2024 Cyber-Physical Systems (CPS) Security: A Comprehensive Analysis and Future Outlook
In our technologically advanced era, Cyber-Physical Systems (CPS)—engineered to bridge digital operations with the physical world—are integral to modern infrastructure. These systems, encompassing everything from IoT devices to industrial control systems, manage complex physical processes and interactions in real-time. With increased connectivity, CPS security has become critical; vulnerabilities can lead to disruptions that extend into the physical world, affecting human safety and economic stability. This analysis provides an in-depth view of the CPS security landscape, guided by Gartner’s 2024 Hype Cycle and enhanced by insights into supply chain security, dark web intelligence, AI-driven threat detection, and regulatory challenges.
Types of Systems Covered by Cyber Physical Systems (CPS)
Cyber-Physical Systems (CPS) encompass a wide variety of interconnected physical and digital systems that interact with and control physical environments through sensors, actuators, and intelligent computing. These systems are critical to sectors where real-time control and response are essential, as they integrate computational and physical processes to achieve seamless and autonomous operation. Below are some of the key types of CPS, highlighting the diverse applications and their importance across industries.
1. Industrial Control Systems (ICS)
- Description: Industrial Control Systems, including SCADA (Supervisory Control and Data Acquisition) and DCS (Distributed Control Systems), form the backbone of automation in industries such as manufacturing, power generation, oil and gas, and water treatment. ICS facilitates precise control over processes and equipment in environments like factories, refineries, and processing plants. The systems gather data from sensors and actuators, providing real-time monitoring and enabling operators to make critical adjustments remotely.
- CPS Role: ICS enhances production efficiency, operational safety, and environmental compliance through rigorous control of industrial processes. By allowing centralized or decentralized automation, these systems reduce manual intervention and increase reliability. However, any disruption to ICS can halt production, degrade safety, or cause environmental hazards, making them high-priority for CPS security.
2. Autonomous Vehicles and Transportation Systems
- Description: This category includes land, air, and sea vehicles, such as autonomous cars, drones, trains, and ships, equipped with sensors, artificial intelligence (AI), and GPS technology. These systems can operate semi- or fully autonomously, relying on real-time data for navigation, collision avoidance, and environmental awareness. In smart transportation networks, traffic signals, route optimization, and predictive maintenance enhance the safety and efficiency of transportation infrastructure.
- CPS Role: CPS in autonomous transportation systems ensure operational safety, efficiency, and continuity. They minimize human error, reduce traffic congestion, and optimize logistics. However, cyber threats to these systems could lead to malfunctions, traffic disruptions, or accidents, endangering human lives and public infrastructure.
3. Smart Grids and Energy Management Systems
- Description: Smart grids integrate digital communication with the traditional electricity distribution network, enabling utilities to monitor, control, and optimize the generation, distribution, and consumption of electricity. Real-time data analytics allow for dynamic load balancing and demand response, enhancing resilience and sustainability in energy management.
- CPS Role: CPS in smart grids enable utilities to efficiently manage power supply, respond to fluctuations, and mitigate outages by distributing electricity where needed. By improving reliability and energy efficiency, CPS contribute to grid resilience and environmental sustainability. However, security breaches could lead to power disruptions, affecting public services, business operations, and overall societal stability.
4. Medical Devices and Healthcare Systems
- Description: Medical CPS encompass wearable health monitors, smart diagnostic tools, robotic surgical systems, and automated drug delivery mechanisms. These devices play an essential role in patient monitoring, diagnostics, and even critical surgeries, where precision and real-time responsiveness are vital. They are increasingly connected, sharing data across healthcare networks to support timely, accurate medical interventions.
- CPS Role: CPS in healthcare enable real-time, precise control of medical devices, enhancing patient care, diagnostic accuracy, and treatment outcomes. They ensure that patients receive timely interventions while minimizing human error. However, compromised medical CPS can lead to data breaches, device malfunctions, or life-threatening outcomes, making security paramount.
5. Building Automation and Smart Home Systems
- Description: These systems include automated control of lighting, HVAC (heating, ventilation, and air conditioning), security, fire safety, and even energy management in both residential and commercial buildings. They provide convenience, energy efficiency, and enhanced security through interconnected devices and sensors, allowing users to control systems remotely or set automated routines.
- CPS Role: Building automation CPS maintain comfort, safety, and energy efficiency by responding to environmental changes and user preferences in real time. They enhance living and working environments, but security vulnerabilities can compromise user privacy, safety, and property security, especially with increased integration of IoT devices.
