How the 1.1 TB Disney Slack Data Breach Could Have Been Prevented with Warden and NodeZero
Earlier this year, attackers stole 1.1 terabytes of data from Disney by exploiting vulnerabilities in their Slack infrastructure. This incident highlights significant concerns about Slack as an attack vector, especially for security-minded CEOs and organizations using Slack. Below, we’ll examine the attack path step-by-step, showcase how this threat could impact any organization, and explain how Warden and NodeZero could mitigate and prevent such data breach risks.

Why Slack Is a Dangerous Attack Vector
Slack’s ubiquity and convenience come with security trade-offs:
File Sharing Risks: Employees often share sensitive files such as keystores, financial documents, and credentials. These files are effectively stored in a shared drive within the Slack workspace.
Access to Sensitive Conversations: Slack’s search feature allows anyone with workspace access to retrieve sensitive company information.
Implicit Trust in Links: Users often trust links shared within Slack, making lateral phishing attacks highly effective.
While Multi-Factor Authentication (MFA) provides a baseline defense, Horizon3.ai’s research revealed a critical vulnerability: an attacker could extract post-MFA authentication tokens from the Slack Desktop App. With these tokens, attackers could impersonate a legitimate user and gain access to the entire Slack workspace creating a data breach.
Real-World Attack Path
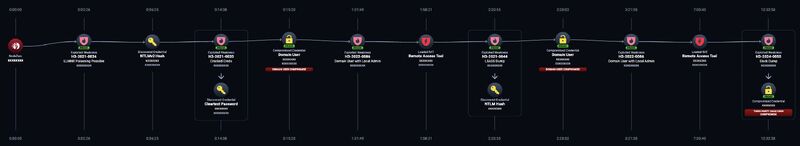
The Horizon3.ai NodeZero team replicated a real-world attack path during an internal pentest:
Harvesting NTLM Hashes: The attackers began with no authentication and used a man-in-the-middle technique to capture NTLM hashes.
Cracking NTLM Hashes: They cracked the hashes to uncover plaintext passwords.
Gaining Endpoint Access: Using the cracked credentials, the attackers logged into an endpoint.
Escalating Privileges: The compromised domain user had local admin rights on the endpoint.
Installing a Remote Access Trojan (RAT): A RAT was deployed on Host 1, enabling the dumping of OS credentials (LSASS).
Laterally Moving to Host 2: Using harvested credentials, the attackers gained access to another machine and deployed a second RAT.
Extracting Slack Tokens: The RAT on Host 2 extracted Slack authentication tokens from the process memory of the Slack Desktop App.
Compromising Slack: With the stolen token, the attackers gained unauthorized access to Slack, potentially stealing sensitive files, conversations, and links.
Key Points:
The attack path exploited misconfigurations and post-exploitation tactics, not CVEs.
No human involvement was required during the attack—it was fully autonomous.
Traditional vulnerability scanners would not detect this attack.
Mitigating the Slack Data Breach Risk with Warden
Warden’s advanced capabilities, such as Default Deny Technology and Kernel API Virtualization, could have prevented multiple stages of this attack path:
-
Prevention of RAT Deployment:
-
Warden’s Default Deny approach ensures that only pre-approved applications and executables can run. This would have blocked the installation of the RAT on both Host 1 and Host 2.
-
-
Blocking Lateral Movement:
-
Kernel API Virtualization isolates processes and prevents malicious actors from exploiting credentials to move laterally between endpoints.
-
-
Protecting Slack Authentication Tokens:
-
Warden’s memory protection features shield sensitive application data, such as Slack tokens, from being accessed or exfiltrated by malicious processes.
-
-
Real-Time Threat Detection:
-
Warden continuously monitors endpoint activity for unusual behavior, such as unauthorized access to process memory, enabling immediate response to such attack attempts.
-
Identifying Data Security and Cyber Risks with NodeZero
NodeZero, an autonomous pentesting platform, excels at uncovering hidden vulnerabilities and attack paths. Here’s how NodeZero could proactively identify and mitigate this Slack-related breach risks:
-
Simulating Real-World Threats: NodeZero replicates the attacker’s methods by dynamically discovering vulnerabilities and misconfigurations in your environment.
-
Validating Slack Token Exposure: NodeZero could identify the extraction vulnerability in the Slack Desktop App, providing clear proof-of-concept (POC) evidence to guide remediation efforts.
-
Mapping Lateral Movement Risks: By simulating credential theft and lateral movement, NodeZero helps organizations understand how attackers could traverse their network.
-
Actionable Remediation Guidance: NodeZero provides a prioritized list of mitigations, such as enforcing least privilege on endpoints, implementing stronger network segmentation, and protecting sensitive application processes.
Step-by-Step Slack Breach Attack Prevention Workflow
-
Deploy NodeZero: Conduct a pentest to identify risks, including the Slack token vulnerability, misconfigurations, and privilege escalation paths.
-
Implement Warden: Configure Warden’s Default Deny policies and Kernel API Virtualization to block unauthorized applications, memory access, and lateral movement.
-
Harden Slack Security:
-
Limit file sharing permissions within Slack.
-
Implement granular workspace access controls.
