Attack Surface Management) helps organizations address visibility challenges by aggregating data from existing security tools to provide a comprehensive view of all internal and external assets. Through API integrations, CAASM identifies coverage gaps, misconfigurations, and security control deficiencies. It enhances security hygiene by automating data collection and reconciliation, replacing manual processes. While it reduces operational overhead and improves asset management, its adoption is limited due to resistance against adding more tools, scalability issues, and integration challenges with existing systems.
- Penetration Testing as a Service (PTaaS) delivers penetration testing through a SaaS platform, blending automation with human testers to enhance efficiency. It provides continuous testing with real-time communications and visibility of results, allowing organizations to address vulnerabilities faster and integrate testing into DevSecOps pipelines. PTaaS is well-suited for application and external infrastructure testing but may not replace traditional in-depth pentests for complex environments. Its adoption is growing as businesses seek cost-effective, continuous security validation to meet compliance and improve risk management.
- Threat Exposure Management focuses on assessing and managing the accessibility and exploitability of digital assets. Governed by a Continuous Threat Exposure Management (CTEM) program, it prioritizes risk reduction by providing a holistic view of vulnerabilities across the organization’s attack surface. This approach integrates penetration testing, threat intelligence, and vulnerability scanning, helping security teams address conflicting priorities and reduce risks across complex digital landscapes.
- Security Service Edge (SSE) secures access to web, SaaS applications, and private applications through adaptive access control, data security, and compliance. Delivered primarily as a cloud-based service, SSE integrates secure web gateways (SWGs), cloud access security brokers (CASBs), and zero-trust network access (ZTNA). SSE enables organizations to protect hybrid work environments, enforce security policies, and simplify operations by converging security functions. It supports the transition to Secure Access Service Edge (SASE) when paired with software-defined WAN (SD-WAN). However, the market faces obstacles such as vendor disparities in feature offerings, including limited DLP and on-premises support, and concerns about availability and performance in some regions.
- Digital Forensics and Incident Response (DFIR) services help organizations manage security incidents by providing forensic analysis, breach investigation, and proactive breach avoidance strategies. These services are crucial for handling complex cyberattacks, such as ransomware, where specialized skills are required. DFIR assists organizations in minimizing breach impacts, reducing downtime, and ensuring compliance with regulatory requirements. The growing need for rapid response and detailed incident investigation has led to increased adoption of DFIR services globally. However, organizations must navigate vendor differences in service delivery and understand the internal coordination required for effective incident response.
- Digital Risk Protection Services (DRPS) enable organizations to identify and mitigate external-facing risks such as brand impersonation, social media threats, and dark web activities. DRPS provides comprehensive visibility into threats across the clear, deep, and dark web, assessing threat actors and offering technical responses such as threat takedowns. This service has gained popularity due to the commoditization of attack techniques and is crucial for maintaining an organization’s reputation and business continuity. However, the crowded market, with over 75 vendors, poses challenges in differentiation and comprehensive coverage. Organizations should evaluate vendors based on takedown success rates, managed service options, and their alignment with specific use cases.
- External Attack Surface Management (EASM) involves identifying internet-facing assets, such as exposed servers and cloud misconfigurations, that can be exploited by threat actors. EASM is increasingly important as digital transformation, cloud adoption, and hybrid working environments expand an organization’s attack surface. By offering capabilities like asset discovery and risk prioritization, EASM helps security leaders mitigate vulnerabilities and respond to incidents. Despite its value, the market faces challenges such as overburdened vulnerability management teams and consolidation among vendors. Organizations should consider EASM as part of a broader attack surface management strategy, particularly when external-facing services drive revenue.
- Identity Threat Detection and Response (ITDR) is a critical security discipline that protects the identity and access management (IAM) infrastructure from targeted attacks. As identity becomes a key focus for security operations, ITDR adds layers of protection against credential misuse, administrative account compromises, and forged tokens. ITDR tools monitor identity-specific threats, ensuring rapid detection and remediation. However, the effectiveness of ITDR requires collaboration between IAM and security teams, which can be challenging. Organizations must prioritize protecting their IAM infrastructure with ITDR tools that detect identity threats, mitigate configuration changes, and respond quickly to attacks, ensuring seamless security across the identity ecosystem.
Evaluating the Gartner Analysis of Security Operations Centers (SOCs) in 2024 highlights critical innovations SOC leaders should consider:
- Security Service Edge (SSE) and Cybersecurity Mesh Architecture (CSMA) are two transformational technologies expected to redefine the SOC landscape in the coming years, enabling seamless and scalable security across hybrid environments.
- Technologies like endpoint detection and response (EDR), managed detection and response (MDR), and threat intelligence services have matured and proven their value. These tools are essential for modernizing SOC capabilities and improving incident response times.

Top 11 Questions About SOCs in 2024
1. What is CTEM, and how can it improve my organization’s security posture?
Key Point: Continuous Threat Exposure Management (CTEM) involves regularly assessing and testing an organization’s defenses against evolving threats. It identifies vulnerabilities before attackers exploit them.
How Warden is taking this head-on: Warden’s Default Deny Architecture inherently minimizes threat exposure by blocking unauthorized activity. Combined with regular updates and Kernel API Virtualization, Warden ensures that the most critical attack vectors are neutralized, improving overall security posture by reducing potential exposure paths. However, we have also integrated an advanced continuous AI pentesting capability, that if purchased would allow you to validate all patches and security tools are working as intended as often as you would like. This is far different than scheduling and waiting the results of a human driven pentest.