6. Robotics and Autonomous Manufacturing Systems
- Description: Robotics and autonomous systems are critical in modern manufacturing, incorporating automated guided vehicles (AGVs), robotic arms, and precision machines. These systems are typically controlled through AI algorithms and sensor feedback, allowing high precision in tasks such as assembly, inspection, and packaging.
- CPS Role: In manufacturing, CPS contribute to high accuracy, efficiency, and adaptability, making production processes more flexible and cost-effective. By minimizing human labor in repetitive and hazardous tasks, CPS increase safety and productivity. However, any attacks or malfunctions can disrupt production lines, damage equipment, and endanger operators, making security crucial in industrial settings.
7. Agriculture and Environmental Monitoring Systems
- Description: Agriculture CPS include autonomous tractors, smart irrigation systems, drones for crop and field monitoring, and environmental sensors that track soil, weather, and crop conditions. Environmental monitoring systems also cover air quality monitoring, pollution tracking, and natural disaster detection. These systems use data analytics to enhance sustainable agriculture and resource management.
- CPS Role: CPS in agriculture improve efficiency, yield, and resource management by automating and optimizing tasks like irrigation, fertilization, and pest control. In environmental monitoring, they enable proactive responses to environmental changes. Security breaches could disrupt critical agricultural operations, cause resource wastage, or delay disaster response, impacting food security and environmental conservation.
8. Public Safety and Emergency Response Systems
- Description: Public safety CPS includes surveillance cameras, automated emergency response systems, communication networks for law enforcement, and firefighting services. These systems are instrumental in real-time monitoring, event detection, and coordinating responses to crises such as natural disasters, accidents, or security threats.
- CPS Role: In emergency response, CPS ensure rapid and coordinated action during critical situations, enhancing public safety and minimizing harm. They provide real-time situational awareness and support decision-making. However, vulnerabilities could impair response effectiveness, risking lives and property during emergencies.
9. Water Management and Treatment Systems
- Description: CPS in water management monitor and control water distribution networks, quality testing, and waste treatment facilities. These systems ensure that potable water is safe for consumption and that wastewater is processed to environmental standards, serving public health and sanitation needs.
- CPS Role: Water management CPS enable efficient, safe distribution of clean water and treatment of wastewater. By maintaining infrastructure integrity, these systems ensure consistent water quality and availability. Security threats to these systems could lead to contamination, supply interruptions, or environmental hazards, underscoring the need for robust cybersecurity.
10. Aerospace and Defense Systems
- Description: CPS in aerospace and defense include UAVs (unmanned aerial vehicles), missile guidance systems, automated surveillance, and response systems, and other military-grade assets. These systems often operate in hostile environments, requiring secure, reliable performance to support national security objectives.
- CPS Role: In defense, CPS play a critical role by providing real-time data, precision targeting, and secure communication to meet mission objectives. They ensure that defense assets function effectively in combat scenarios. Breaches or disruptions could compromise national security, making cybersecurity a top priority for these mission-critical systems.
11. Internet of Things (IoT)
- Description: IoT systems consist of a vast network of interconnected devices that collect and share data across various environments. They include smart home devices, wearable health monitors, industrial sensors, and environmental monitors, providing automation and connectivity to diverse applications. IoT is implemented in numerous sectors like healthcare, smart cities, logistics, and agriculture, making it a versatile component of modern CPS.
- CPS Role: IoT devices in CPS play a critical role in real-time monitoring, data collection, and automated decision-making, supporting predictive maintenance, energy management, and safety. By creating highly interconnected environments, IoT enables faster and more efficient responses across physical and digital domains. Security vulnerabilities, however, could lead to data breaches, privacy concerns, and unauthorized control of devices, threatening the overall CPS network’s integrity.
Understanding Cyber-Physical System (CPS) and Why CPS Security Is Mission-Critical
Cyber Physical Systems (CPS) encompass a broad range of interconnected technologies designed to sense, compute, control, and interact with the physical environment. These systems are critical to industries like energy, healthcare, manufacturing, and transportation, which use CPS for essential services. However, as these systems grow in complexity and connectivity, so do the threats they face. Unlike traditional IT systems, where security focuses on data integrity and confidentiality, CPS security must address the physical consequences of breaches, including operational shutdowns, equipment damage, environmental hazards, and public safety risks.