-
Educate employees on phishing risks and suspicious link handling.
-
-
Monitor and Respond: Use Warden’s real-time monitoring to detect and mitigate threats before they escalate.
Why Traditional Vulnerability Management Falls Short
This incident underscores the limitations of traditional vulnerability scanners. Since no CVEs were exploited, a scanner would fail to identify the risks associated with this attack. Warden’s proactive endpoint defense and NodeZero’s autonomous pentesting capabilities provide a more comprehensive approach to identifying and mitigating advanced threats.
Conclusion Slack Channel, Workspace and How to Protect Your Slack for Security Teams
The Disney data breach demonstrates the importance of securing collaboration tools like Slack. While Slack’s ease of use is an asset, it can also become a significant liability if not properly protected. By leveraging Warden and NodeZero, organizations can:
-
Proactively identify vulnerabilities.
-
Block attack paths.
-
Prevent sensitive data exfiltration.
With these tools in place, businesses can confidently embrace the benefits of collaboration tools without exposing themselves to unnecessary data exfil or breach risks.

Slack Channel Protection with Warden and NodeZero: Comprehensive Answers to Top Questions with Best Practices
1. How can attackers exploit Slack vulnerabilities?
Attackers can exploit Slack by stealing authentication tokens, accessing sensitive files, and phishing users with malicious links. The Disney breach highlights how attackers used post-MFA Slack tokens to gain workspace access.
2. How does Warden prevent unauthorized access to Slack?
Warden’s Default Deny Technology ensures that only authorized processes can interact with Slack, blocking RAT installation or token exfiltration. Kernel API Virtualization isolates processes, preventing malicious interactions.
Securing Slack’s Local Data Storage and Processes
Warden prevents unauthorized access to Slack’s local data storage by encrypting sensitive application data. Its process isolation ensures that only trusted applications can interact with Slack, blocking any attempts by malicious software to access or modify files.
3. How can NodeZero uncover Slack-specific risks?
NodeZero can simulate attacker methods like extracting Slack tokens, testing permissions, and mapping lateral movement risks. It identifies misconfigurations and provides actionable remediation.
Evaluating API Tokens and Bots
NodeZero tests Slack’s API tokens for excessive permissions and identifies vulnerabilities in bot integrations that could expose sensitive data. For example, it verifies whether bots have unnecessary access to private channels or workspace-wide permissions.
4. What are best practices for securing Slack workspaces?
Slack security can be improved by limiting file-sharing permissions, implementing granular access controls, and educating employees on phishing risks.
Comprehensive Best Practices Checklist
Best practices for Slack security include:
Disabling public file links to reduce data exposure risks.
Reviewing third-party app integrations regularly.
Implementing session expiration policies for all users.
Enforcing least privilege access to sensitive Slack channels.
5. How can organizations prevent Slack data breaches?
Warden blocks key stages of the attack, including RAT installation and lateral movement. NodeZero proactively identifies vulnerabilities that attackers could exploit.
Post-Breach Response with Warden and NodeZero
In the event of a breach, Warden immediately isolates affected endpoints, preventing attackers from expanding their reach. NodeZero analyzes attack paths to identify weaknesses and prioritize remediation, ensuring long-term security improvements.
6. Can Warden protect against insider threats in Slack?
Warden’s behavioral monitoring can detect unusual Slack activity, such as large file downloads or unauthorized deletions. This helps mitigate insider threats.
Insider Threat Scenarios
Warden’s behavioral monitoring detects suspicious Slack activity, such as employees sharing sensitive files with unauthorized users or mass-deleting messages. Alerts are generated for unusual patterns, enabling immediate investigation and mitigation.
7. What steps can organizations take to secure Slack file sharing?
Organizations should limit file-sharing permissions, educate users on sensitive data risks, and use NodeZero to simulate file-sharing vulnerabilities. Warden prevents unauthorized file uploads or downloads.
8. How can phishing links shared on Slack be mitigated?
Warden’s web filtering blocks malicious links shared on Slack, and NodeZero can simulate phishing attempts to evaluate employee awareness.
Phishing Simulation Workflows
NodeZero provides targeted phishing simulations to measure employee susceptibility to Slack-based phishing links. Warden enforces real-time link security, analyzing URLs before users access them.
9. How can organizations protect Slack tokens from being stolen?
Warden shields Slack tokens in process memory, preventing malicious processes from accessing or exfiltrating them. NodeZero validates token security by simulating extraction attempts.
10. Does Warden protect Slack from API exploitation or misconfigured apps?
Warden monitors and isolates Slack integrations, preventing data leaks through malicious or poorly configured apps. It also ensures that API interactions adhere to security policies.
Detecting Malicious App Behavior
Warden analyzes app behavior in real-time to identify and block unauthorized data access or sharing. By monitoring API usage, Warden ensures only legitimate requests are processed.
11. What are the limitations of traditional Slack security measures?
Slack’s built-in measures, like MFA, don’t prevent token theft or address vulnerabilities in app integrations. Traditional vulnerability scanners fail to detect non-CVE-based attacks. Warden and NodeZero provide deeper, proactive defense.