2. How can AI assistants enhance SOC operations without introducing new risks?
Key Point: AI assistants can streamline threat detection, response times, and automate low-level tasks in SOCs. However, they risk generating false positives and missing sophisticated attacks.
How Warden is taking this head-on: Warden doesn’t rely on AI for threat detection, which can introduce new risks. Instead, it employs a proactive, zero-trust model that blocks unauthorized processes automatically, significantly reducing the reliance on potentially flawed AI models and enhancing SOC efficiency. That are needed to overcome security systems flagging everything for the analysts to review.
3. What role does generative AI play in both defending and attacking cybersecurity?
Key Point: Generative AI can be used for both cyber defense (automating detection and response) and attacks (creating sophisticated malware). Its dual role means security solutions must adapt quickly to both defend and prevent AI-driven threats.
How Warden is taking this head-on: Warden’s Zero Trust Endpoint Defense creates a robust shield against AI-driven attacks by restricting any non-verified code execution, preventing malware generated by AI from compromising systems, while also providing protection that does not rely on reactive AI defenses, which may be outpaced by attackers.
4. Why is identity threat detection and response (ITDR) critical for SOCs?
Key Point: Identity Threat Detection and Response (ITDR) helps SOCs protect user credentials from being compromised, which is crucial as attackers increasingly target identity systems to bypass traditional defenses.
How Warden is taking this head-on: Warden’s Kernel API Virtualization ensures that even if credentials are compromised, malicious actors are restricted from executing unauthorized actions or moving laterally through the network, thus safeguarding the system against identity-based threats.
5. How do co-managed monitoring services differ from traditional SOC solutions?
Key Point: Co-managed SOCs blend in-house security teams with external expertise, offering greater flexibility and 24/7 monitoring, compared to traditional SOCs, which are fully managed internally.
How Warden is taking this head-on: Warden’s endpoint protection is designed to seamlessly integrate with co-managed monitoring services, providing enhanced visibility and actionable insights for both internal and external security teams, ensuring more effective collaboration and threat management.
6. What is the value of adversarial exposure validation, and how does it work?
Key Point: Adversarial exposure validation tests an organization’s defenses by simulating real-world attacks to identify weaknesses before an attacker exploits them.
How Warden is taking this head-on: Warden’s Zero Trust model significantly reduces exposure, even during adversarial testing. Its Default Deny policy ensures that any unauthorized behavior is auto-contained before impact, whether through testing or real attack attempts, is blocked at the endpoint, providing inherent defense without needing constant validation. We leverage an advanced continuous model for validation of adversarial risks, that those interested in can opt into this service for additional costs.
7. What are the key differences between XDR and SIEM, and when should I adopt XDR?
Key Point: Extended Detection and Response (XDR) integrates data across endpoints, networks, and cloud environments to provide broader threat detection than Security Information and Event Management (SIEM), which focuses more on log aggregation and monitoring.
How Warden is taking this head-on: Warden’s Zero Trust Endpoint Defense complements XDR by adding an extra layer of security at the endpoint level, ensuring that threats blocked by Warden do not even reach the detection or response phase, making XDR adoption smoother, less time consuming and more efficient. Warden also has a fully integrated SIEM, so you can bring your logs from all your other security sensors into a single place for analysis by those choosing the managed service will get this included.
8. How can smaller organizations benefit from preconfigured SOC technologies?
Key Point: Preconfigured SOC technologies provide cost-effective, ready-to-deploy security solutions for smaller organizations that may lack the resources for a fully customized SOC.
How Warden is taking this head-on: Warden’s modular design allows smaller organizations to implement enterprise-grade protection without the complexity of managing large-scale SOC operations. This enables these organizations to secure their environments quickly and affordably without sacrificing protection.
9. How should organizations prioritize technology investments to maximize security ROI?
Key Point: Organizations should prioritize investments that provide long-term protection and proactive defenses, rather than reactive measures that only address known threats.
How Warden is taking this head-on: By focusing on proactive threat prevention with its Zero Trust Endpoint Defense, Warden provides high ROI by reducing the number of incidents and eliminating the need for extensive incident response efforts. This allows organizations to invest smartly in solutions that prevent attacks before they happen, maximizing security ROI.
10. What is the cybersecurity mesh architecture (CSMA), and when should it be implemented?
Key Point: Cybersecurity Mesh Architecture (CSMA) is a flexible, integrated security approach that secures assets regardless of their location. It’s ideal for organizations with distributed environments or a hybrid workforce.
How Warden is taking this head-on: Warden’s Zero Trust model naturally aligns with CSMA by securing distributed endpoints with its Kernel API Virtualization and Default Deny Technology, ensuring all systems remain secure, no matter where they are located, or how they are accessed.
11. What is the role of continuous exposure assessment platforms, and how do they fit into the broader security strategy?
Key Point: Continuous Exposure Assessment Platforms provide real-time visibility into an organization’s vulnerabilities and the potential impact of new threats, helping to maintain a strong security posture over time. This is a new category in the Gartner Analysis of Security Operations Centers (SOCs) in 2024.
How Warden is taking this head-on: Warden’s Default Deny architecture reduces the need for continuous exposure assessments by inherently protecting against new and emerging threats. Warden’s proactive blocking of unauthorized actions ensures that exposure is minimized at all times, fitting seamlessly into broader security strategies without the need for constant assessment.