Current Landscape and Key Drivers in Cyber Physical System (CPS) Security
With CPS forming the backbone of critical infrastructure, these systems are increasingly targeted by cybercriminals for data theft, ransomware attacks, and even political sabotage. The stakes are especially high because a successful CPS attack could cripple essential public services, cause environmental harm, or disrupt critical production processes. Government and private initiatives worldwide are pushing CPS security to the forefront, enforcing regulations and investing in protective measures across domains such as smart cities, utilities, healthcare, agriculture, and public safety.
Key drivers shaping CPS security include:
- Increased Attacks and Threat Sophistication: CPS environments are experiencing a surge in attacks designed to disrupt visibility or control in manufacturing and infrastructure sectors.
- Physical Impact of Attacks: Successful CPS attacks can result in real-world damage and safety risks, which intensifies the need for stringent security measures beyond traditional data protection.
- Regulatory Focus: Governments and industry bodies are recognizing CPS as a national security issue, prompting the development of policies and mandates to establish baseline security protocols.
Gaps in the Gartner Framework and Additional Key Focus Areas
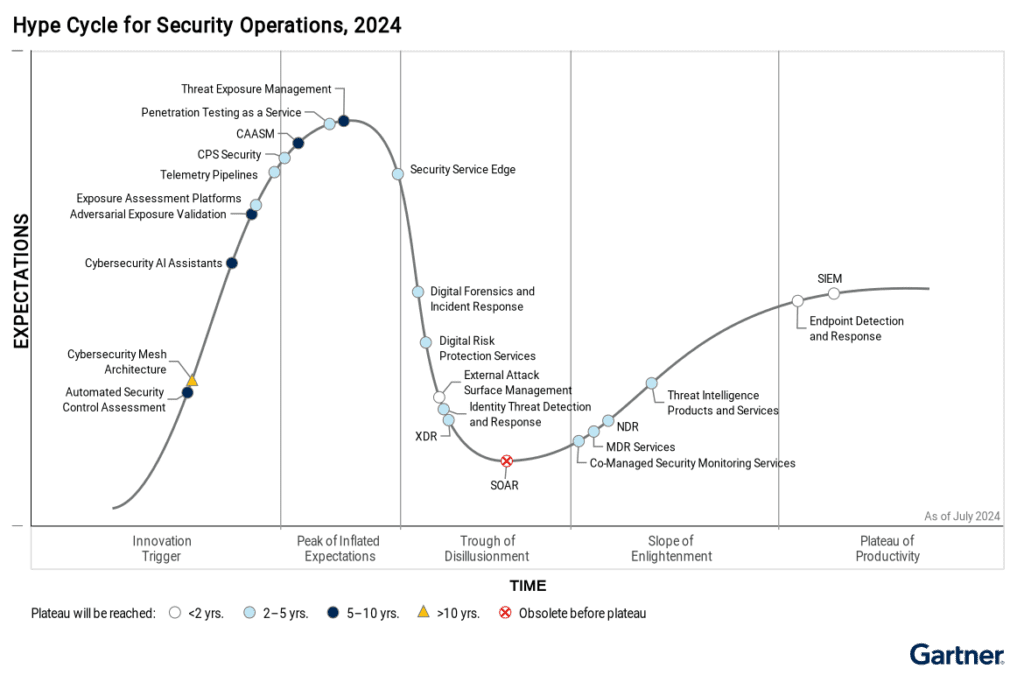
Gartner’s 2024 Hype Cycle provides a solid foundation for understanding the CPS security landscape. However, several critical areas require further exploration to fully address the complexities of CPS. Below are additional dimensions that can strengthen the analysis of CPS security challenges and solutions.
1. Supply Chain Vulnerabilities in CPS
Supply chain security remains a significant concern in CPS environments, where dependencies on third-party hardware, firmware, and software introduce new vulnerabilities. These components often lack visibility and traceability, creating blind spots that attackers can exploit. Implementing a zero-trust architecture across supply chains can mitigate these risks by enforcing strict access controls, continuous monitoring, and comprehensive asset management. Solutions such as Warden offer robust endpoint protection that can help secure critical CPS components across the supply chain.
2. Dark Web Intelligence for CPS Threats
The dark web has become a hub for exchanging exploit kits, attack strategies, and zero-day vulnerabilities targeting CPS. By integrating continuous penetration testing tools like Horizon3.ai’s NodeZero, organizations can gain insights into the latest CPS attack vectors discussed on dark web forums. Using open-source intelligence tools, security teams can proactively address emerging threats and fortify defenses before vulnerabilities are exploited in real-world settings.
3. AI/ML-Driven CPS Threat Detection
Machine learning and artificial intelligence are transforming the capabilities of CPS threat detection. These technologies can quickly identify anomalies within vast CPS environments, distinguishing between normal operations and potential threats with greater precision than traditional monitoring tools. AI-driven solutions are especially valuable in high-traffic environments, such as autonomous vehicles and smart cities, where real-time detection and response are crucial.
4. Resilience in Disaster and Attack Recovery
Resilience is essential for CPS, particularly in mission-critical sectors where downtime can be catastrophic. This involves not only rapid incident response but also the ability to automate recovery protocols. Solutions like Warden’s Default Deny model contribute to operational resilience by preemptively blocking unauthorized access, allowing critical infrastructure to recover and continue operations with minimal disruption.
5. Regulatory and Compliance Mandates for CPS
The regulatory landscape for CPS is evolving, with governments around the world establishing security standards and mandates. In the U.S., entities such as CISA and NIST are setting forth requirements for critical infrastructure protection, pushing for the adoption of continuous testing (e.g., through NodeZero) and endpoint defense (e.g., Warden) to meet compliance standards. Organizations need to be agile in adapting to these regulatory changes to avoid penalties and reduce risks.
Competitive Landscape and Market Trends in CPS Security
The CPS security market is rapidly evolving, driven by the emergence of niche vendors and advanced solutions. Notable vendors include:
- Armis and Claroty: Offering CPS security solutions that focus on visibility and control over OT and IoT devices, they cater to industries with complex, high-risk environments.
- Dragos and Nozomi Networks: Specialize in threat detection and monitoring across critical infrastructure sectors, emphasizing protection for industrial control systems.
- Microsoft: Provides cloud-based cybersecurity solutions tailored for CPS environments, utilizing its extensive cloud ecosystem and AI capabilities.
Warden stands out with its Kernel API Virtualization technology, which mitigates threats by isolating potentially malicious applications and preventing unauthorized actions, thus aligning well with the complex security requirements of CPS. Horizon3.ai’s NodeZero is also a notable player in this space, offering continuous penetration testing capabilities that allow organizations to preemptively identify vulnerabilities in CPS systems.
Social Media and Influencer Insights
Recent CPS security events, such as cyberattacks on critical infrastructure and vulnerabilities in smart cities, have fueled active discussions on social media. Influential posts on LinkedIn and Twitter often focus on case studies, regulatory developments, and emerging solutions in CPS security. Posts that cite real-world incidents and offer actionable insights, such as those from cybersecurity analysts and solution providers, garner significant engagement, indicating a strong interest in understanding CPS security risks.
Noteworthy Content Themes:
- High-Stakes Incidents: Posts about attacks on water treatment facilities, power grids, or transportation systems resonate deeply, as they showcase the tangible consequences of CPS vulnerabilities.
- Case Studies and Success Stories: Successful defenses or mitigations of CPS attacks draw attention, offering practical insights for other organizations facing similar risks.
- Insights into Dark Web Intelligence: Posts or articles discussing the dark web’s role in CPS threats and how continuous penetration testing (like NodeZero) can identify these risks before they become active threats receive high engagement.
Recommendations for a Robust CPS Security Strategy
Organizations aiming to fortify their CPS security should consider the following recommendations:
- Prioritize Secure Procurement Practices: Emphasize security in procurement policies by adopting “secure by design” approaches for CPS components.
- Comprehensive Asset Discovery: Use CPS-specific discovery tools to identify and secure all connected assets, particularly those in mission-critical environments.
- Cross-Functional Collaboration: Foster collaboration between IT, OT, and security teams to break down silos and enable cohesive CPS security efforts.
- Leverage AI and Continuous Testing: Integrate AI-driven detection models and continuous penetration testing solutions like NodeZero to monitor and address vulnerabilities in real-time.
- Engage Business Leaders: Define risk ownership and encourage business leaders to support investments in CPS security for operational resilience.
Conclusion
Cyber-Physical Systems are integral to modern infrastructure, yet they are also increasingly vulnerable to a spectrum of sophisticated threats. By building upon the foundational insights of the 2024 Gartner Hype Cycle and incorporating advanced solutions like Warden and Horizon3.ai’s NodeZero, organizations can address gaps in traditional security frameworks and prepare for emerging risks. As CPS security continues to evolve, the strategies and solutions outlined here will help businesses and governments protect these vital systems, making this analysis an essential resource for stakeholders across the CPS ecosystem.
Through these insights, we aim to equip security professionals with actionable knowledge that safeguards the physical and digital worlds.

Top-11 Questions on Cyber Physical Systems Security
1. What is a Cyber-Physical System (CPS), and how does it function?
A cyber-physical system (CPS) integrates computation, networking, and physical processes. CPS merges cyber components like software and hardware with the physical world, allowing it to sense and interact with physical processes in real-time. CPS often includes embedded computers and networks and uses sensors and actuators to monitor and control the physical environment, effectively creating a feedback loop between the digital and physical realms.
2. How are CPS and IoT different, and how do they complement each other?
While both CPS and the Internet of Things (IoT) involve networked systems that interact with the physical world, CPS typically features tighter integration between computation and physical elements and often serves more critical, complex functions, such as in medical devices and control systems for national infrastructure. CPS and IoT can complement each other, with CPS providing critical cyber and physical control and IoT contributing data from numerous IoT devices distributed in the physical environment. Together, they provide powerful solutions across sectors like industry 4.0, healthcare, and smart cities.
3. What are the key applications of Cyber-Physical Systems (CPS)?
Applications of cyber-physical systems span multiple domains:
- Industrial Control Systems (ICS) for automated production.
- Smart Grids for energy management.
- Autonomous vehicles in transportation.
- Healthcare, through medical devices and systems monitoring. These types of CPS are embedded across various industries, enabling automation and real-time decision-making in scenarios where physical processes directly interact with computational elements.
4. How does CPS enhance control systems across industries?
CPS integrates the dynamics of control systems and allows operators to monitor and control the physical processes in a real-time and precise manner. By combining sensing and control systems, CPS enables advancements in process control systems in sectors like manufacturing, agriculture, and public safety. This integration means that physical processes affect computations and vice versa, allowing for efficient control and robust feedback mechanisms that enhance reliability and efficiency in various industries.
5. What are some examples of cyber-physical systems?
Examples of CPS include smart grids, which use real-time data to optimize power distribution; autonomous vehicles that rely on sensor-driven computation to navigate; and medical devices like insulin pumps that automatically adjust dosage based on sensor input. Other examples of CPS can be found in defense systems, robotic manufacturing, and smart cities, where CPS control the physical and cyber world to improve safety, efficiency, and sustainability.
6. How does CPS security differ from traditional cybersecurity?
CPS security involves protecting both cyber and physical elements within a system. Since CPS components interact directly with the physical world, security teams must address not only cyber threats but also physical security vulnerabilities. Cyber-physical systems security requires specialized measures to protect against threats that could lead to physical impacts, making the security posture of CPS unique compared to traditional cybersecurity.
7. What are the new challenges posed by CPS?
CPS presents new challenges because they require feedback loops where physical processes affect computations, making them sensitive to both digital and physical disruptions. Issues like system design, cyber and physical risks, and interoperability among networked systems create complexities in CPS. Additionally, the need to protect CPS from cyber threats without compromising their performance or physical security adds to these challenges.
8. How are CPS systems used in critical infrastructure?
In critical sectors like power systems, water treatment, and healthcare, CPS devices and systems play a crucial role by providing reliable, real-time monitoring and control. These critical CPS systems are engineered for resilience and network security, as any disruption could have severe consequences on public safety and economic stability. They form part of management systems that control essential services, ensuring consistent and reliable operations.
9. How does the Department of Homeland Security (DHS) protect CPS?
The Department of Homeland Security (DHS) and other regulatory bodies focus on protecting critical CPS by setting standards, issuing best practices, and coordinating with industry partners to fortify cyber physical systems security. DHS emphasizes collaboration to safeguard CPS from both cyber and physical threats, ensuring that cyber and physical components remain resilient against vulnerabilities that could impact national security and essential infrastructure.
10. What role does the National Science Foundation (NSF) play in advancing CPS?
The National Science Foundation (NSF) funds research into cyber-physical systems to support advancements in system design, embedded systems, and computational and physical elements integration. NSF grants facilitate the development of next-generation cyber-physical system architecture and contribute to innovations in sectors like industry 4.0 and autonomous systems, helping the U.S. remain at the forefront of CPS development and cyber-physical systems security.
11. What is the future of CPS, and how does it impact society?
As CPS continues to evolve, the economic and societal potential of such systems is expected to grow substantially. CPS advancements will enable more autonomous, interconnected engineered systems, influencing daily life through smarter infrastructure, safer transportation, and more efficient physical processes. The growth of CPS will drive the societal potential of such systems, creating opportunities across industries and raising the need for innovative CPS protection platforms and security frameworks.





